Category: Credit Card Security
 Hello I’m Laylah Cortijo, a new high school intern at National Transaction Corporation. As this is my first internship and job, I couldn’t help but feel extra nervous about the idea of working in a serious, strictly professional environment. However, as I was introduced to the other employees, the work setting, and the values of the business, I recognized the authentic, comfortable, and ethical environment of NTC. There is a strong balance of being a family-owned business, professionalism, and the desire to help potential and current clients.
Hello I’m Laylah Cortijo, a new high school intern at National Transaction Corporation. As this is my first internship and job, I couldn’t help but feel extra nervous about the idea of working in a serious, strictly professional environment. However, as I was introduced to the other employees, the work setting, and the values of the business, I recognized the authentic, comfortable, and ethical environment of NTC. There is a strong balance of being a family-owned business, professionalism, and the desire to help potential and current clients.
Beginning my first day, I introduced myself to everyone, even those I had already encountered from my first tour. It didn’t take long to recognize the positive atmosphere as I was greeted by a fluffy and friendly dog named Baxter and employees that happily assisted me in learning about the business. After being given my own desk, I did more research about the company and spent my days in the office listening in on phone conversations, explanations about the structure of NTC, the merchant account application process and overall, shadowed the employees. As all the newfound information I learned revolved around the merchant account companies and the payment processing industry, I began to understand the basics of credit card processing which is a lot more interesting than I thought it would be.
Being new to something and trying to absorb everything about it all at once is never easy, but everyone around me never hesitated to explain or offer help whenever I needed it; it made me think – if this is how they treat a high school intern like me, then I can imagine how highly they treat and respect their merchants. The constant support and reassurance helped solidify NTC’s attitude of honesty for me. They were able to explain a complex payment processing system in an understandable way which made me feel like I really am in good hands as an intern here.
One aspect of the business that stood out to me was NTC’s strive to keep data safe and secure a top priority. The employees, specifically, the owner’s daughter Megan, informed me of their emphasis on working with healthy businesses and aiming to improve their overall health through secure payment processing. NTC works to ensure their partners are compliant with PCI security standards while keeping them aware of smart potential business decisions that can refine the business’s protection.
In my first week, I’ve learned a vast amount of information about card payment processing, merchant accounts services, payment gateways – topics that will definitely take a little longer for me to fully grasp. I’ve also learned that NTC specializes in merchant accounts for travel agents, which are considered high risk merchant accounts in the electronic payment world. As well as, the company’s push to stay technologically involved through their NTC ePay feature and mobile processing systems like Apple Pay. After listening in on the sales and customer service side of NTC, I was able to learn about the necessity of secure payment systems which applies to all businesses in all industries. What really excites me about NTC is the wide variety of industries they’re familiar with and the ever-changing world of ecommerce.
I was able to form my own opinion about the company in the week that I have spent here. The work space is very family and pet oriented, with a basketball hoop in the back, two adorable dogs that typically reside at the office on regular work days, and a team that strives to be friendly. There’s even a big screen television in the back where parents can keep their children occupied while discussing their plans with NTC consultants. It’s easy to feel comfortable with the specialists because you can trust that they actually know what they are talking about.
From my honest perspective, the employees, the owner, the overall ideals of the business are looking for what’s best for the client. Although they acknowledge the benefits of working with merchants, the sales representatives are never overbearing or forceful with their calls and actively listen to the current state of the person they’re speaking to. There’s a sense of sincerity with building their relationships with businesses that is typically obsolete in the online transaction business. Again, as someone who is an inexperienced high school senior, who is not entirely familiar with the world of payment processing merchant services, and just really wants to understand the working world, I feel very grateful to have gotten this internship and I mean that wholeheartedly. I may be a high school student, but from just a week of working, learning and observation, I plan on recommending NTC when an opportunity comes even after I stop interning.
Posted in Credit card Processing, Credit Card Security, Electronic Payments, Merchant Account Services News Articles
July 26th, 2017 by Elma Jane
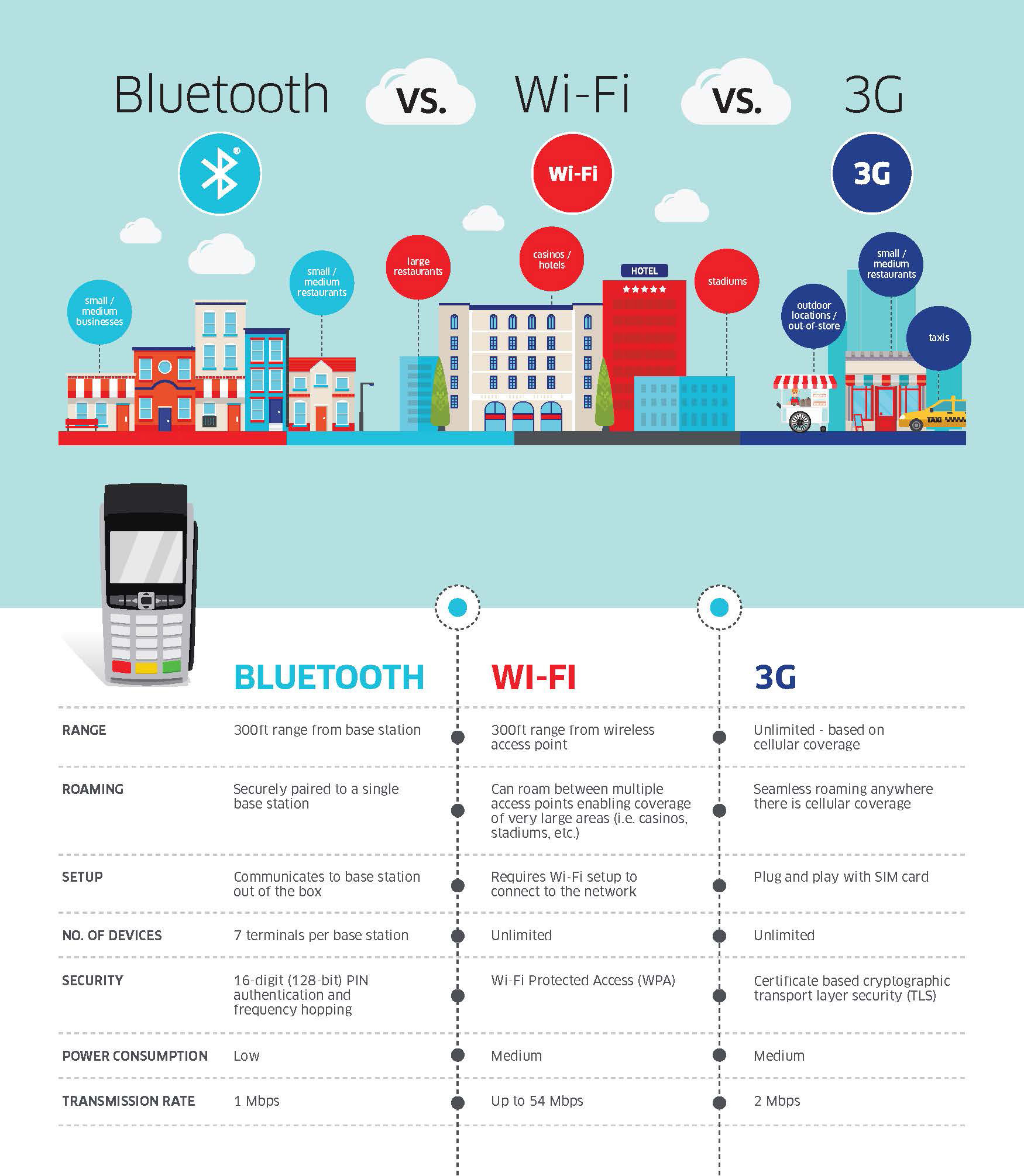
Check out the wide range of smart wireless terminal connectivity options and know the difference.
Bluetooth Wireless: Designed for reliable Bluetooth connectivity even in the most demanding environments.
Rage – 300ft from base station
Roaming – paired to single base station
Setup – Communicates to base station out of the box
No. Of Devices – 7 Terminals per base station
Security – 16-Digit (128-Bit) PIN authentication and frequency hopping
Accept EMV Chip & PIN, magstripe and NFC/Contactless
WiFi: Designed for reliable WiFi connectivity, Wireless mobility for the point of sale.
Rage – 300ft from base station
Roaming – can roam between multiple access points enabling coverage of very large areas.
Setup – Requires WiFi Setup to connect to the network
No. Of Devices – Unlimited
Security – WiFi Protected Access (WPA)
Accept EMV Chip & PIN, magstripe and NFC/Contactless
3G Wireless: Bring compact, reliable 3G Wireless Technology and mobility to the point of sale.
Rage – unlimited – based on cellular coverage
Roaming – Seamless roaming anywhere there is cellular coverage
Setup – Plug and play with SIM card
No. Of Devices – Unlimited
Security – Certificate based cryptographic transport layer security
Accept EMV Chip & PIN, magstripe and NFC/Contactless
Wireless terminals provide merchants with a number of benefits including:
Mobility – enable merchants to better serve the customer and bring the transaction right to the point of service.
Printed Receipt – give your servers the capability to print a receipt for the customer even when away from the POS.
Variety of Payment Options – provide the ability to accept magstripe, EMV, and NFC payments including the latest mobile wallets.
For Electronic Payment Set Up Call Now 888-996-2273
Posted in Best Practices for Merchants, Credit Card Reader Terminal, Credit Card Security, EMV EuroPay MasterCard Visa, Near Field Communication Tagged with: bluetooth, chip, Contacless, EMV, magstripe, nfc, PIN, Security

November 18th, 2016 by Elma Jane
Tokenization and Encryption are completely different technologies when it comes to securing sensitive data, such as credit cards.
Encryption tools and techniques is to mask original data, then allow it to be decrypted. It uses an algorithm to scramble credit card information that makes the data unreadable to anyone.
Encryption is most often “end-to-end.”
Example: When someone enters card data into a web browser to buy an item and decrypted when the purchaser’s authorized credit card information reaches its intended destination, which is the merchant’s e-commerce database.
Encrypted card data is unreadable while it’s “at rest” in a database or “in motion” during a purchase transaction; and inaccessible until a key decrypts it. The chances of a hacker stealing the data is minimal. But, if card data passes through multiple internal systems en route to an acquiring bank or payment gateway, the encrypt/decrypt/re-encrypt process could open a wide security hole, thus creating vulnerabilities to hackers.
Tokenization have found to be cheaper, easier to use and more secure than end-to-end encryption.
Tokenization completely removes credit card data from internal networks and replaces it with a generated, unique “token”. Tokens have no meaning and are worthless to criminals if a company’s system is breached.
Merchants use only the token to retrieve, access, or maintain their customers’ credit card information.
Example: Actual credit card number was 3234 4567 8789 78910, it might become FHIW145BVE65478 when a token is generated. The token is randomly generated and there is no algorithm to regain the original card number. hackers can’t reverse-engineer the actual credit card number, even if they were to grab the tokens off the servers.
Using tokens doesn’t change a merchant’s payment processing experience. Only they’re much safer for a merchant than actual credit cards.
Posted in Best Practices for Merchants, Credit Card Security Tagged with: card, credit cards, customers, data, encryption, gateway, merchants, payment, Security, token, tokenization, transaction

October 13th, 2016 by Elma Jane
Code 10 merchants first line of defense!
How to use “Code 10”
- Call the voice authorization phone number provided by your Merchant Provider. This number can be found on the sticker on your terminal or call your Merchant Service provider and ask to be transferred to the Voice Authorization department.
- Choose the prompt for “Code 10”. Never call a phone number for the card issuing bank provided by a customer; or let the customer call the card issuing bank for you to obtain an authorization code. Do not accept an authorization code given to you by a customer. Authorization code obtained from your Authorization Center can be verified; but not the one from other sources.
- Provide the cardholder name, billing address and shipping address, if the order is a mail order, phone or Internet sale. The representative will attempt to verify the information you provide with the bank that issued the card to the customer.
- The representative will attempt to verify the cardholder information during your call; the data will be forwarded to an investigator for further research and will attempt to contact you within 24 – 72 hours with the current status or results of the investigation.
- Request another form of payment other than a credit card if an authorization request is declined. Do not split a declined transaction into smaller increments to obtain an authorization.
- Obtain an authorization code for the full amount of the sale. Always obtain the authorization code before shipping the merchandise.
Whether you are in a face-to-face environment, or via mail, phone or Internet that sell goods and services you can employ a “Code 10” authorization to verify additional information on a suspicious transaction.
You may be prompted by your processing terminal to call for voice authorization of the charges (CALL AUTH), or you may simply not feel right about the transaction. In either case, you can use “Code 10” to gain additional information before you release your merchandise.
Posted in Best Practices for Merchants, Credit Card Security Tagged with: bank, card, cardholder, customer, internet, merchant provider, merchants, service provider, terminal, transaction

October 11th, 2016 by Elma Jane
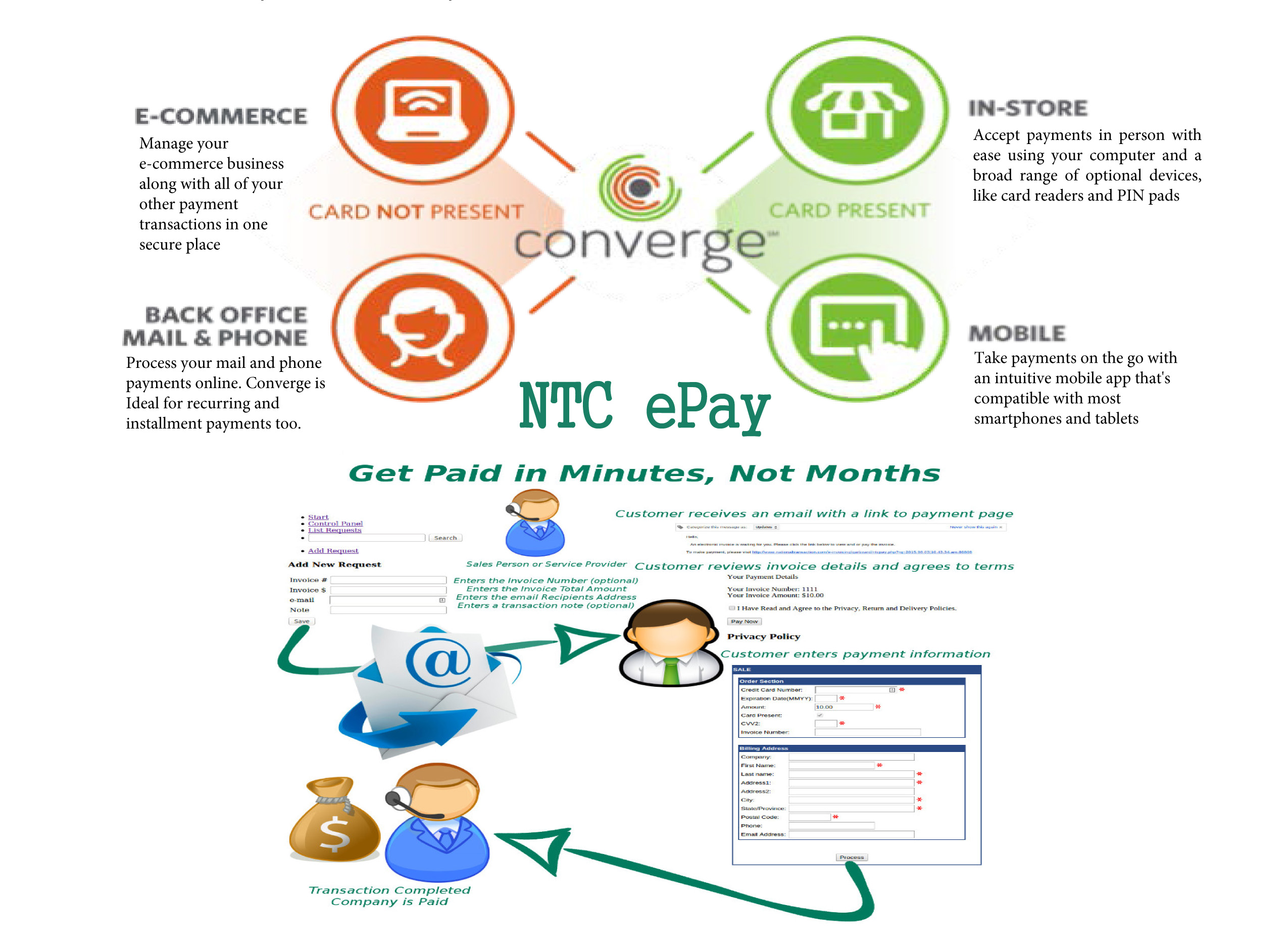
Cybersecurity via Converge:
Converge uses a multi-layered approach to security which helps keep cardholder data safe throughout the entire payment process; from beginning to end.
- EMV: All new Ingenico PIN pads and readers – iCMP and RP457c used with Converge Mobile offer EMV to help protect against counterfeit card use. The PIN pads go a step further in helping protect against lost; stolen and NRI (never received/issued) when a PIN-preferred card is accepted with PIN entry.
- Encryption: All new Ingenico devices also include encryption as a standard security component in addition to protect card data in transit.
- Tokenization: An enhanced security feature that is particularly valuable in card-not-present (CNP) environments when cards are stored on file for processing at a later time, or either for recurring/installment payments.
Get the Ingenico iCMP EMV PIN Pad for only $130.00.
For all payment applications, either Debit or Credit PIN Transaction. Work with both Apple and Android Devices.
Ingenico EMV RP457c card reader for only $75.00.
For Merchants that do not need PIN Pad. Works with hundreds of mobile devices.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Mobile Payments, Smartphone Tagged with: card, card-not-present, cardholder, data, EMV, mobile, payment, PIN pads, Security, tokenization

September 21st, 2016 by Elma Jane
PCI compliance applies to any company, organization or merchant of any size or transaction volume that either accepts, stores or transmits cardholder data.
Any merchant accepting payments directly from the customer via credit or debit card must be Compliant. The merchant themselves are therefore responsible for becoming Compliant, as the deadline for the merchant becomes overdue.
Understanding and knowing the details of Payment Card Industry Compliance can help you better prepare your business. Because failing and waiting to become compliant or ignoring them, could end up being an expensive mistake.
The VISA regulations have to adhere to the PCI standard forms as part of the operating regulations. The regulations signed when you open an account at the bank. The rules under which merchants are allowed to operate merchant accounts.
The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, MasterCard, American Express, Discover, and JCB.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: American Express, cardholder, compliance, credit, customer, data, debit card, Discover, jcb, MasterCard, merchant, Payment Card Industry, payments, PCI, transaction, visa
September 20th, 2016 by Elma Jane
Avoiding Chargeback!
Always ask for the card security codes:
- CVV2 for Visa
- CVC2 for MasterCard
- CID for Discover and American Express.
Always use the Address Verification Service (AVS) and only process sales after receiving a positive AVS response.
Avoid using voice authorizations, unless absolutely necessary.
Billing descriptor must set up properly and shows your phone number. Customer can contact you directly if there is an issue,
Consider using the associations’ 3-D secure services:
- Verified by Visa
- SecureCode by MasterCard
- A 3-D transaction confirmation proves card ownership and therefore protects you from certain types of chargeback. Another additional layer of security for online credit and debit card transactions.
Customers must be informed by email when a refund has been issued or a membership service has been cancelled. Notify them of the date the refund was processed and provide a reference number.
Make available customer support phone number and email address on your website so that customers can contact you directly. You need to meet this requirement before opening a merchant account.
Make it easy for your customers to discontinue a recurring plan, either membership or subscription. Finally, have a no-questions-asked policy.
Notify customers by email and indicate that their cards will be charge each transaction.
Obtain a confirmation of delivery for each shipment.
Process refunds as quickly as possible.
Secure an authorization approval for every transaction.
Secure customers’ written or electronic signatures, for recurring payments or monthly fees. Giving you express permission to charge their cards on a regular basis.
Terms and conditions must be clearly stated on your website. Customers must acknowledge acceptance by clicking on an Agree or a similar affirmative button.
Transaction amount must never exceed the authorized amount.
Reauthorize transaction before settling it if an authorization approval is more than seven days old.
Posted in Best Practices for Merchants, Credit Card Security
September 16th, 2016 by Elma Jane
National Transaction offer valuable features and benefits, if you want to improve your business’s productivity, you should look for the following features below, that you need from your Electronic Payments provider.
Advanced Security Options – 6 out of 10 small businesses close within six months of a card data breach, it is important that Point-of-Sale devices should have appropriate security measures, particularly EMV, encryption and tokenization. NTC offer Safe-T for Small and Medium Businesses and Safe-T for Large Businesses. The Top-tier security is important on your business’s data especially customer information, consider adding additional authentication procedures.
Fast Payment Processing – first step is having up-to-date technology, because some customers might leave, the sooner you have the money processed by your provider, the bigger and stronger your business can become. NTC is adept at administering payments quickly and efficiently. We can provide regular funding or next day funding.
Feature Flexibility – obtaining the features you need from your payment services provider is very important. Look for a provider that appropriately addresses your payment concerns.
Mobile Payment Processing – NTC offer Virtual Merchant/Converge Mobile that gives you the ability to accept payments using your smartphone or tablet anywhere you go. Furthermore, the app works with most Apple and Android mobile devices. Accept a key-entered transactions or swipe cards using an encryption reader. You can now take chip card payments using Ingenico iCMP PIN Pad or the new RP457c card reader.
Reliable Customer Support – NTC is available 24/7, the phones are answered by humans and not automated systems. You got support with your hardware, answer questions and guide you to better understand the process. Customer support is the most important feature of any business partnership you make. At NTC we are very passionate about that.
Up-to-Date Tech – futuristic features, like mobile payment abilities, EMV/NFC, contactless payments are worth investing. Modern consumers are generally more familiar with up-to-date payment systems. Seeing a payment service provider offer a swipe-only terminal should be a red flag, because the recent regulations require merchants to have EMV to provide better data security.
Posted in Best Practices for Merchants, Credit Card Security, Electronic Payments, EMV EuroPay MasterCard Visa, Mobile Payments, Mobile Point of Sale, Near Field Communication, Point of Sale, Smartphone Tagged with: Breach, card data, card reader, chip card, contactless payments, data, EMV, encryption, merchants, mobile, mobile payment, nfc, payments, Payments provider, point of sale, provider, Security, service provider, smartphone, swipe, tablet, terminal, tokenization, transactions
September 15th, 2016 by Elma Jane
Storing credit card data for recurring billing are discouraged.
But many feels storing is necessary in order to facilitate recurring payments.
Using a third party vault provider to store credit card data for recurring billing is the best way.
It helps reduce or eliminate the need for electronically stored cardholder data while still maintaining current business processes.
For recurring billing a token can be use, by utilizing a vault. The risk is removed from your possession.
Modern payment gateways allow card tokenization.
Any business that storing data needs to review and follow PCI DSS requirement in order for the electronic storage of cardholder data to be PCI compliant.
On the primary account number, an appropriate encryption will be applied. In this situation, the numbers in the electronic file should be encrypted either at the column level, file level or disk level.
Posted in Best Practices for Merchants, Credit Card Security Tagged with: billing, cardholder, credit card, data, payment gateways, payments, PCI, recurring, token, tokenization
July 26th, 2016 by Elma Jane
Mobile payment space is growing yet, many small businesses and retailers are choosing to overlook the idea of mobile payment acceptance.
Here are stats that prove the importance of mobile payments:
About 45% of consumers use mobile payments out of convenience.
1 billion users will use in-store mobile payments by 2019.
An increase from $3.2 billion in 2014 to $487 billion by 2020 in US in-store mobile payments is predicted.
Millenials use contactless payments on a regular basis.
Over the next five years, mobile payments will reach about $3 trillion in volume.
There are 16 million Starbucks mobile app active users that make 8 million mobile payments per week.
Transactions globally are on mobile devices.
It is a great investment for a merchant to upgrade your point-of-sale (POS) to have near field communication (NFC) capabilities. If you’re not currently accepting mobile payments, you should start now, your customers who are already using mobile payments will thank you and your business will be ahead of the game as more businesses onboard mobile payment acceptance.
Posted in Best Practices for Merchants, Credit Card Reader Terminal, Credit Card Security, Mobile Payments, Near Field Communication, Point of Sale Tagged with: contactless payments, customers, merchant, mobile payment, Near Field Communication, nfc, point of sale, POS, transactions







