January 15th, 2015 by Elma Jane
The fact that your business needs a mobile presence is by no means news. Brands today know that being accessible to the increasing number of smartphones and tablet users is a must NOW, the goal is to provide a top-notch user experience.
Mobile is opening the door for designing new experiences that complement a brand’s physical presence. The context of WHEN, WHERE and WHAT a customer is doing during their day allows companies to enhance a person’s interaction and customize device-specific experiences.
Brands will need to meet the following mobile experience expectations in 2015:
Combating fraud through mobile. Mobile users want to safeguard themselves against fraud, and 56 percent are willing to deal with a slightly more complex user experience if it means greater protection. Businesses can provide an intuitive, high-quality mobile experience that also protects against fraud by offering to validate transactions, set fraud controls and generate unique payment IDs through the user’s mobile device.
Complement, not copy: E-commerce providers must leverage mobile to complement the user experience, rather than provide a replica of what users get through a Web browser. Nearly 4 in 10 mobile users are most likely to use their mobile phone for shopping, so businesses need to ensure that those customers are getting something unique from their mobile interaction.
CRM through mobile marketing: Mobile marketing isn’t just for acquisition anymore. Today, it’s about boosting loyalty by using mobile for customer, consumers always have their mobile device on them and check it more than 150 times a day. Businesses can communicate with their existing customers through alert notifications, in-app, email and mobile Web. But don’t overdo it. The key to maintaining an effective relationship is doing so in a complementary way, giving users what they need when they need it.
Mobile apps and mobile Web: Got a mobile app but not a mobile-friendly website, or vice versa? You might want to put your energy into leveling out your mobile presence. Consumers are about equally split when it comes to their preference of app versus browser: The percentage of users who prefer their mobile browser when completing a task 28 percent is only slightly higher than the 23 percent that prefer to use an app. Both app and Web designs are critical for businesses in the mobile space, so it pays to do them right.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Smartphone Tagged with: consumers, crm, customers, e-commerce, mobile, mobile device, payment, provider's, Smartphones, transactions
October 8th, 2014 by Elma Jane
When the PCI Security Standards Council (PCI SSC) launched PCI DSS v3.0 in January 2014, businesses were given one year to implement the updated global standard. Now that the deadline is fast approaching, interest is picking up in what v3.0 entails. On Jan. 1, 2015, version 3.0 of the Payment Card Industry (PCI) Data Security Standard (DSS) will reach year one of its three-year lifecycle.
Trustwave, a global data security firm, is on the frontlines of helping secure the networks of merchants and other businesses on the electronic payments value chain against data breaches. As an approved scanning vendor, Trustwave is used by businesses to achieve and validate PCI DSS compliance.
PCI DSS v3.0 is business as usual for the most part, except for a few changes from v2.0 that considers impactful for large swaths of merchants. The top three changes involve e-commerce businesses that redirect consumers to third-party payment providers. The expansion of penetration testing requirements and the data security responsibilities of third-party service providers.
Penetration testing
Penetration testing is the way in which merchants can assess the security of their networks by pretending to be hackers and probing networks for weaknesses. V3.0 of the PCI DSS mandates that merchants follow a formal methodology in conducting penetration tests, and that the methodology goes well beyond what merchants can accomplish using off-the-shelf penetration testing software solutions.
Merchants that are self assessing and using such software are going to be surprised by the rigorous new methodology they are now expected to follow.
Additionally, penetration testing requirements in v3.0 raises the compliance bar for small merchants who self assess. Those merchants could lower the scope of their compliance responsibilities by segmenting their networks, which essentially walls off data-sensitive areas of networks from the larger network. In this way merchants could reduce their compliance burdens and not have to undergo penetration testing.
Not so in v3.0. If you do something to try to reduce the scope of the PCI DSS to your systems, you now need to perform a penetration test to prove that those boundaries are in fact rigid.
Redirecting merchants
The new redirect mandate as affecting some, but not all, e-commerce merchants that redirect customers, typically when they are ready to pay for online purchases to a third party to collect payment details. If you are a customer and you are going to a website and you add something to your shopping cart, when it comes time to enter in your credit card, this redirect says I’m going to send you off to this third party.
The redirect can come in several forms. It can be a direct link from the e-commerce merchant’s website to another website, such as in a PayPal Inc. scenario, or it can be done more silently.
An example of the silent method is the use of an iframe, HTML code used to display one website within another website. Real Estate on the merchant’s website is used by the third-party in such a way that consumers don’t even know that the payment details they input are being collected and processed, not by the e-commerce site, but by the third party.
Another redirect strategy is accomplished via pop-up windows for the collection of payments in such environments as online or mobile games. In-game pop-up windows are typically used to get gamers to pay a little money to purchase an enhancement to their gaming avatars or advance to the next level of game activity.
For merchants that employ these types of redirect strategies, PCI DSS v3.0 makes compliance much more complicated. In v2.0, such merchants that opted to take Self Assessment Questionnaires (SAQs), in lieu of undergoing on-site data security assessments, had to fill out the shortest of the eight SAQs. But in v3.0, such redirect merchants have to take the second longest SAQ, which entails over 100 security controls.
The PCI SSC made this change because of the steady uptick in the number and severity of e-commerce breaches, with hackers zeroing in on exploiting weaknesses in redirect strategies to steal cardholder data. Also, redirecting merchants may be putting themselves into greater data breach jeopardy when they believe that third-party payment providers on the receiving end of redirects are reducing merchants’ compliance responsibilities, when that may not, in fact, be the case.
Service providers
Service provider is any entity that stores, processes or transmits payment card data. Examples include gateways, web hosting companies, back-up facilities and call centers. The update to the standard directs service providers to clearly articulate in writing which PCI requirements they are addressing and what areas of the PCI DSS is the responsibility of merchants.
A web hosting company may tell a merchant that the hosting company is PCI compliant. The merchant thought, they have nothing left to do. The reality is there is still always something a merchant needs to do, they just didn’t always recognize what that was.
In v3.0, service providers, specifically value-added resellers (VARs), also need to assign unique passwords, as well as employ two-factor authentication, to each of their merchants in order to remotely access the networks of those merchants. VARs often employ weak passwords or use one password to access multiple networks, which makes it easier for fraudsters to breach multiple systems.
The PCI SSC is trying to at least make it more difficult for the bad guys to break into one site and then move to the hub, so to speak, and then go to all the other different spokes with the same attack.
Overall, v3.0 is more granular by more accurately matching appropriate security controls to specific types of merchants, even though the approach may add complexity to merchants’ compliance obligations. On the whole a lot of these changes are very positive.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: (PCI SSC), call centers, cardholder data, consumers, credit-card, customers, data breaches, data security assessments, Data Security Standard, e-commerce breaches, e-commerce businesses, e-commerce merchant's website, electronic payments, global data security, global standard, Merchant's, merchant’s website, mobile, networks, payment, payment card data, Payment Card Industry, payment providers, PCI Security Standards Council, PCI-DSS, Penetration testing, Service providers, shopping cart, software solutions, web hosting, website
September 23rd, 2014 by Elma Jane
Home Depot, US retail chain says that 56 million payment cards are at risk following a malware-laden cyber-attack on eftpos tills across its stores in the US and Canada.
The investigation into a possible breach began on September 2nd,Tuesday morning, immediately after Home Depot received reports from its banking partners and law enforcement that criminals may have breached its systems.
According to Home Depot’s security partners, the malware had not been seen previously in other attacks.
Criminals used unique, custom-built malware to evade detection. The cyber-attack is estimated to have put payment card information at risk for approximately 56 million unique payment cards, after lurking in the company’s eftpos tills for four months between April and September.
While the breach has been seen as a further proof-point in the US push to adopt Chip and PIN at the point-of-sale, the fact that the outbreak also hit the home improvement chain’s Canadian stores, where the EMV standard has been implemented, leaves pause for thought. Nonetheless, the retailer has committed to installing 85,000 PIN pads at its US outlets, well ahead of the national 2015 deadline.
Home Depot has set aside $65 million to cover the cost to investigate the data breach, provide credit monitoring services to its customers, increase call center staffing, and pay legal and professional services. Approximately $27 million of the projected outlay will be covered by the company’s insurance.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale Tagged with: banking partners, Breach, call center, card information, cards, Chip and PIN, credit monitoring, credit monitoring services, customers, cyber-attack, data breach, EMV, EMV standard, Malware, payment, payment card information, payment cards, PIN pads, point of sale, risk
September 22nd, 2014 by Elma Jane
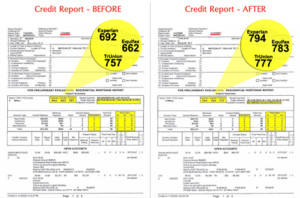
Consumers know how hard it is to obtain a credit card, if your credit score isn’t up to par. A bad credit score can prevent you from getting credit and make it hard to purchase your day to day necessities. People with poor credit don’t know their options. There are a number of ways to get a credit card if you have a poor credit score. There will likely be road blocks and limitations in your search. You won’t have the same options available as someone with pristine credit. But you will be able to get a line of credit if you look in the right place.
COSIGNED CREDIT CARDS If you get a cosigner, you will be able to obtain a card that would not be available to you otherwise. The cosigner has to have good credit, and they are responsible for your debt if you can’t pay. Make sure your cosigner fully recognizes their obligations and what will happen if you are unable to pay.
GIVE AN EXPLANATION FOR POOR CREDIT Explain the circumstances behind your poor credit. You can add a 100-word statement to your credit report such as the loss of a job. If you can tell your story and convince creditors you are on the road to increasing your credit score, they may believe you are more likely to pay back your debts. Divorce and illness are two other instances where individuals may see a drop in their credit score. Make sure whatever you list is true.
IMPROVE YOUR CREDIT One of the most difficult options. Poor credit can seem extremely hard to repair. But there are choices, it is just a process that will take a significant period of time. If you have poor credit, you can open bank accounts and pay off your loans and credit cards on time. If you pay off your debt in a timely manner, your credit score will improve over time and you will gain access to more credit card options.
RETAIL STORE CARDS Retail stores often have store credit cards they offer customers. Retail stores are generally more willing to approve applicants without a stellar credit score. But these cards usually come with extremely high interest rates and relatively low credit limits, so make sure you fully understand the terms of the card before applying.
SECURED CREDIT CARDS You deposit some money into an account, and then a creditor will provide you with a line of credit equal to your deposit. It is essentially a down payment, and if you don’t pay your credit card bill, your creditor is entitled to the money in the account. This might not sound like a favorable position, but remember that secured credit cards can be used as a valuable tool to rebuild your credit. Make sure the card you apply for reports to a credit reporting agency. This will help you start building a credit history. SELECT A CREDIT
CARD DESIGNED FOR THOSE WITH POOR CREDIT There are a number of credit cards offered by Visa and MasterCard designed for people with poor credit. These cards have low limits, a significant number of fees and high interest rates. But for some people, it may be their best option. Talk to your bank’s administrators or with your current credit card company to see if they offer a credit card that fits your personal needs.
SUBPRIME CREDIT CARDS Another option for those with poor credit, but they are ripe with fees that many people who are already short on cash may not be able to handle. Interest rates can be dangerously high for those with poor credit, so beware of these cards. They are often a last resort for individuals who need access to credit. However, like secured credit cards, they can be used to rebuild credit. Make sure you read the fine print and understand the applicable fees before you apply for a subprime credit card. Again, make sure the card reports to a credit reporting agency so you start building a credit history. Finding a line of credit doesn’t have to be a difficult endeavor. If you know what you are looking for, you can find a line of credit that fits your personal needs without breaking the bank. There are limitations, as well as pros and cons, to many of the forms of credit available to those with poor credit scores, such as secured credit cards or subprime credit cards. But those options do give people choices they otherwise may not have, and they help you build credit, so that eventually you will have a greater number of options.
Posted in Best Practices for Merchants Tagged with: account, applicants, card, consumers, COSIGNED CREDIT CARDS, credit, credit card bill, credit history, credit limits, credit report, credit score, credit-card, creditor, customers, deposit, down payment, good credit, interest rates, low credit limits, MasterCard, payment, poor credit, RETAIL STORE CARDS, retail stores, SECURED CREDIT CARDS, store credit cards, SUBPRIME CREDIT CARDS, visa, Visa and MasterCard
September 10th, 2014 by Elma Jane
Merchant go into business to make a sale. They go to great length to advertise their business and then they make a sale and don’t track it… They don’t track the very customer they went into business to attract…That seems crazy…But now more companies are embracing the practice of collecting email addresses at the point of sale (POS) and they’re doing so with increasing regularity. An example, when customers are at the cash register, many brick-and-mortar stores now offer to email them receipts
Confidently collect email addresses at POS:
Your email service provider should be able to implement a text-to-join acquisition program for you that executes quickly and can be built specifically to mitigate the risks around POS data collection.
Instead of relying on sales associates to accurately input email addresses, your customers can use SMS to text their email addresses to your short code.
Customers receive an immediate SMS reply message letting them know to check their email for their receipt.
A mobile-optimized receipt is immediately emailed to the address.
This can be followed by an email inviting customers to join your company’s email program. Offering a purchase discount can increase opt-ins. New joiners can be sent an age verification email, if relevant.
Your welcome email, including discount coupon, is sent and the relationship starts off on the right foot.
Increasing your confidence about POS email address collection, a text-to-join program can increase your acquisition rates. It can engage those customers who prefer to provide their information privately via their mobile devices. It can help protect companies against potential blacklisting because of typos and confirmed opt-ins. It can even reduce overhead costs by saving sales associates valuable time. Understanding these important email address collection issues and adopting the prescribed best practices are critical to ensuring customers have a safe, positive and valuable experience with your company at the point of sale and beyond.
Virtual Merchant can collect data too, and as a provider we can help merchant use that data. We are committed to providing appropriate protection for the information that is collected from customers who visit the website and use the Virtual Merchant payment system. Policy Privacy is updated from time to time.The website is provided to our customers as a business service and use of the site is limited to customers only.
If the merchant never makes a sale before 10 why do they open at 9 ?? This is only one small example on how collecting data first and then analyzing that data can shape businesses and find money you may be throwing away ….
Posted in Best Practices for Merchants, Mobile Point of Sale, Point of Sale Tagged with: brick and mortar, business, cash, cash register, customers, data, discount, discount coupon, email, merchant, mobile, Mobile Devices, payment, payment system, point of sale, policy, POS, provider, purchase, Rates, receipts, sale, service, sms, store's, virtual merchant, website
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services
September 5th, 2014 by Elma Jane
A cup of coffee, a pack of chewing gum., a newspaper at the airport. For even the smallest, most casual purchase, credit cards and debit cards are replacing cash as the preferred form of payment. One in three usually uses a credit card or a debit card for in-person purchases of less than $5. Eleven percent prefer credit cards, 22% debit cards and 65% cash, but the generational divide is striking. A slight majority (51 percent) of consumers 18-29 prefer plastic to cash, the only age group to do so. A preference for cash becomes stronger in each advancing age bracket, until at age 65-plus, 82 percent prefer cash.
Survey conducted by landline and cellphone found that: Credit cards and debit cards are used more frequently for small purchases by those employed full time (42%) or part time (34%) than for the unemployed (23%). People with children are more likely to use the cards for small purchases (41%) than those without children (30%), perhaps because parents have less time to wait around for change. Income doesn’t seem to be much of a differentiator, except for those near the bottom of the scale. A combined 38% of those making $75,000 or more preferred plastic for small purchases, compared with 43 percent of those making $50,000 to $74,900, 32% of those earning $30,000 to $49,900 and only 23% percent of those making less than $30,000.
Politically, we’ve finally found something on which we all can agree. Thirty percent of Democrats and a nearly identical 28% of Republicans favor credit cards or debit cards rather than cash for small purchases. Interestingly, those describing themselves as politically independent also were more independent from cash, 40% of them prefer plastic for such transactions.
The casual use of plastic is moving steadily through age brackets and already has a firm grip not only on millennials, but also increasingly on Gen Xers. Crunched another way, the data show that if you’re 49 or younger, you’re almost as likely to pay for a $5 purchase with plastic as you are to pay with cash. Fifty two percent prefer cash, 46% prefer debit or credit cards. Now, if you’re 50 or older, you’re still somewhat unlikely to pay for a $5 purchase with plastic. Seventy seven percent still prefer cash, with 21% reaching for debit cards or credit cards. Those who graduated from or attended college are significantly more comfortable than others with using plastic for small purchases.
A combined 39% of those with college degrees prefer debit cards (21%) or credit cards (18%) over cash (59%). Only 16% of those who have not attended college usually use debit cards for purchases of less than $5, along with only 6 percent who prefer credit cards for that purpose.
The trend is clear. Regardless of some differences in magnitude based on demographic factors, plastic is replacing cash as the currency of choice even for small purchases. Plastic use will increase for small purchases, both for debit and credit cards.
Why the shift to cards There are many reasons:
Technological advancements at the point of sale have made it just as fast to pay by plastic as by cash. Rewards have become a common feature of credit cards, with two out of three credit cards offering rewards, encouraging rewards chasing. Debit cards, with their balances available instantly and online have largely replaced paper checks and tedious manual records.
Financial institutions have spent decades persuading consumers to use and merchants to accept cards universally. Small purchases represent particularly appropriate uses of a debit card, assuming you don’t get carried away and overdraw the card-linked bank account. Why keep going to the bank and then carry cash if you don’t have to? Moving away from cash and moving toward using cards for even small purchases is more convenient.
Debit cards are everywhere already, but because their use can’t be reported to the credit bureaus and thus, they don’t build credit, they should only be used as a matter of convenience. People who frequently use credit cards for small, casual purchases also could overdo it, but probably not to a great degree. It would take a lot of lattes to send someone into credit counseling or bankruptcy court. In truth, we like the idea of using credit cards frequently for small, manageable expenses. This gives users the benefit of an active credit history, but leaves them with monthly bills that are small enough to pay off in full, so they don’t have to pay any interest. It’s getting to the point where, if I’m out and about, I’m using plastic the whole time. It’s just so much easier.
Posted in Best Practices for Merchants Tagged with: account, bank, bank account, bankruptcy, bills, cards, cash, cellphone, credit, credit counseling, credit history, data, debit cards, financial, financial institutions, Merchant's, payment, transactions
September 4th, 2014 by Elma Jane
EMV, which stands for Europay, MasterCard and Visa, and is slated to be mandated across the United States starting in October 2015 and automated fuel dispensers have until October 2017 to comply. Unlike magnetic swipe cards, EMV chip cards encrypt data and authenticate communication between the card and card reader. Additionally, chip card user is prompted for a PIN for authentication.
Why are those dates important? Companies lose $5.33 billion to fraud today, with card issuers and merchants incurring 63 and 37 percent of these losses, respectively. Under the EMV mandate, merchants who do not process chip cards will bear the burden of the issuer loss. By accepting chip card transactions, merchants and issuers should see a reduction in fraud.
Overcoming Barriers to EMV Adoption
Given the significant barriers to EMV adoption, it may be tempting for merchants to meet minimum requirements for accepting EMV payments. However, medium to large retailers should also consider the bigger picture of customer security and peace of mind.
Some key critical success factors for a payment initiative of this size include:
Business Continuity Architecture: As with all payment systems, it is imperative to have the EMV system running at all times. The solution should preferably have Active-Active architecture across multiple data centers and have a low Recovery Point Objective (the point in time to which the systems and data must be recovered after an outage).
Cost Benefit Analysis: Take a top down approach and decide accordingly on the scope of the analysis. This will ensure that decisions on scope are made on basis of quantitative data and not just qualitative arguments.
Phased Approach: To overcome time or cost overage in a project of this scope and complexity, retailers should try using an iterative approach for development. The rollout can be divided into multiple releases of six to seven months, which will provide the opportunity to review, capture lessons learnt, and improve subsequent releases.
Proactive Monitoring Alerts: Considering the criticality of business function carried out by EMV, tokenization and payment gateway, a vigorous supervising environment must be defined to perform proactive and reactive monitoring. It should take into consideration the monitoring targets, tools, scope and methods. This will provide advance visibility to the failure points and better ensuring maximum system availability.
Resilience Testing: Typically in a software project, the testing is limited to the unit, integration, performance and user acceptance. However, due to the critical nature of the applications and systems involved, robust resiliency testing is vital. This will ensure that there are no single points of failure and the system remains available when running in error conditions.
Stakeholder Identification: This is a key step to ensure that you have varied perspectives from all departments and their support. It will keep your organization from being blindsided and reduce the risk of disagreements in later stages of the program. Key stakeholders should include Store Operations, Card Accounting, Loss Prevention, Contact Center and IT & Data Security.
Organizations should adopt a five step approach to implement a secure, robust and industry-leading payment solution:
Encryption – Point to point encryption will ensure card data is secure and encrypted from the point of capture to the processor. Usually, merchants use data encryption that is not point to point, rendering their organization vulnerable to data breaches. Software encryption is the most common form of encryption, as it is easily installed and quires little or no hardware upgrades; however, it is less secure, may expose encryption keys, and is prone to memory scanning attacks. Hardware encryption is considered more secure but requires more costly terminal upgrades. Hardware encryption is designed to self-destruct the keys if tampered, but is not well-defined as very limited headway has been made in this space.
Tokenization – Build a Card Data Environment (CDE) that will host a centralized card data storage solution. Only limited applications with firewall access and capability to mutually authenticate via certificates can access CDE and receive card data. The rest of the applications will have tokens which are random numbers. This architecture will ease the merchant’s burden with existing and emerging PCI Data Security Standards.
Payment Gateway – Perform a risk assessment on the current payment gateway and identify gaps in functionality, manageability, compliance, scalability, speed to market and best practices. Determine the alternatives to mitigate the risks. Some of the important aspects of a leading payment gateway solution are support for all forms of credit, debit, gift cards and check transactions. Its ability to work with any acquirer, in-built encryption abilities, support for settlement and reconciliation must also be kept into consideration.
Settlement, Funding and Reconciliation – A workflow-based system to handle chargebacks and the automation of chargeback processing will greatly reduce labor-intensive work and enhance the quality of data used for settlement and reconciliation. Upgrades to the existing receipt retrieval system may be needed.
Card fraud is on the rise in the U.S., and merchants are the primary target for stealing information. With the EMV deadline just over a year away, the responsible retailer must take steps to prepare now. Although EMV implementation might seem overwhelming to merchants, they should start their journey to secure payments rather than wait for a looming deadline. Solutions such as data encryption and tokenization should be used in combination with EMV to implement a robust payment solution to better protect merchants against fraud. By proactively adopting EMV payment solutions, merchants can stay ahead of the regulatory curve and better protect their customers from fraud.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: authentication, automation, card, card data, Card Data Environment, card fraud, card issuers, card transactions, CDE, chargeback, chargeback processing, check, check transactions, chip, chip cards, credit, customer, customer security, data, data breaches, data encryption, data security, debit, EMV, emv chip cards, EuroPay, fraud, gateway, Gift Cards, host, integration, magnetic swipe cards, MasterCard, Merchant's, payment, payment gateway, payment solution, payment systems, PCI, PCI Data Security Standards, PIN, processor, retailers, Security, software, swipe, terminal, tokenization, tools, visa
September 2nd, 2014 by Elma Jane
While Apple doesn’t talk about future products,latest report that the next iPhone would include mobile-payment capabilities powered by a short-distance wireless technology called near-field communication or NFC. Apple is hosting an event on September 9th, that’s widely expected to be the debut of the next iPhone or iPhones. Mobile payments, or the notion that you can pay for goods and services at the checkout with your smartphone, may finally break into the mainstream if Apple and the iPhone 6 get involved.
Apple’s embrace of mobile payments would represent a watershed moment for how people pay at drugstores, supermarkets or for cabs. The technology and capability to pay with a tap of your mobile device has been around for years, you can tap an NFC-enabled Samsung Galaxy S5 or NFC-enabled credit card at point-of-sale terminals found at many Walgreen drugstores, but awareness and usage remain low. Apple has again the opportunity to transform, disrupt and reshape an entire business sector. It is hard to overestimate what impact Apple could have if it really wants to play in the payments market.
Apple won’t be the first to enter the mobile-payments arena. Google introduced its Google Wallet service in May 2011. The wireless carriers formed their joint venture with the intent to create a platform for mobile payments. Apple tends to stay away from new technologies until it has had a chance to smooth out the kinks. It was two years behind some smartphones in offering an iPhone that could tap into the faster LTE wireless network. NFC was rumored to be included in at least the last two iPhones and could finally make its appearance in the iPhone 6. The technology will be the linchpin to enabling transactions at the checkout.
Struggles
The notion of turning smartphones into true digital wallets including the ability to pay at the register, has been hyped up for years. But so far, it’s been more promise than results. There have been many technical hurdles to making mobile devices an alternative to cash, checks, and credit cards. NFC technology has to be included in both the smartphone and the point-of-sale terminal to work, and it’s been a slow process getting NFC chips into more equipment. NFC has largely been relegated to a feature found on higher-end smartphones such as the Galaxy S5 or the Nexus 5. There’s also confusion on both sides, the merchant and the customer, on how the tech works and why tapping your smartphone on a checkout machine is any faster, better or easier than swiping a card. There’s a chicken-and-egg problem between lack of user adoption and lack of retailer adoption. It’s one reason why even powerhouses such as Google have struggled. Despite a splashy launch of its digital wallet and payment service more than three years ago, Google hasn’t won mainstream acceptance or even awareness for its mobile wallet. Google hasn’t said how many people are using Google Wallet, but a look at its page on the Google Play store lists more than 47,000 reviews giving it an average of a four-star rating.
The Puzzle
Apple has quietly built the foundation to its mobile-payment service in Passbook, an app introduced two years ago in its iOS software and released as a feature with the iPhone 4S. Passbook has so far served as a repository for airline tickets, membership cards, and credit card statements. While it started out with just a handful of compatible apps, Passbook works with apps from Delta, Starbucks, Fandango, The Home Depot, and more. But it could potentially be more powerful. Apple’s already made great inroads with Passbook, it could totally crack open the mobile payments space in the US. Apple could make up a fifth of the share of the mobile-payment transactions in a short few months after the launch. The company also has the credit or debit card information for virtually all of its customers thanks to its iTunes service, so it doesn’t have to go the extra step of asking people to sign up for a new service. That takes away one of the biggest hurdles to adoption. The last piece of the mobile-payments puzzle with the iPhone is the fingerprint recognition sensor Apple added into last year’s iPhone 5S. That sensor will almost certainly make its way to the upcoming iPhone 6. The fingerprint sensor, which Apple obtained through its acquisition of Authentic in 2012, could serve as a quick and secure way of verifying purchases, not just through online purchases, but large transactions made at big-box retailers such as Best Buy. Today, you can use the fingerprint sensor to quickly buy content from Apple’s iTunes, App and iBooks stores.
The bigger win for Apple is the services and features it could add on to a simple transaction, if it’s successful in raising the awareness of a form of payment that has been quietly lingering for years. Google had previously seen mobile payments as the optimal location for targeted advertisements and offers. It’s those services and features that ultimately matter in the end, replacing a simple credit card swipe isn’t that big of a deal.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Smartphone Tagged with: app, Apple, card, card swipe, cash, checkout machine, checks, chips, credit, credit card swipe, credit-card, customer, debit card, Digital wallets, fingerprint recognition, fingerprint sensor, Galaxy S5, Google Wallet, iOS, Iphone, market, merchant, mobile, mobile device, mobile payment, mobile wallet, Near Field Communication, network, Nexus 5, nfc, payment, payment service, platform, point of sale, products, sensor, services, smartphone, software, statements, swiping card, terminals, transactions, wireless technology
August 28th, 2014 by Elma Jane
The new ECB regulation, which came into force earlier this month, covers large-value and retail payment systems in the euro area operated by both central banks and private entities. The aim is to promote the smooth operation of safe and efficient payment systems through strong management of legal, credit, liquidity, operational, general business, custody, and investment risks. In identifying systemically important payment systems, the ECB looked at the value of payments settled, market share, cross-border relevance and provision of services to other infrastructures. If a system is deemed to meet at least two of these four criteria it makes the list.
Target2 – operated by the Eurosystem.
Euro1 and Step2-T – both run by EBA Clearing.
Core(Fr) – French bank joint initiative, have been identified.
The list will be reviewed annually based on updated data. With this regulation, Europe is consolidating international practice for the oversight of Sips into EU law, as with past efforts for other financial market infrastructures, such as the European Market Infrastructure Regulation for the supervision of central counter parties and trade repositories and the ongoing regulatory initiative for central securities depositories.
Posted in Financial Services Tagged with: bank, central banks, credit, data, depositories, financial market, payment, payment systems, retail payment, securities