
January 27th, 2016 by Elma Jane
MasterPass To Make Booking Travel Experience Even Easier For JetBlue
MasterCard today added JetBlue as its latest merchant to accept digital payments with MasterPass. MasterPass will be available later this year on the airline’s website and mobile app, giving customers the opportunity to speed up their booking travel experience, according to a press release.
With MasterPass, shoppers can pay for the things they want at thousands of merchants with the security they demand, anywhere online or in app, using any device. The wallet securely stores shoppers’ preferred payment and shipping information which is readily accessible when they click on the “Buy with MasterPass” button and sign into their account.
U.S. consumers can sign up for a MasterPass account by visiting the MasterPass website or through a participating bank. Launched in 2013, MasterPass by MasterCard is free, easy to set up, and available anywhere you see the Buy with MasterPass button. It is currently available in 29 countries and is accepted at 250,000 merchants globally.
Accepting MasterPass by MasterCard on JetBlue’s online and in-app properties expands the relationship between the two companies. JetBlue announced in October 2015 that MasterCard would be its network partner for its co-brand portfolio.
Posted in Travel Agency Agents Tagged with: bank, customers, digital payments, merchant, mobile, mobile app, online, payments, Security, travel

January 26th, 2016 by Elma Jane
The convenience, simplicity and security of Apple Pay are now available to customers who use U.S. Bank FlexPerks American Express Cards.
U.S. Bank which is the fifth-largest bank in the nation will add TouchID biometric capabilities to its mobile app in March.
The company made the disclosure as part of a notable iOS app update released last Friday. Release appears to include, among other enhancements, improvements such as easier navigation, quicker accessibility to account information, and the ability to search transactions from previous months.
U.S. Bank Minneapolis did not give many details about how TouchID will be used within its iOS app, other than to say for fingerprint authentication for enabled devices.
Many major banks already have TouchID implemented in their mobile apps, including Citibank, Wells Fargo and Bank of America. Citibank, for example, implemented TouchID last July. Apple introduced TouchID in mid-2013.
Last week, U.S. Bank enabled for Apple Pay use the last of its debit and credit cards that had not been Apple Pay-capable. Apple Pay relies on TouchID for security and authentication.
Apple Pay is now available with the:
- U.S. Bank FlexPerks Reserve American Express Card.
- U.S. Bank FlexPerks Travel Rewards American Express Card.
- U.S. Bank FlexPerks Select+ American Express Card.
Posted in Best Practices for Merchants Tagged with: account, bank, biometric, cards, credit cards, customers, debit, mobile, mobile app, Security, transactions
December 15th, 2015 by Elma Jane
Visa Inc. has launched the Visa Token Service in Asia Pacific, in association with United Overseas Bank (UOB). Store tokens on mobile devices, cloud-based mobile applications, and e-commerce merchants carry less risk of security hack. This security technology will replace sensitive account information to make payments without exposing bank details.
Tokenized cards are linked to customer’s wallet application or mobile and validated by VisaNet. Biometric authentication and device identification features are available through this service. Visa debit or credit cardholders with NFC-enabled Android smarthphones cardholders will be able to make contacless payments.
Posted in Best Practices for Merchants, e-commerce & m-commerce Tagged with: bank, biometric, cardholders, cards, contacless payments, credit, debit, e-commerce, e-commerce merchants, merchants, nfc, payments, token, Tokenized cards, visa
November 19th, 2015 by Elma Jane
Cyphort Advance Malware Defense, the next generation Advanced Persistent Threat (APT) defense company, recently analyzed the top financial malware threats cybercriminals are using to target electronic payment systems. This will raise awareness of the dangers they present.
Most dangerous financial malware threats of 2015:
Zeus – Since debuting in 2007, this malware has infected tens of millions of computers worldwide. Financial service professionals consider it to be the most severe threat to online banking.
SpyEye – This Trojan horse has infected 1.4 million computers worldwide. Banking information is stolen using a keylogger application, and the bot can take screenshots of a victim’s machine.
Torpig – This botnet is spread using a Trojan horse called Mebroot. Torpig steals targeted login credentials to access bank accounts. It is difficult to detect because it hides its files and encrypts its logs.
Vawtrak – This a relatively new Trojan that can spread itself via social media, email and file transfer protocols. Its unique feature is that it can hide evidence by changing the balance shown to the victim.
Bebloh – This malware targets login credentials to intercept online transactions and breach financial systems.
Shylock – Attacks European banks via Man-in-the-Browser exploits. Worldwide, it has infected 60,000 computers using Microsoft Windows.
Dridex – Malicious code is executed via email attachments and Microsoft Word documents that contain macros that can download a second-stage payload, which can then download and execute the Trojan.
Dyre – Relies on malicious PDF attachments that can exploit unpatched versions of Adobe Reader. The email subject line will be misspelled and read “Unpaid invoic” or contain the attachment “Invoice621785.pdf.” Once the document is opened, Dyre can obtain bank account credentials.
Financial malware has been around for more than a decade, it is quickly evolving in sophistication, to make sure your organization is protected from financial malware, Cyphort recommends the following:
- Keep system and applications patched.
- Educate employees to be careful when visiting websites with popups. If a person does need to go to such a site, do so from a non-Windows platform.
- Adopt a new defense paradigm that continually monitors, diagnoses and mitigates attacks.
Posted in Best Practices for Merchants Tagged with: bank, banking, electronic payment systems, financial, financial service, financial systems, online transactions, payment

October 29th, 2015 by Elma Jane
What is Identity Theft?
Identity theft and identity fraud are terms used to refer to all types of crimes in which someone wrongfully obtains and uses another person’s personal data.
Basic categories of identity theft:
Account Takeover Fraud – is one of the two basic forms of financial identity theft, it occurs when a fraudster obtains and uses a victim’s personal information to take control of existing bank or credit card accounts and carries out unauthorized transactions right at a point of sale or access individual accounts online. Victims are often the first to detect account takeover when they discover charges on monthly statements they did not authorize or funds depleted from existing accounts.
Business or commercial identity theft – entails using a business’ name to obtain credit or even billing a business’ clients for products and services. Business identity theft can go on for years undetected.
Criminal identity theft – occurs when an imposter gives another person’s name and personal information such as drivers’ license, date of birth, or Social Security Number to a law enforcement officer during an investigation or upon arrest.
Identity cloning – some people use identity theft and identity cloning interchangeably, but definitely are not the same thing. True identity clones pretends to be you, they want to assume your identity. They want to become YOU.
Medical identity theft – occurs when someone steals your personal information (like name, Social Security Number or MediCare Number) to obtain medical care in your name. Medical identity theft can damage your credit rating.
New Account Fraud – means using another’s personal identifying information to obtain products and services. New credit card accounts is the most prevalent form of new account fraud. Because the thief is likely to use a different mailing address, the victim never sees the bill for the new account. When this type of fraud involves a credit card, once the new plastic is issued, the criminal turns it into cash very quickly. Victims may also be denied credit as a result of applying for loans.
Posted in Best Practices for Merchants Tagged with: bank, credit, credit card, data, fraud, medical, Medicare, point of sale, transactions
October 27th, 2015 by Elma Jane
Users need to take personal responsibility for their passwords, people tend to stick with simple, easy to remember passwords, but these are the passwords that are easy to hack.
There are many ways that a hacker can get into your online account.
Force attack is one way to gain access to information, and is generally done when a hacker writes a special code to log into a site using specific usernames and passwords.
Hacker instructs the code to try thousands of different username and password combinations on the target site, such as your bank.
Hacker usually focuses on websites that are not known for security and if you are like most people, the same password and username you use on your favorite site is the same you use at your bank is not a good idea.
What makes this easier? Your computer stores cookies, which have information on your login credentials, in a neat, orderly unencrypted folder on the cache of your web browser. As soon as this is accessed, it can be used to get into online accounts.
How to Improve Your Passwords
Consider using a password manager to keep track of all of your account credentials. This way, you won’t have to worry about remembering all of the symbols and letters.
Have a different username and password combination for every account.
Substitute numbers for letters, such as @ for O.
Test your password strength with an online tester, but make sure it is from a reputable source.
Throw in a random capital letter.
Don’t learn a hard lesson when it comes to your passwords, update your log in credentials and have a safer tomorrow.
Posted in Best Practices for Merchants Tagged with: bank, Security
September 29th, 2015 by Elma Jane


There are three contenders competing for dominance in mobile payments.
NFC – or near-field communication, is a contactless data transfer system similar to RFID. When two NFC-enabled devices come into range, you can transfer data from one to the other (such as bringing a phone in range of a credit card terminal).
NFC is found in a lot of phones, especially the flagship devices from Samsung, LG, and Sony. Apple finally jumped into the NFC game in 2014, and Google relaunched its mobile payments service as Android Pay in 2015. Samsung also launched its own app, aptly named Samsung Pay, in 2015.
NFC is a safe method for payments. Sensitive data is stored in a secure element, either built into the SIM card of a phone or placed in a separate chip. In most cases, retailers never actually see your card or bank account data.
QR Codes – or quick-response codes, have the sort of ubiquity that NFC lacks. They work a bit like your standard bar codes, except that instead of relying on one-dimensional analog scanning, they are digital. That means that with a QR code reader app, your smartphone’s camera can be temporarily converted into a scanner. QR codes can embed way more information than your standard bar codes, which gives them the power to do things like open mobile sites, direct you to YouTube Videos, and even enable you to complete mobile payments.
iBeacon – is an Apple-developed technology that uses Bluetooth Low-Energy (BLE, or sometimes also called Bluetooth Smart). Unlike the other two types of technology, it’s really still in the developmental stages. While it can be used for mobile payments, at the moment the biggest application for iBeacon is actually as proximity alert or geo-fence that can go where GPS doesn’t.
It works like this: iBeacon units are set up throughout a building (such as a department store). When someone with an iBeacon-enabled device comes into range of those beacons, they transmit information. Some of the ways this technology could be used would be to transmit mobile coupons or other special offers, to guide customers throughout the store by department, or even to help them find specific items on a shopping list.
NFC devices need to be within 8 inches (though 2 inches is really most effective). iBeacons, on the other hand, have a range of 50 meters, or about 165 feet.
For payments, iBeacons would work nearly the same as NFC: the phone would wirelessly transmit payment information to the terminal or beacon via Bluetooth.
It’s also worth noting that while iBeacons are Apple technology, they are not exclusive to iOS devices. The phone just needs to have Bluetooth Smart and the appropriate app.
Samsung announced its own version of the iBeacon, called Proximity, at its 2014 developer conference in November. it works the same way as iBeacons, but rather than going through an app, Proximity works directly with the phone’s hardware.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Smartphone Tagged with: Android Pay, Apple, bank, card, credit card terminal, google, iBeacon, LG, Mobile Payments, Near Field Communication, nfc, payments, qr codes, Samsung, Samsung Pay, Sony
September 14th, 2015 by Elma Jane
The security rules for fraud liability of credit and debit cards will change in the United States, starting October 1, 2015.
The new security rules would prompt major plastic card brands like MasterCard and Visa to upgrade their magnetic stripe based cards to more modern and secure chip technology based cards.
Credit and debit card fraud amount in the U.S. reached around $11.27 billion, in 2012.
With the new rules, any financial institution and payment processing merchant who would not upgrade their cards to chip technology would be held responsible for any committed fraud with their cards instead of their customers. This new rule would effectively transfer the liability in case of a fraud from the consumer to the least secure card provider. The rule specifically says that liability will fall on the bank or retailer with the least secure technology.
If the bank has not given you a new chip card, and you use your magnetic swipe card and there’s resulting fraud, the bank will be responsible for that.
All merchants who do not offer payment terminals that support chip based cards would be held liable for any fraud committed on their premises as well, from October 1. The new rules say that if the card is chip based and the merchants fail to offer a chip based terminal, and a fraud is committed, they would be held liable instead of the card holder.
With chip based cards, the customer would need to insert their card inside a chip enabled payment terminal while making a purchase. Then, they need to confirm the amount and enter a private pin to verify their identity. The customer would also sign for the purchase like using a regular magnetic card.
Besides MasterCard, Visa has already rolled out the new chip based terminals in the U.S. under its Zero Liability Policy.
The chip based cards are more secure compared to the old magnetic technology. That is one of the reasons why the new rules are promoting the chip based technology over the 55 years old magnetic cards.
Not all merchants have to replace their old magnetic terminals and it is still an optional decision, but industry analysts think that the shift of liability in case of fraud from consumers to financial institutions and merchants would likely prompt them to start using chip based technology.
Posted in Best Practices for Merchants, Credit Card Security Tagged with: bank, card holder, card provider, chip card, debit cards, magnetic swipe, magnetic terminals, merchants, payment processing, payment terminals
September 3rd, 2015 by Elma Jane
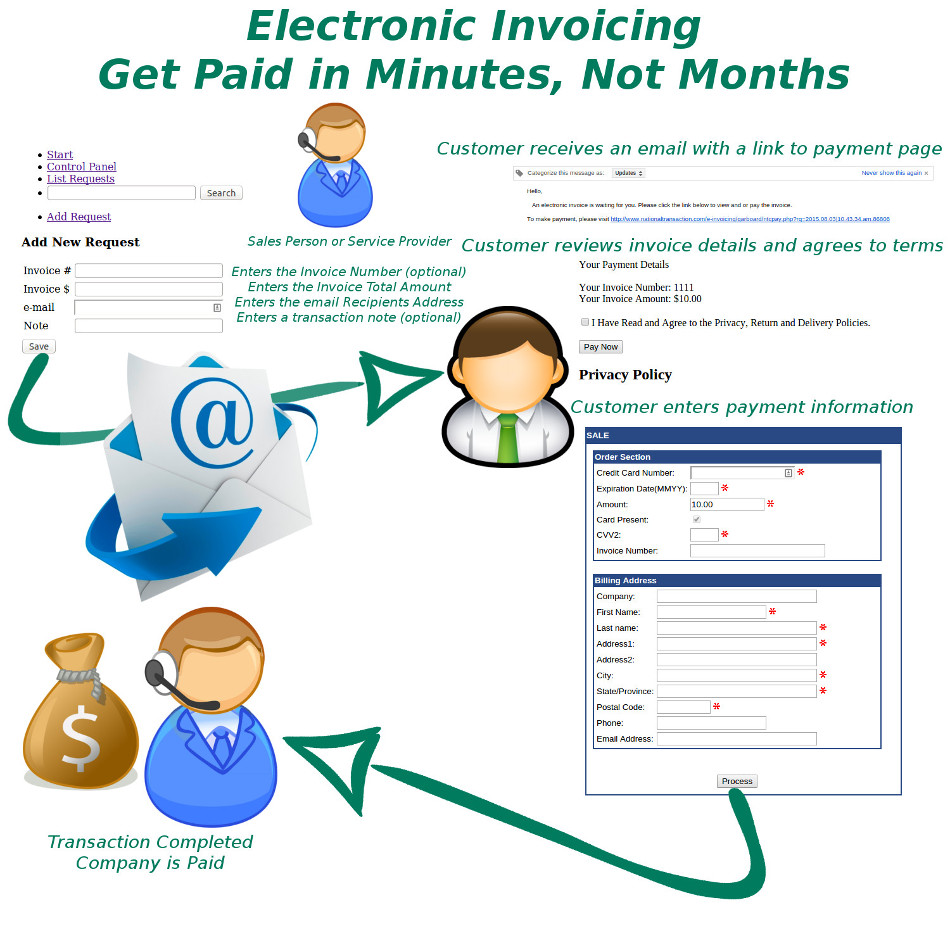
Today, there are numbers of dedicated invoicing software solutions to choose from, but also, specifically built to handle all aspects of invoicing. Whether you send out invoices in the mail, electronically or both. NTC’s Cloud-based invoicing software is a way to simplify your invoicing processes.
National Transaction help merchants consider making the switch to online invoicing methods.
If you’re considering making the transition, check National Transaction’s Electronic Invoice.
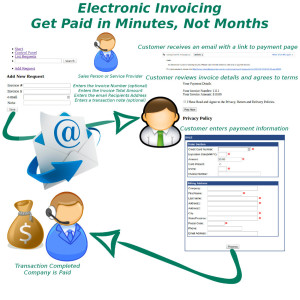
Once the transaction is approved a confirmation email is sent to the merchant and consumer.
Benefits of Electronic Invoicing:
Ease of use – Merchants only needs to enter the email address and the amount of sale to complete order.
Better security – Card Holder enters credit card data directly into an acquiring bank system. Bank stores such sensitive information in an encrypted format on remote servers. This reduces your liability and makes it so you won’t lose all your important data if your server gets hacked or destroyed.
Collect useful sales information – Most invoicing software has reporting capabilities which let you track payments, projected income and client history.
Get paid faster – E-Invoice can be paid the same day. The sooner you send your invoices, the sooner you are likely to get paid. With NTC Electronic Invoice, you can schedule invoices to be sent out ASAP, which means faster, more reliable income for your business.
Look more professional – Invoicing software typically includes professional-looking invoice templates, which you can customize with your business name and logo.
Emailing clients invoices instead of mailing them printed bills, is approximately 10 times cheaper than paper invoicing.
Send invoices from anywhere – Cloud-based invoicing software can be accessed from anywhere with an internet connection. This means you can easily invoice customers or access your business’s billing information wherever you are in the world, and even from your phone if you need to.
Interested in Electronic Invoicing? Give us a call 888-996-2273 or go to our website www.nationaltransaction.com
Posted in Best Practices for Merchants Tagged with: bank, card, card data, credit card, Electronic Invoice, invoicing, merchants
October 23rd, 2014 by Elma Jane
The U.S. government will replace roughly 9 million government-issued payment cards with EMV chip-and-PIN versions early next year in a push to increase awareness and use of the more secure cards. Between 5 and 6 million prepaid debit cards used for issuing government payments, including Social Security and veterans benefits, will be reissued in January 2015. Another 3 million cards issued to federal government employees will also be replaced with EMV versions through the General Services Administration’s SmartPay program.
All the cards will be set up for Chip and PIN security as a U.S. government standard under the upgrade program, rather than the Chip and Signature approach required by Visa and MasterCard for most U.S. retailers starting late next year. However, there was no indication that the new cards will actually have the less secure magnetic data stripe removed.
Finding the right answers with the latest technologies to stop these cyber thieves and taking proactive and positive steps by adopting PIN and chip technology for government-issued debit and credit cards shows the importance of protecting financial transactions. While EMV is important, it’s not a total solution to the issue of data security.
POS devices at all federal agencies that accept retail payments will also be converted to accept EMV cards on a schedule set by the U.S. Treasury Dept. No timetable was given for the federal POS conversion.
The rollouts at four of the six largest U.S. retail chains will give a boost to EMV, which despite an October 2015 deadline has seen slow uptake among retailers. Under a mandate by Visa and MasterCard, retailers who experience credit or debit card fraud after next October but haven’t upgraded their POS equipment to accept EMV cards will be liable for the loss. If the bank that issued the card hasn’t upgraded it to EMV, the bank will take the loss.
But despite that October deadline, fewer than half of retailers’ POS terminals are expected to be able to accept EMV cards by the end of 2015, and barely half of U.S. payment cards will have been upgraded by then, according to the Payments Security Task Force, a banking industry group tracking EMV uptake.
The 9 million federally issued cards are a tiny fraction of the 1 billion credit and debit cards in use in the U.S., so the overall impact of accelerated EMV conversion is likely to be small. However, the Buy Secure initiative also explicitly includes a consumer-education component. Visa said it will spend $20 million in a public service campaign, and American Express said it will launch a $10 million program to help small merchants upgrade their POS terminals.
Small merchants are less likely to know about EMV than large retail chains, which have been making implementation plans for years.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security Tagged with: American Express, bank, Chip and PIN, chip and signature, credit cards, data security, debit card fraud, debit cards, EMV, emv cards, EMV conversion, financial transactions, magnetic data stripe, MasterCard, Merchant's, payment cards, Payments Security, POS conversion, POS devices, POS equipment, POS terminals, retail payments, visa











