All merchants that accepts, transmit or stores cardholder data are required to be PCI (Payment Card Industry) Compliant. Most believe that because they do not charge the credit cards themselves, they are exempt. Why all agencies are required to be complaint even when they don’t charge credit cards themselves, and some steps to ensure your agency is PCI compliant.
What is PCI compliance?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that all companies that process, store or transmit credit card information maintain a secure environment. PCI applies to all organizations or merchants, regardless of size or number of transactions, that accepts, transmits or stores any cardholder data. Travel agents accepting, storing and transmitting credit card information to suppliers, are required to be compliant too. Suppliers reinforce this through their travel agent guidelines/contracts. Travel Agency must adhere to the applicable credit card company’s procedures for credit card transactions.
Consequences of Not Being PCI Compliant
If an agency is not PCI compliant, the agency can lose the ability to process credit card payments with that supplier. Not being able to pay with client credit cards can be a serious roadblock for agencies, and an inconvenience for clients.
If you have a merchant account and are found to be out of compliance, you can be fined.
How to be PCI Compliant
Don’t store the CCV security code from the client’s credit card. The client does not have the authority to grant you permission to store their CCV code. The credit card company explicitly forbid storage of the CCV code.
Make sure you securely store any client information, including their credit card number and expiration date. If you use a CRM, ensure that you have a strong password. If your CRM database is stored on your computer hard drive, encrypt it (there is a great encryption software that is free of charge). If you have an IT resource, talk to them about installing a firewall on your network, installing anti-virus and anti-malware protection, and any other steps that you can take to secure your client data even further.
If you keep paper copies of client information, keep it in a locked filing cabinet or desk drawer. When you no longer need their credit card information, cross shred it.
Home based businesses are arguably the most vulnerable simply because they are usually not well protected, according to the PCI Compliance Guide. Having strong passwords, encryption, a firewall, anti-virus and anti-malware protection are all inexpensive steps that you can take to protect your business and your clients’ sensitive data.
If you receive a courtesy call reminding you about PCI Compliance, don’t ignore it.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Payment Card Industry PCI Security Tagged with: cardholder, cardholder data, cards, CCV, CCV code, credit, credit card company, credit card number, credit card payments, credit card transactions, credit cards, crm, CRM database, data, database, encryption software, merchant account, Merchant's, network, Payment Card Industry, PCI, security code, transactions, travel agents
May 4th, 2015 by Elma Jane
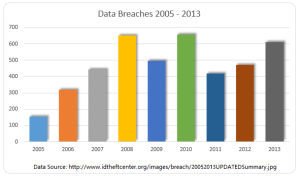
The rate of payments fraud is steadily decreasing, the current frequency stands at 0.06 percent or six basis points.
The perception of risks associated with card payments are much larger than the actual threat or reported losses. But the lack of trust that comes from such perception could impact the growth of the payments industry.
Recent advancements in payments security, such as tokenization and multiple tier authentication protocols, have contributed to the manageable number of fraudulent transactions. The EMV migration is expected to push the figure even lower, as chip-enabled technology spreads to over 50 percent of the US by the end of 2015.
For criminals, breaking into robust financial systems is becoming more costly and time consuming, which has discouraged many from attempting such unlawful acts.
Fraud is something that we can’t say will be eliminated completely. But efforts by all stakeholders in the industry can contain it to the minimum.
Counterfeit cards and payments data falling into the wrong hands are the two most common types of fraud that consumers are facing today. The surge in e-commerce has been linked to greater risks of fraud in the online channel, and while counterfeiting cards may be more difficult with EMV in place, online fraud has historically increased in its place.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa Tagged with: card payments, cards, consumers, data, e-commerce, EMV, EMV migration, fraud, payments, payments industry, Payments Security, tokenization, transactions
April 21st, 2015 by Elma Jane
An advanced strain of malware called “Punkey,” is capable of attacking Windows point of sale terminals, stealing cardholder data and upgrading itself while hiding in plain sight.
Researchers from Security vendor Trustwave discovered the new strain. The investigation found compromised payment card information and more than 75 infected, and active, Internet Protocol addresses for Windows POS terminals.
Punkey poses a unique threat to payment networks, particularly because it also can download updates for itself.
If the malware author has a new feature it wants to add or updates to get rid of bugs, it actually pushes the malware down from the command and control server, revealed by Trustwave’s SpiderLabs research center. Punkey operates like a typical Botnet.
The malware hides inside of the Explorer process, which exists on every Windows device and manages the opening of individual program windows. Punkey scans other processes on the terminal to find cardholder data, which it sends to the control server.
The malware performs key logging, capturing 200 keystrokes at a time. It sends the information back to its server to store passwords and other private information.
A year ago, security vendors warned retailers against using Windows XP at the point of sale, since Microsoft stopped supporting Windows XP security patches. However, even Punkey is not attacking Windows due to any vulnerability in the systems, so even merchants with newer versions of Windows are at risk.
Punkey just runs like any Windows binary would. Even if the system is upgraded or a new system is put in place, criminals are still getting malware on the POS in other ways.
Many retailers use remote desktop support software, which fraudsters take advantage of, they steal a password and install malware like a technician would install any software.
While Punkey represents a more sophisticated POS malware than Trustwave has seen previously, merchants can still protect themselves through attention to basic security best practices.
Merchants should update antivirus and firewall protections, monitor the remote access software, establish two-factor authentication and check network activity daily for anything out of the ordinary. Unfortunately, many organizations have neither the expertise nor the manpower to perform these tasks.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Reader Terminal, Credit Card Security, Mobile Point of Sale, Payment Card Industry PCI Security, Point of Sale Tagged with: card, cardholder, cardholder data, data, Malware, Merchant's, payment, payment networks, point of sale, POS terminals, retailers, terminals
December 1st, 2014 by Elma Jane
Few Americans will likely remember the life and work of Martin Cooper, largely because most Americans have no idea who Martin Cooper is. Without Martin Cooper much of what we identify as normal life for the last two decades would not have been possible, as without his invention we would still be looking for pay phones, dropping off film to be developed, printing out boarding passes and contemplating a future where a plastic rectangle was the height of payments technology.
Anyone reading this has a phone with internet access which means no one has to guess, with a few taps on a smartphone most readers who didn’t already know were able to find out that Martin Cooper invented the handheld mobile phone and by so doing changed the lives of not just Americans, but people all over the world.
Mobile has integrated so seamlessly into our life that we didn’t realize it was changing everything we do.
Here are the list of all of the ways that mobile has improved life for us all.
We All Get To Know Everything All The Time, with just a smartphone. Impulse buy is a thing of the past because consumers just don’t buy on impulse as much anymore. A new intentionality has taken hold of shopping. Many Americans have the money and the will to spend. But they are time-pressed and deal savvy, visiting stores only when they run out of items like cereal or toilet paper and after doing extensive research on purchases online and with friends. They buy what they came for and then leave. Plus consumers are harder to fool, they know if they are being overcharged because they can look it up in real time while they are in the showroom.
Full Price Is A Notion Utterly Without Meaning. There are sites like Groupon, LivingSocial and a thousand imitators offer coupons pretty much across every retailer that mean no matter where one is shopping or eating they’re probably a few button taps away from paying less for the type of service they are out for. And then there are the retailer rewards programs all bent on giving consumers more stuff for free as long as they use their mobile coupons.
We All Think Way More About Privacy And Digital Security Than We Used To. Twenty years ago one’s largest security concern was probably that their home or car would be broken into, followed closely by their wallet being stolen. Now we wait for Russian cybercriminals to steal our cards by hacking into POS systems and lifting the data. Or for cybercriminals to hack our phones and upload naked pictures of us to the internet (celebrity readers only). Or for Nigerian princes to trick our grandparents into wiring them money. In short, while we still fear for our physical possessions as much as we ever did, the mobile world gave us something entirely new to worry about, the integrity of our data and who could use our phones, cards and email accounts as a backdoor into our entire personal and financial lives.
We Want It All, And We Want It Now. Anyone with a phone in their pocket can, in one way or another, buy it on the spot. Which has given rise to the push for same-day delivery, consumers who can buy it now, also want to be able to get it now, or as close to now as possible.
We Also Want It Later. Maybe the consumer likes going to the store, enjoys the Christmas lights, wants to eat at a mall food court, they just don’t want to stand inline. And now, through the magic of omnichannel commerce, they may not have to do. Through the magic of multi-device shopping an instore pick-up, consumers are increasingly getting used to finding something on their mobile, paying on their computer and picking up in store. Or some combination thereof.
Mobile has made commerce less a race between the e-markets and the brick-and-mortars, and more a race to offer the most seamless commerce experience. Mobile has taught ever one to care less about where they buy, and more about what the total buying experience is.
We Pay For Access Instead Of Objects. Ten years ago when your family set about its early experiments in binge watching television with the first season of Lost, odds are everyone gathered round and watched a DVD set or maybe a Blue Ray, if your family happened to be full of early adopters.
This weekend, when entire families are sitting down to watch How To Get Away With Murder, more likely than not they are streaming it through Hulu. Unless they don’t want to watch that, in which case, they are watching something else on Netflix on their phone while sitting in the same room with their family. Unless of course this is a football family, in which case you are paying the NFL for access to every football game played everywhere in America tomorrow and a cable company to watch in HD.
We Want To Use A Phone To Access Everything. It’s almost now quaint to refer to a time when phones were used primarily to talk. With the rapidly emerging internet of things, it will soon be quaint to talk about a phone as a tool used primarily for communicating and shopping.
The smartphone is already heading toward being the key interface between connected devices and products (The Internet of Things) and their users. Among other things, people will use the device to remotely control household appliances, interact with screens and automatically adjust car settings to their preferences.
We Kinda Hope The Phone Might Keep Us Alive. With the release of Apple Pay, also came the release of Apple Health that has widely been reported as ushering in the age of mobile device as wellness guru. Smartphones can already help people lead healthier lives by providing information, recommendations and reminders based on data gathered through sensors embedded in users’ clothing (shoes, wristbands, etc.) or through other phone capabilities (motion detectors, cameras, etc.).
And, even if you don’t listen to your phone and put your health at risk, it will still probably save you. Internet-enabled mobile devices are becoming important tools in broadening access to health care, diagnosing diseases and saving lives in crisis situations.
Making Life A Lot Better For Everyone. Small merchants can do something now that they couldn’t do en masse twenty years ago. Take credit card payments and use a tablet to do that and run their business. With the emergence of mobile, came thousands of the other mPOS solutions and platforms exploding all over the world. This has not only changed the way these small businesses operate, it has changed their entire pitch to their customers.
Mobile has made life easier for many consumers, but for some businesses and many people mobile has made mainstream financial participation possible.
Posted in Best Practices for Merchants, Smartphone Tagged with: (POS) systems, brick-and-mortars, cards, consumers, credit card payments, customers, data, e-markets, email accounts, mobile, mobile coupons, mobile device, mPOS solutions, omnichannel commerce, pay phones, payments technology, platforms, Small merchants, smartphone, tablet
October 15th, 2014 by Elma Jane
Another day, another corporate data breach. Business owners are now aware that cyber criminals are becoming increasingly smart and sophisticated in their hacking methods, and they can target just about anyone. But smaller companies that think, It can’t happen, or they are too small for hackers to notice, may be setting themselves up for a devastating data breach.
Large corporations typically have a lot more money and resources to invest in IT security, whereas small to medium businesses do not have the IT staffing, resources, money or know-how to put effective security measures into place to combat security vulnerabilities.
If a small business owner is responsible for security practices, it’s going to fall to the lower end of the priority list. The business will have less protections in place and hackers recognize that. Criminals are looking for unlocked doors.
Recent research found that more than half of all small and midsize businesses have been hacked at some point, and nearly three-quarters weren’t able to restore all the lost data. The two most common methods of attack are phishing, gathering sensitive information by masquerading as a trusted website and watering holes. Installing malware on commonly used websites of a target group. These tactics, grant cyber criminals access to the information that leads to identity theft and stolen credit card information.
A credit card breach is fairly easy to recognize once customers of a certain company all begin reporting fraudulent charges. But by that point, a breach has already done a significant amount of damage, not just to the consumers but to the company they trusted to protect their data.
A computer that appears to have been tampered with.If you turned off your computer when you left work and it’s on or has windows and programs running when you return, someone may have been trying to steal important information. This is an especially likely scenario with internal data theft, such as the AT&T breach. Keeping your machines password-protected and encrypting any sensitive data can prevent unauthorized individuals from accessing the information.
Locked-out accounts. If you’ve ever been locked out of your email or social media accounts, you know it’s usually because you typed the wrong login credentials one too many times. If you receive a lock-out message the first time you try to access an account (and you know you’ve typed your password correctly), you might have been hacked. This can mean that someone is attempting to brute force an account, or that an account has already been compromised and the password changed.
Unusually slow Internet or computers. This could be a sign of a compromised machine that is sending out lots of traffic, or that malware or a virus is on the machine. You should also look for pop-up ads (especially if you have an activated blocker) or websites that don’t load properly.
In all of these instances, minor inconveniences that most people might ignore if the problem seems to resolve itself could be signs of a much more serious problem. Both experts advised keeping your antivirus software, firewalls and device operating systems up-to-date, and always remaining alert for any suspicious activity.
Posted in Best Practices for Merchants Tagged with: consumers, credit card breach, credit card information, customers, data, data breach, device, Security, website
September 18th, 2014 by Elma Jane
Electronic invoicing is the exchange of the invoice document between a supplier and a buyer in an integrated electronic format. Traditionally, invoicing, like any heavily paper-based process, is manually intensive and is prone to human error resulting in increased costs and processing lifecycles for companies.
The issue of compliance seems to have separated E-Invoicing from B2B. Surprisingly many Finance leaders are unaware that their company is already sending/receiving EDI electronic invoices.
E-Invoicing is a common B2B practice and National Transaction is ready to launch its E-Invoicing system.
True definition of an electronic invoice is that it should contain data from the supplier in a format that can be entered integrated into the buyer’s Account Payable (AP) system without requiring any data input from the buyer’s AP administrator.
There are number of formats to be employed, it is useful to Apply below guidelines:
An E-Invoice:
1) Structured invoice data issued in Electronic Data Interchange (EDI) or XML formats.
2) Structured invoice data issued using standard Internet-based web forms.
Not a true E-Invoice:
1) Paper invoices sent via fax machines.
2) Scanned paper invoices.
3) Unstructured invoice data issued in PDF or Word formats.
Although significant cost and time savings can be achieved by removing paper and manual processing from your invoicing, the real benefits of E-Invoicing come with the level of security that comes with E-invoicing. Integration between your trading partners and your invoicing software and other business systems are optional. National Transaction can offer a customized Electronic Invoice Structure .
Posted in Best Practices for Merchants Tagged with: (AP), Account Payable, AP administrator, b2b, buyer, compliance, data, E-Invoice, E-Invoicing, E-Invoicing system, EDI, EDI electronic invoices, electronic data interchange, electronic format, electronic invoices, Electronic invoicing, Finance leaders, Internet-based web, invoice document, invoicing, National Transaction, Paper invoices, Security, supplier, web
September 15th, 2014 by Elma Jane
Visa has taken advantage of the hoopla surrounding Apple’s application of digital account tokens to replace card numbers for online and mobile purchasing by initiating the roll out of its Token Service to US clients.
Visa Tokens will be made available to issuing financial institutions globally, starting with US banks next month, and followed by a phased roll-out overseas beginning in 2015. The technology has been designed to support payments with mobile devices using all major mobile platforms.
More than 750 staff from across the Visa organisation globally were involved in the effort, working closely with initial launch partners – financial institutions, merchants and processors to ensure the ecosystem was ready. Today, Visa is making these services available and believe it will help transform connected devices and wearables into secure payment vehicles.
Visa Token Service replaces sensitive payment account information found on plastic cards with a digital account number or token. Because tokens do not carry a consumer’s payment account details, such as the 16-digit account number, they can be safely stored by online merchants or on mobile devices to for e-commerce and mobile payments.
The release of the service has been given added urgency by a spate of successful hacks on merchant card data stores, such as the recent plundering of card account data at Home Depot and Target.
MasterCard has its own equivalent Digital Enablement Service, which will be released outside of the US in 2015.
Posted in Best Practices for Merchants, Credit Card Security, e-commerce & m-commerce, Mobile Payments, Visa MasterCard American Express Tagged with: account details, card, card account data, card data, data, digital account, digital account number, e-commerce, financial institutions, MasterCard, merchant card data, Merchant's, mobile, Mobile Devices, Mobile Payments, mobile platforms, online merchants, payments, processors, Token Service, tokens, visa, Visa organisation, Visa Token Service, wearables
September 12th, 2014 by Elma Jane
Over the last couple of years, Big Data has become a huge buzzword in the business world. Whether this data comes from social networks, purchase histories, Web browsing patterns or surveys.
The vast amount of consumer information that brands can gather and analyze has allowed them to improve and personalize their customers’ experiences. But for all the attention Big Data has received, many companies tend to forget about one application of it…Employee Engagement.
When done in the right way, tracking, analyzing and sharing employee performance metrics can be very beneficial for both you and your staff. One of the things that is very powerful is being able to analyze real-time information, boil it down into performance data and empower employees with reports from that data. If you can provide employees with data to do their job better in a succinct, actionable way, it’s very motivating.
The more Big Data can be incorporated into an intimate individual experience, the better. This demonstrates to the employee that the experience is not just off the shelf and that it is relevant to the person. This personal relevance is shown to deliver higher engagement.
Applying Big Data analytics to employees’ performance helps identify and acknowledge not only the top performers, but the struggling or unhappy workers as well.
If you want to introduce analytics technology to your employee engagement strategies, below are a few tips to help you.
Find a program that integrates with your current systems. For any new software that you implement within your company, it’s important to make the transition as seamless and simple for your employees as possible.
The software has to work where the employees work already. You can’t make them switch tasks and go to another platform to aggregate the data stream. The software should genuinely assist the end user. Your choice of software should be a grassroots decision, and you should have buy-in from your employees before you ask them to use the new system.
Consider how employees will view themselves and others. Once you introduce performance and engagement analytics into your company, you’ll have to consider how that program fits into employee relationships and workplace culture as a whole.
A company needs to take into consideration the actions of the employee’s co-workers and how to make these data points of interest to the employee. This helps to foster a respected and trusting engagement experience and data needs to be used to build trust. No matter what solution you choose, an analytics program moves you away from the traditional manual reporting process of performance measurement; helping make your staff more efficient, motivated and engaged.
Business software is in the beginning stages of being useful for performance measurement. Businesses have not pushed for innovation as hard as consumers have, but now that’s starting to change. Think about business processes in a different way and gather data in a way that matters.
Select and focus on the most important metrics.Analytics programs can pull and process data for a large number of metrics. Even when applying Big Data to customer service, many businesses struggle to keep up with the volume of information pouring in. Narrowing down your focus to only the most important key performance indicators (KPIs). Don’t introduce too many metrics, it becomes too difficult and confusing. If you can boil it down to some very simple statistics, like a score that incorporates the elements you want, everyone can focus on consolidated KPIs.
Posted in Best Practices for Merchants Tagged with: big data, Business software, consumer, customer, customer service, data, key performance indicators, program, service, social networks, software, web, Web browsing patterns
September 11th, 2014 by Elma Jane
Online retailers are finding the bricks-and-clicks strategy to be an effective way to serve and engage shoppers. Perhaps that is why an increasing number of ecommerce merchants are setting up shop offline. It’s important to note, however, that a bricks-and-clicks business isn’t just about having a physical store and an ecommerce site. For this model to be effective, each channel must complement and add value to the other.
Guidelines to execute a bricks-and-clicks strategy:
Allow Access to Online Account Information in Physical Store
Bridge the gap between bricks and clicks by giving your customers and physical-store staff access to online account information. Doing so can enhance shopping experiences and drive sales.
Integrate Online and Offline Inventory, Fulfillment
Offer click-and-collect services that allow shoppers to buy merchandise online and pick it up at a local retail branch or service station. Many consumers would rather forgo the shipping costs and wait time and instead pick up their items at a time and place that’s convenient for them. Also, use your brick-and-mortar inventory when an item is out of stock online.
Use Online Data for Offline Selling, and Vice Versa
Data pertaining to online sales and traffic won’t just help you optimize your ecommerce site. It can also apply to offline decisions. For instance, if you see an increase in sales for a particular product on your website, you should consider promoting it offline, as well, to your brick-and-mortar shoppers.
Also pay attention to social media data such as Facebook likes and Pinterest pins. What’s trending on social sites can help with merchandising and marketing. Consider something similar in your brick-and-mortar business. Take note of the most liked, viewed, and pinned items online and then leverage that information when making decisions regarding product displays, inventory and more.
You can also use offline information to enhance your ecommerce site. Utilize in-store analytics tools, such as people counters and sensors, to better understand how your offline customers behave and then compare that with online behavioral data to spot patterns and opportunities.
Qualitative information, such as shoppers’ common questions and concerns, can also be used to improve your online shop. For instance, if your physical store associates keep getting the same questions about a particular product, there’s a good chance that online shoppers have similar queries. So you may want to include the answer in that item’s product description page.
Use Smartphone Beacons in Physical Stores
Beacons are Bluetooth-enabled devices that let brick-and-mortar merchants send customized offers and recommendations to their shoppers via their smartphones based on where the shoppers are in the store. For example, if a shopper is in the footwear department, the retailer can use its store beacons to send the shopper a coupon for shoes. Bricks-and-clicks businesses can also use the technology to send tailored offers to shoppers based on their online behavior.
Posted in Best Practices for Merchants Tagged with: account, Beacons, bluetooth, brick and mortar, business, consumers, coupon, customers, data, devices, ecommerce, Facebook, inventory, marketing, merchandising, Merchant's, Online Account Information, Online Data, pinterest, product, sales, shoppers, site, smartphone, social sites, store, website
September 10th, 2014 by Elma Jane
Merchant go into business to make a sale. They go to great length to advertise their business and then they make a sale and don’t track it… They don’t track the very customer they went into business to attract…That seems crazy…But now more companies are embracing the practice of collecting email addresses at the point of sale (POS) and they’re doing so with increasing regularity. An example, when customers are at the cash register, many brick-and-mortar stores now offer to email them receipts
Confidently collect email addresses at POS:
Your email service provider should be able to implement a text-to-join acquisition program for you that executes quickly and can be built specifically to mitigate the risks around POS data collection.
Instead of relying on sales associates to accurately input email addresses, your customers can use SMS to text their email addresses to your short code.
Customers receive an immediate SMS reply message letting them know to check their email for their receipt.
A mobile-optimized receipt is immediately emailed to the address.
This can be followed by an email inviting customers to join your company’s email program. Offering a purchase discount can increase opt-ins. New joiners can be sent an age verification email, if relevant.
Your welcome email, including discount coupon, is sent and the relationship starts off on the right foot.
Increasing your confidence about POS email address collection, a text-to-join program can increase your acquisition rates. It can engage those customers who prefer to provide their information privately via their mobile devices. It can help protect companies against potential blacklisting because of typos and confirmed opt-ins. It can even reduce overhead costs by saving sales associates valuable time. Understanding these important email address collection issues and adopting the prescribed best practices are critical to ensuring customers have a safe, positive and valuable experience with your company at the point of sale and beyond.
Virtual Merchant can collect data too, and as a provider we can help merchant use that data. We are committed to providing appropriate protection for the information that is collected from customers who visit the website and use the Virtual Merchant payment system. Policy Privacy is updated from time to time.The website is provided to our customers as a business service and use of the site is limited to customers only.
If the merchant never makes a sale before 10 why do they open at 9 ?? This is only one small example on how collecting data first and then analyzing that data can shape businesses and find money you may be throwing away ….
Posted in Best Practices for Merchants, Mobile Point of Sale, Point of Sale Tagged with: brick and mortar, business, cash, cash register, customers, data, discount, discount coupon, email, merchant, mobile, Mobile Devices, payment, payment system, point of sale, policy, POS, provider, purchase, Rates, receipts, sale, service, sms, store's, virtual merchant, website