Category: Best Practices for Merchants
October 15th, 2014 by Elma Jane
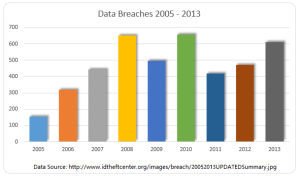
Another day, another corporate data breach. Business owners are now aware that cyber criminals are becoming increasingly smart and sophisticated in their hacking methods, and they can target just about anyone. But smaller companies that think, It can’t happen, or they are too small for hackers to notice, may be setting themselves up for a devastating data breach.
Large corporations typically have a lot more money and resources to invest in IT security, whereas small to medium businesses do not have the IT staffing, resources, money or know-how to put effective security measures into place to combat security vulnerabilities.
If a small business owner is responsible for security practices, it’s going to fall to the lower end of the priority list. The business will have less protections in place and hackers recognize that. Criminals are looking for unlocked doors.
Recent research found that more than half of all small and midsize businesses have been hacked at some point, and nearly three-quarters weren’t able to restore all the lost data. The two most common methods of attack are phishing, gathering sensitive information by masquerading as a trusted website and watering holes. Installing malware on commonly used websites of a target group. These tactics, grant cyber criminals access to the information that leads to identity theft and stolen credit card information.
A credit card breach is fairly easy to recognize once customers of a certain company all begin reporting fraudulent charges. But by that point, a breach has already done a significant amount of damage, not just to the consumers but to the company they trusted to protect their data.
A computer that appears to have been tampered with.If you turned off your computer when you left work and it’s on or has windows and programs running when you return, someone may have been trying to steal important information. This is an especially likely scenario with internal data theft, such as the AT&T breach. Keeping your machines password-protected and encrypting any sensitive data can prevent unauthorized individuals from accessing the information.
Locked-out accounts. If you’ve ever been locked out of your email or social media accounts, you know it’s usually because you typed the wrong login credentials one too many times. If you receive a lock-out message the first time you try to access an account (and you know you’ve typed your password correctly), you might have been hacked. This can mean that someone is attempting to brute force an account, or that an account has already been compromised and the password changed.
Unusually slow Internet or computers. This could be a sign of a compromised machine that is sending out lots of traffic, or that malware or a virus is on the machine. You should also look for pop-up ads (especially if you have an activated blocker) or websites that don’t load properly.
In all of these instances, minor inconveniences that most people might ignore if the problem seems to resolve itself could be signs of a much more serious problem. Both experts advised keeping your antivirus software, firewalls and device operating systems up-to-date, and always remaining alert for any suspicious activity.
Posted in Best Practices for Merchants Tagged with: consumers, credit card breach, credit card information, customers, data, data breach, device, Security, website
October 13th, 2014 by Elma Jane
Non-cash payments volumes are expected to increase by nearly 10% percent to reach 366 billion transactions in 2013, fueled by strong growth in developing markets and mobile payments.
Overall, more than half of global non-cash payment growth comes from developing countries despite them only making up one quarter of the market size at 93 billion transactions. China remains a relatively underdeveloped market for non-cash transactions but its population and growth rate suggest in certain conditions that it could soon outstrip the US and Euro-zone within the next five years.
China is one to watch over the coming years, with the report showing that if growth rates remain at the current high level, it could become the largest market for non-cash transactions within just five years. These soaring growth rates in key markets put pressure on the global payments arena to innovate to meet rapidly increasing consumer demand.
Increased use of tablets and smartphones is creating a convergence of e- and m- payments, posing new challenges for Payments Services Providers (PSPs). In 2015, m-payments are projected to grow at 60.8% while e-payments growth is forecast to decelerate to 15.9% annually over the next year, as more people use mobile devices to make payments.
This trend is adding to the pressure on PSPs to modernize their payments processing infrastructures, ideally based around a single integrated payments platform for corporate and retail payments and a central hub.
The growth of the industry coupled with the fast pace of new regulation requires flexibility from PSPs to adapt, initiatives such as real-time payments, pressure on card interchange fees and improved payments governance as examples of cascading regulation.
Posted in Best Practices for Merchants Tagged with: card, card interchange fees, consumer, e-payments, global payments, m-payments, Mobile Devices, Mobile Payments, Non-cash payments, payments platform, payments processing, Payments Services Providers, psps, real-time payments, retail payments, Smartphones, tablets, transactions
October 9th, 2014 by Elma Jane

This 300-year-old coin around my neck. It was off of a Spanish Shipwreck known as the Shipwreck of 1715. When I first saw it, I noticed a little hole with a speck of a diamond. I questioned the jeweler about it, why would you drill a hole in a 300-year-old coin and damage this 300-year-old treasure? The jeweler preceded to tell me that it was a 300-year-old hole.
Think about how we used currency 300 years ago. There were no banks, no financial institutions to hold merchants money. So if I had a bunch of money, I had it on a wire or had it in a box. I may have kept my money in my mattress. People would keep their money on a wire, punch holes in the coins, string the money through the wire and then go back to business on their horse and buggy, or however they got from point-to-point 300 years ago. If you have ever heard a phrase that the business owner started his business on a shoe string, you now know where the phrase originated.
What I found amazing in this one coin that I wear is that, It has thousands of transactions in its history. Who knows what was bought and sold with this very coin? Whether it was goats or chickens, a piece of property somewhere, or a boat ride to the states, or whatever it might be. There is no documented history behind each one of those transactions.
Today, when National Transaction processes a transaction for a merchant, we know the date and time. We know the amount of sale, we probably know the email address and the owner zip code, we actually know quite about the information around that transaction.
Many articles are written that answer the who, what, when, where and why questions with today’s electronic transactions. We have four of the five answers. We know who, what, when and where. The only thing that we don’t know is why the customer bought the item.
If this coin had today’s technologies there would have been thousands of transactions that this coin could have shared. The story of those purchases would be fascinating.
All business owners wants to make a sale. Each time they do make a sale, we recommend capturing any and all contact information. This customer is a buyer! Today, most people have an email address or cell phone number. If we don’t capture the customer’s information we have just ignored the single most important thing in any business’s life cycle: the customer.
Posted in Best Practices for Merchants Tagged with: banks, business owner, currency, customer, financial institutions, Merchant's, purchases, transactions
October 8th, 2014 by Elma Jane
When the PCI Security Standards Council (PCI SSC) launched PCI DSS v3.0 in January 2014, businesses were given one year to implement the updated global standard. Now that the deadline is fast approaching, interest is picking up in what v3.0 entails. On Jan. 1, 2015, version 3.0 of the Payment Card Industry (PCI) Data Security Standard (DSS) will reach year one of its three-year lifecycle.
Trustwave, a global data security firm, is on the frontlines of helping secure the networks of merchants and other businesses on the electronic payments value chain against data breaches. As an approved scanning vendor, Trustwave is used by businesses to achieve and validate PCI DSS compliance.
PCI DSS v3.0 is business as usual for the most part, except for a few changes from v2.0 that considers impactful for large swaths of merchants. The top three changes involve e-commerce businesses that redirect consumers to third-party payment providers. The expansion of penetration testing requirements and the data security responsibilities of third-party service providers.
Penetration testing
Penetration testing is the way in which merchants can assess the security of their networks by pretending to be hackers and probing networks for weaknesses. V3.0 of the PCI DSS mandates that merchants follow a formal methodology in conducting penetration tests, and that the methodology goes well beyond what merchants can accomplish using off-the-shelf penetration testing software solutions.
Merchants that are self assessing and using such software are going to be surprised by the rigorous new methodology they are now expected to follow.
Additionally, penetration testing requirements in v3.0 raises the compliance bar for small merchants who self assess. Those merchants could lower the scope of their compliance responsibilities by segmenting their networks, which essentially walls off data-sensitive areas of networks from the larger network. In this way merchants could reduce their compliance burdens and not have to undergo penetration testing.
Not so in v3.0. If you do something to try to reduce the scope of the PCI DSS to your systems, you now need to perform a penetration test to prove that those boundaries are in fact rigid.
Redirecting merchants
The new redirect mandate as affecting some, but not all, e-commerce merchants that redirect customers, typically when they are ready to pay for online purchases to a third party to collect payment details. If you are a customer and you are going to a website and you add something to your shopping cart, when it comes time to enter in your credit card, this redirect says I’m going to send you off to this third party.
The redirect can come in several forms. It can be a direct link from the e-commerce merchant’s website to another website, such as in a PayPal Inc. scenario, or it can be done more silently.
An example of the silent method is the use of an iframe, HTML code used to display one website within another website. Real Estate on the merchant’s website is used by the third-party in such a way that consumers don’t even know that the payment details they input are being collected and processed, not by the e-commerce site, but by the third party.
Another redirect strategy is accomplished via pop-up windows for the collection of payments in such environments as online or mobile games. In-game pop-up windows are typically used to get gamers to pay a little money to purchase an enhancement to their gaming avatars or advance to the next level of game activity.
For merchants that employ these types of redirect strategies, PCI DSS v3.0 makes compliance much more complicated. In v2.0, such merchants that opted to take Self Assessment Questionnaires (SAQs), in lieu of undergoing on-site data security assessments, had to fill out the shortest of the eight SAQs. But in v3.0, such redirect merchants have to take the second longest SAQ, which entails over 100 security controls.
The PCI SSC made this change because of the steady uptick in the number and severity of e-commerce breaches, with hackers zeroing in on exploiting weaknesses in redirect strategies to steal cardholder data. Also, redirecting merchants may be putting themselves into greater data breach jeopardy when they believe that third-party payment providers on the receiving end of redirects are reducing merchants’ compliance responsibilities, when that may not, in fact, be the case.
Service providers
Service provider is any entity that stores, processes or transmits payment card data. Examples include gateways, web hosting companies, back-up facilities and call centers. The update to the standard directs service providers to clearly articulate in writing which PCI requirements they are addressing and what areas of the PCI DSS is the responsibility of merchants.
A web hosting company may tell a merchant that the hosting company is PCI compliant. The merchant thought, they have nothing left to do. The reality is there is still always something a merchant needs to do, they just didn’t always recognize what that was.
In v3.0, service providers, specifically value-added resellers (VARs), also need to assign unique passwords, as well as employ two-factor authentication, to each of their merchants in order to remotely access the networks of those merchants. VARs often employ weak passwords or use one password to access multiple networks, which makes it easier for fraudsters to breach multiple systems.
The PCI SSC is trying to at least make it more difficult for the bad guys to break into one site and then move to the hub, so to speak, and then go to all the other different spokes with the same attack.
Overall, v3.0 is more granular by more accurately matching appropriate security controls to specific types of merchants, even though the approach may add complexity to merchants’ compliance obligations. On the whole a lot of these changes are very positive.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: (PCI SSC), call centers, cardholder data, consumers, credit-card, customers, data breaches, data security assessments, Data Security Standard, e-commerce breaches, e-commerce businesses, e-commerce merchant's website, electronic payments, global data security, global standard, Merchant's, merchant’s website, mobile, networks, payment, payment card data, Payment Card Industry, payment providers, PCI Security Standards Council, PCI-DSS, Penetration testing, Service providers, shopping cart, software solutions, web hosting, website
October 1st, 2014 by Elma Jane
Approximately $350 billion in housing rent is written out on checks or given in cash annually and until now more than 90 million renters in the U.S. didn’t have an option to use their credit or debit card to pay their rent. RadPad wants to be that option. The service works by allowing users to sign up and link their debit or credit card to their account, then asks for the Landlords mailing address and email, which presumably allows to mail the check to the Landlord. By saving the payments to the customers RadPad profile, Renters Can conceivably improve their credit score. Moreover, it allows roommates or others who split rent to pay communally. They can get both terms to go mainstream by letting people pay their rent by phone.
Posted in Best Practices for Merchants, Mobile Payments Tagged with: card, cash, checks, credit, credit score, customers, debit, debit card, email, housing rent, payments, phone, renters
September 30th, 2014 by Elma Jane
Email remains king in the types of digital marketing businesses. Fifty four percent of businesses view email as the most effective form of Internet marketing. However, a number of other types of digital marketing tactics aren’t far behind. More than 40 percent of the businesses surveyed believe optimized websites and blogs, search engine optimization (SEO) and social media are among the most successful online marketing tactics. Mobile marketing and e-commerce marketing are viewed as the least effective forms.
Contributing to email marketing’s success is the ease in which it is conducted. Eleven percent of the businesses surveyed thought email was one of the most difficult types of digital marketing to execute. Social media tops the list, with nearly 50 percent of businesses saying it was the hardest to accomplish.Content marketing and SEO were among the other toughest tactics to execute. Overall, the vast majority of businesses using some form of digital marketing report seeing positive results from it.
Businesses have a wide range of motives for using Internet marketing. Wanting to increase customer engagement, sales revenue, leads for their sales teams and brand awareness were the most important reasons. Reducing marketing and customer service costs are surprisingly least important. Majority of the businesses believe their digital marketing efforts are only getting better. In order to achieve all of their goals, there are a number of challenges businesses are facing:
The most challenging obstacle to success is clearly the lack of an effective digital marketing strategy.
Followed by an inadequate budget to fund programs.
Other challenges business must overcome to achieve better digital marketing results include a lack of training and expertise.
Inability to prove a return on investment and increasing competition.
Posted in Best Practices for Merchants, e-commerce & m-commerce Tagged with: Content marketing, customer service, digital marketing, digital marketing businesses, e-commerce marketing, email, Internet marketing, Mobile marketing, search engine optimization, SEO, social media, websites
September 29th, 2014 by Elma Jane
If your retail business products sells only in-store, then you’re falling behind. Consumers in the digital age expect options when they shop, and if you’re not offering those choices, your customers may pass you by for a more tech-savvy competitor. Consumers go into stores, evaluate products and buy online, or research online and go into the store for purchase. The two worlds have merged, if you’re not covering both spectrums, you’re missing out.
Recent research by UPS showing 40 percent of today’s shoppers use a combination of online and in-store interactions to complete their purchases. The days of physical stores being separated from online shopping are over. They’re no longer channels that are happening on their own. The UPS survey found that a large chunk of online shoppers cross channels during their shopping path. Be present on both channels and take advantage of that.
It’s not always possible or economic for an online-only retailer to open up a physical storefront, but existing brick-and-mortar stores or wholesalers can easily introduce an e-commerce component to their sales to expand their customer reach. Online sales help reach consumers that may not otherwise be able to purchase your products. Even if your company’s main focus is creating a personalized in-store experience, there are still ways to capture the online shopper market. In addition to giving consumers a way to research your products before coming in-store to purchase your offerings, you can offer people a way to conveniently buy items they already know they want.
For all the advantages a multi-channel sales strategy can give a retailer, there are still some challenges to this approach. Managing inventory versus cash flow and ensuring even demand on both channels have been company’s two greatest challenges in balancing in-store and online sales. Creating demand is how companies set themselves apart from competition. The secret sauce. The challenge is making sure that retail operations have a turnover ratio that works for the shipping schedules from the main warehouse. This isn’t a problem for e-commerce businesses, because product can be packaged and shipped as fast as it gets produced. But an omnichannel company has to take retail and e-commerce into account when stocking a warehouse.
There are a few different strategies retailers can use to help keep their sales operations well-balanced. Offering different items online versus in-store, to avoid inventory competition (i.e., selling seasonal or discontinued items online and current items in-store). Requiring a minimum order for online purchases or grouping products together rather than selling them individually to make e-commerce more worth your while.
The best way to balance a multi-channel sales strategy is to take a unified view of consumers online and offline by connecting their on- and offline behaviors via technology. Some of the retailers questions have is how to connect a person offline with what they buy online, how to recognize who they are in the store and know what they look at on your website, because people are switching back and forth. Link behaviors online with a unique ID through email or a mobile app, since 66% of customers use smartphones in-store.
Even if your business can’t actually sell and ship products via e-commerce,it’s still important to be in tune and up-to-date with the way customers want to interact with you on the Web. People are on the go, researching on phones and tablets. If you’re not savvy to what’s happening out there and don’t have the best-in-class SEO, you’ll miss out. You still need to engage in the digital world, even if it’s not always obvious.
Posted in Best Practices for Merchants, e-commerce & m-commerce Tagged with: brick and mortar, business products, consumers, customers, digital world, e-commerce, email, mobile app, multi-channel sales, online and in-store, online shoppers, online shopping, phones, products, retail business, SEO, shoppers, Smartphones, tablets, web
September 24th, 2014 by Elma Jane
The CVV Number (Card Verification Value) on your credit card or debit card is a 3 digit number on VISA, MasterCard and Discover branded credit and debit cards. On your American Express branded credit or debit card it is a 4 digit numeric code.
The codes have different names:
American Express – CID or unique card code.
Debit Card – CSC or card security code.
Discover – card identification number (CID)
Master Card – card validation code (CVC2)
Visa – card verification value (CVV2)
CVV numbers are NOT your card’s secret PIN (Personal Identification Number).
You should never enter your PIN number when asked to provide your CVV. (PIN numbers allow you to use your credit or debit card at an ATM or when making an in-person purchase with your debit card or a cash advance with any credit card.)
Types of security codes:
CVC1 or CVV1, is encoded on track-2 of the magnetic stripe of the card and used for card present transactions. The purpose of the code is to verify that a payment card is actually in the hand of the merchant. This code is automatically retrieved when the magnetic stripe of a card is swiped on a point-of-sale (card present) device and is verified by the issuer. A limitation is that if the entire card has been duplicated and the magnetic stripe copied, then the code is still valid.
The most cited, is CVV2 or CVC2. This code is often sought by merchants for card not present transactions occurring by mail or fax or over the telephone or Internet. In some countries in Western Europe, card issuers require a merchant to obtain the code when the cardholder is not present in person.
Contactless card and chip cards may supply their own codes generated electronically, such as iCVV or Dynamic CVV.
Code Location:
The card security code is typically the last three or four digits printed, not embossed like the card number, on the signature strip on the back of the card. On American Express cards, the card security code is the four digits printed (not embossed) on the front towards the right. The card security code is not encoded on the magnetic stripe but is printed flat.
American Express cards have a four-digit code printed on the front side of the card above the number.
MasterCard, Visa, Diners Club, Discover, and JCB credit and debit cards have a three-digit card security code. The code is the final group of numbers printed on the back signature panel of the card.
New North American MasterCard and Visa cards feature the code in a separate panel to the right of the signature strip. This has been done to prevent overwriting of the numbers by signing the card.
Benefits when it comes to security:
As a security measure, merchants who require the CVV2 for card not present payment card transactions are required by the card issuer not to store the CVV2 once the individual transaction is authorized and completed. This way, if a database of transactions is compromised, the CVV2 is not included, and the stolen card numbers are less useful. Virtual Terminals and payment gateways do not store the CVV2 code, therefore employees and customer service representatives with access to these web-based payment interfaces who otherwise have access to complete card numbers, expiration dates, and other information still lack the CVV2 code.
The Payment Card Industry Data Security Standard (PCI DSS) also prohibits the storage of CSC (and other sensitive authorization data) post transaction authorization. This applies globally to anyone who stores, processes or transmits card holder data. Since the CSC is not contained on the magnetic stripe of the card, it is not typically included in the transaction when the card is used face to face at a merchant. However, some merchants in North America require the code. For American Express cards, this has been an invariable practice (for card not present transactions) in European Union (EU) states like Ireland and the United Kingdom since the start of 2005. This provides a level of protection to the bank/cardholder, in that a fraudulent merchant or employee cannot simply capture the magnetic stripe details of a card and use them later for card not present purchases over the phone, mail order or Internet. To do this, a merchant or its employee would also have to note the CVV2 visually and record it, which is more likely to arouse the cardholder’s suspicion.
Supplying the CSC code in a transaction is intended to verify that the customer has the card in their possession. Knowledge of the code proves that the customer has seen the card, or has seen a record made by somebody who saw the card.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale, Visa MasterCard American Express Tagged with: (Card Verification Value), (CVC2), American Express, atm, authorization data, bank/cardholder, card holder data, card identification number, card issuers, Card Not Present transactions, card number, card numbers, card security code, card validation code, card-not-present, card-present transactions, cardholder, cards, cash advance, chip cards, CID, code, Contactless card, credit, credit-card, CSC, customer, customer service, CVC1, CVV Number, CVV1, CVV2, Data Security Standard, debit, debit card, debit cards, device, Diners Club, Discover, fax, gateways, iCVV or Dynamic CVV, individual transaction, internet, issuer, JCB credit, magnetic stripe, mail, MasterCard, merchant, payment card, Payment Card Industry, payment card transactions, payment gateways, PCI-DSS, Personal Identification Number, PIN, point of sale, post transaction authorization, security codes, telephone, terminals, unique card code, virtual terminals, visa, web-based payment
September 23rd, 2014 by Elma Jane
Home Depot, US retail chain says that 56 million payment cards are at risk following a malware-laden cyber-attack on eftpos tills across its stores in the US and Canada.
The investigation into a possible breach began on September 2nd,Tuesday morning, immediately after Home Depot received reports from its banking partners and law enforcement that criminals may have breached its systems.
According to Home Depot’s security partners, the malware had not been seen previously in other attacks.
Criminals used unique, custom-built malware to evade detection. The cyber-attack is estimated to have put payment card information at risk for approximately 56 million unique payment cards, after lurking in the company’s eftpos tills for four months between April and September.
While the breach has been seen as a further proof-point in the US push to adopt Chip and PIN at the point-of-sale, the fact that the outbreak also hit the home improvement chain’s Canadian stores, where the EMV standard has been implemented, leaves pause for thought. Nonetheless, the retailer has committed to installing 85,000 PIN pads at its US outlets, well ahead of the national 2015 deadline.
Home Depot has set aside $65 million to cover the cost to investigate the data breach, provide credit monitoring services to its customers, increase call center staffing, and pay legal and professional services. Approximately $27 million of the projected outlay will be covered by the company’s insurance.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale Tagged with: banking partners, Breach, call center, card information, cards, Chip and PIN, credit monitoring, credit monitoring services, customers, cyber-attack, data breach, EMV, EMV standard, Malware, payment, payment card information, payment cards, PIN pads, point of sale, risk
September 22nd, 2014 by Elma Jane
Consumers know how hard it is to obtain a credit card, if your credit score isn’t up to par. A bad credit score can prevent you from getting credit and make it hard to purchase your day to day necessities. People with poor credit don’t know their options. There are a number of ways to get a credit card if you have a poor credit score. There will likely be road blocks and limitations in your search. You won’t have the same options available as someone with pristine credit. But you will be able to get a line of credit if you look in the right place.
COSIGNED CREDIT CARDS If you get a cosigner, you will be able to obtain a card that would not be available to you otherwise. The cosigner has to have good credit, and they are responsible for your debt if you can’t pay. Make sure your cosigner fully recognizes their obligations and what will happen if you are unable to pay.
GIVE AN EXPLANATION FOR POOR CREDIT Explain the circumstances behind your poor credit. You can add a 100-word statement to your credit report such as the loss of a job. If you can tell your story and convince creditors you are on the road to increasing your credit score, they may believe you are more likely to pay back your debts. Divorce and illness are two other instances where individuals may see a drop in their credit score. Make sure whatever you list is true.
IMPROVE YOUR CREDIT One of the most difficult options. Poor credit can seem extremely hard to repair. But there are choices, it is just a process that will take a significant period of time. If you have poor credit, you can open bank accounts and pay off your loans and credit cards on time. If you pay off your debt in a timely manner, your credit score will improve over time and you will gain access to more credit card options.
RETAIL STORE CARDS Retail stores often have store credit cards they offer customers. Retail stores are generally more willing to approve applicants without a stellar credit score. But these cards usually come with extremely high interest rates and relatively low credit limits, so make sure you fully understand the terms of the card before applying.
SECURED CREDIT CARDS You deposit some money into an account, and then a creditor will provide you with a line of credit equal to your deposit. It is essentially a down payment, and if you don’t pay your credit card bill, your creditor is entitled to the money in the account. This might not sound like a favorable position, but remember that secured credit cards can be used as a valuable tool to rebuild your credit. Make sure the card you apply for reports to a credit reporting agency. This will help you start building a credit history. SELECT A CREDIT
CARD DESIGNED FOR THOSE WITH POOR CREDIT There are a number of credit cards offered by Visa and MasterCard designed for people with poor credit. These cards have low limits, a significant number of fees and high interest rates. But for some people, it may be their best option. Talk to your bank’s administrators or with your current credit card company to see if they offer a credit card that fits your personal needs.
SUBPRIME CREDIT CARDS Another option for those with poor credit, but they are ripe with fees that many people who are already short on cash may not be able to handle. Interest rates can be dangerously high for those with poor credit, so beware of these cards. They are often a last resort for individuals who need access to credit. However, like secured credit cards, they can be used to rebuild credit. Make sure you read the fine print and understand the applicable fees before you apply for a subprime credit card. Again, make sure the card reports to a credit reporting agency so you start building a credit history. Finding a line of credit doesn’t have to be a difficult endeavor. If you know what you are looking for, you can find a line of credit that fits your personal needs without breaking the bank. There are limitations, as well as pros and cons, to many of the forms of credit available to those with poor credit scores, such as secured credit cards or subprime credit cards. But those options do give people choices they otherwise may not have, and they help you build credit, so that eventually you will have a greater number of options.
Posted in Best Practices for Merchants Tagged with: account, applicants, card, consumers, COSIGNED CREDIT CARDS, credit, credit card bill, credit history, credit limits, credit report, credit score, credit-card, creditor, customers, deposit, down payment, good credit, interest rates, low credit limits, MasterCard, payment, poor credit, RETAIL STORE CARDS, retail stores, SECURED CREDIT CARDS, store credit cards, SUBPRIME CREDIT CARDS, visa, Visa and MasterCard