September 10th, 2014 by Elma Jane
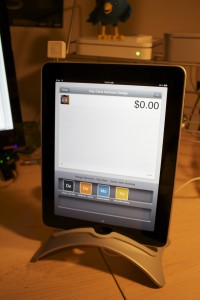
If your businesses considering an iPad point-of-sale (POS) system, you may be up for a challenge. Not only can the plethora of providers be overwhelming, but you must also remember that not all iPad POS systems are created equal. iPad POS systems do more than process payments and complete transactions. They also offer advanced capabilities that streamline operations. For instance, they can eliminate manual data entry by integrating accounting software, customer databases and inventory counts in real time, as each transaction occurs. With these systems, you get 24/7 access to sales data without having to be in the store. The challenge, however, is knowing which provider and set of features offer the best iPad POS solution for your business. iPad POS systems vary in functionality far more than the traditional POS solutions and are often targeted at specific verticals rather than the entire market. For that reason, it’s especially important to compare features between systems to ultimately select the right system for your business.
To help you choose a provider, here are things to look for in an iPad POS system.
Backend capabilities
One of the biggest benefits of an iPad POS system is that it offers advanced features that can streamline your entire operations. These include backend processes, such as inventory tracking, data analysis and reporting, and social media integration. As a small business, two of the most important time saving and productivity-boosting features to look for are customer relationship management (CRM) capabilities and connectivity to other sales channels. You’ll want an iPad POS that has robust CRM and a customizable customer loyalty program. It should tell you which products are most and least frequently purchased by specific customers at various store locations. It should also be able to identify the frequent VIP shoppers from the less frequent ones at any one of your store locations, creating the ultimate customer loyalty program for the small business owner. If you own an online store or use a mobile app to sell your products and services, your iPad POS software should also be able to integrate those online platforms with in-store sales. Not only will this provide an automated, centralized sales database, but it can also help increase total sales. You should be able to sell effortlessly through online, mobile and in-store channels. Why should your customers be limited to the people who walk by your store? Your iPad POS should be able to help you sell your products through more channels, online and on mobile. E-commerce and mobile commerce (mCommerce) aren’t just for big box retailers.
Cloud-based
The functions of an iPad POS solution don’t necessarily have to stop in-store. If you want to have anytime, anywhere access to your POS system, you can use one of the many providers with advanced features that give business owners visibility over their stores, its records and backend processes using the cloud. The best tablet-based POS systems operate on a cloud and allow you to operate it from any location you want. An iPad POS provider, with a cloud-based iPad POS system, businesses can keep tabs on stores in real time using any device, as well as automatically back up data. This gives business owners access to the system on their desktops, tablets or smartphones, even when not inside their stores. Using a cloud-based system also protects all the data that’s stored in your point of sale so you don’t have to worry about losing your data or, even worse, getting it stolen. Because the cloud plays such a significant role, businesses should also look into the kind of cloud service an iPad POS provider uses. In other words, is the system a cloud solution capable of expanding, or is it an app on the iPad that is not dependent on the Internet? Who is the cloud vendor? Is it a premium vendor? The type of cloud a provider uses can give you an idea about its reliability and the functions the provider will offer.
Downtime and technical support
As a small business, you need an iPad POS provider that has your back when something goes wrong. There are two types of customer support to look for: Downtime support and technical support.
iPad POS systems are often cheaper and simpler than traditional systems, but that doesn’t mean you can ignore the product support needs. The POS is a key element of your business and any downtime will likely result in significant revenue loss. You could, for instance, experience costly downtime when you lose Internet connectivity. iPad POS systems primarily rely on the Web to perform their core functions, but this doesn’t mean that when the Internet goes down, your business has to go down, too. Many providers offer offline support to keep your business going, such as Always on Mode. The Always on Mode setting enables your business to continue running even in the event of an Internet outage. Otherwise, your business will lose money during a loss of connectivity. Downtime can also happen due to technical problems within the hardware or software. Most iPad POS providers boast of providing excellent tech support, but you never really know what type of customer service you’ll actually receive until a problem occurs.
Test the friendliness of customer service reps by calling or emailing the provider with questions and concerns before signing any contracts. This way, you can see how helpful their responses are before you purchase their solution. Your POS is the most important device in your store. It’s essentially the gateway to all your transactions, customer data and inventory. If anything happens to it, you’ll need to be comfortable knowing that someone is there to answer your questions and guide you through everything.
Grows with your business
All growing businesses need tech solutions that can grow right along with them. Not all iPad POS systems are scalable, so look for a provider that makes it easy to add on more terminals and employees as your business expands. Pay attention to how the software handles growth in sales and in personnel. As a business grows, so does it sales volume and the required software capabilities. Some iPad POS solutions are designed for very small businesses, offering very limited features and transactions. If you have plans for growth, look for a provider that can handle the changes in transactions your business will be going through. Find out about features and customization. Does the system do what you want it to do? Can it handle large volume? How much volume? What modules can you add, and how do you interface to third parties? You should also consider the impacts of physical expansion and adding on new equipment and employees. If there are plans in the future for you to open another store location, you’ll need to make sure that your point of sale has the capabilities of actually handling another store location without adding more work for you. If you plan on hiring more employees for your store, you’ll also want to know that the solution you choose can easily be learned, so onboarding new staff won’t take up too much of your time.
Security
POS cyber attacks have risen dramatically over the past couple of years, making it more critical than ever to protect your business. Otherwise, it’s not just your business information at risk, but also your reputation and entire operations. iPad POS system security is a bit tricky, however. Unlike credit card swipers and mobile credit card readers that have long-established security standards namely, Payment Card Industry (PCI) compliance — the criteria for the iPad hardware itself as a POS terminal aren’t quite so clear-cut. Since iPads cannot be certified as PCI compliant, merchants must utilize a point-to-point encryption system that leaves the iPad out of scope. This means treating the iPad as its own system, which includes making sure it doesn’t save credit-card information or sensitive data on the iPad itself. To stay protected, look for PCI-certified, encrypted card swipers.
Posted in Best Practices for Merchants, Mobile Point of Sale, Point of Sale Tagged with: (POS) systems, accounting, app, business, card, cloud-based, credit, credit card readers, credit-card, crm, customer, customer relationship management, customer support, data, data analysis, database, desktops, e-commerce, inventory, iPad Point-Of-Sale, loyalty program, mcommerce, mobile, mobile app, mobile commerce, online, online platforms, Payment Card Industry, payments, PCI, platforms, POS, POS solution, products, sales, Security, security standards, services, Smartphones, social media, software, tablets, terminal, transactions, web
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services
August 27th, 2014 by Elma Jane
Backoff malware that has attacked point of sale systems at hundreds of businesses may accelerate adoption of EMV chip and PIN cards and two-factor authentication as merchants look for ways to soften the next attack. Chip and PIN are a big thing, because it greatly diminishes the value of the information that can be trapped by this malware, said Trustwave, a security company that estimates about 600 businesses have been victims of the new malware. The malware uses infected websites to infiltrate the computing devices that host point of sale systems or are used to make payments, such as PCs, tablets and smartphones. Merchants can install software that monitors their payments systems for intrusions, but the thing is you can’t just have anti-virus programs and think you are safe. Credit card data is particularly vulnerable because the malware can steal data directly from the magnetic stripe or keystrokes used to make card payments.
The point of sale system is low-hanging fruit because a lot of businesses don’t own their own POS system. They rent them, or a small business may hire a third party to implement their own point of sale system. The Payment Card Industry Security Standards Council issued new guidance this month to address security for outsourced digital payments. EMV-chip cards, which are designed to deter counterfeiting, would gut the value of any stolen data. With this magnetic stripe data, the crooks can clone the card and sell it on the black market. With chip and PIN, the data changes for each transaction, so each transaction is unique. Even if the malware grabs the data, there not a lot the crooks can do with it. The EMV transition in the U.S. has recently accelerated, driven in part by recent highprofile data breaches. Even with that momentum, the U.S. may still take longer than the card networks’ October 2015 deadline to fully shift to chip-card acceptance.
EMV does not by itself mitigate the threat of breaches. Two-factor authentication, or the use of a second channel or computing device to authorize a transaction, will likely share in the boost in investment stemming from data security concerns. The continued compromise of point of sale merchants through a variety of vectors, including malware such as Backoff, will motivate the implementation among merchants of stronger authentication to prevent unauthorized access to card data.
Backoff has garnered a lot of attention, including a warning from the U.S. government, but it’s not the only malware targeting payment card data. It is not the types of threats which are new, but rather the frequency with which they are occurring which has put merchants on their heels. There is also an acute need to educate small merchants on both the threats and respective mitigation techniques.. The heightened alert over data vulnerability should boost the card networks’ plans to replace account numbers with substitute tokens to protect digital payments. Tokens would not necessarily stop crooks from infiltrating point of sale systems, but like EMV technology, they would limit the value of the stolen data. There are two sides to the equation, the issuers and the merchants. To the extent we see both sides adopt tokenization, you will see fewer breaches and they will be less severe because the crooks will be getting a token instead of card data.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security, Point of Sale Tagged with: access, account, account numbers, anti-virus programs, authentication, Backoff, card, card networks, chip, credit, Credit card data, credit-card, data, data breaches, devices, digital payments, EMV, magnetic stripe, Malware, Merchant's, Payment Card Industry, payments, PCs, PIN, PIN cards, point of sale, POS, POS system, programs, Security, security standards, Smartphones, software, system, tablets, tokenization, tokens, transaction, Trustwave, websites
February 18th, 2014 by Elma Jane
Payment Tokenization Standards
Tokenization is the process of replacing a traditional card account number with a unique payment token that is restricted in how it can be used with a specific device, merchant, transaction type or channel. When using tokenization, merchants and digital wallet operators do not need to store card account numbers; instead they are able to store payment tokens that can only be used for their designated purpose. The tokenization process happens in the background in a manner that is expected to be invisible to the consumer.
EMVCo – which is collectively owned by American Express, Discover, JCB, MasterCard, UnionPay and Visa – has announced that it is expanding its scope to lead the payments industry’s work to standardize payment tokenization. EMVCo says that the new specification will help provide the payments community with a consistent, secure and interoperable environment to make digital payments when using a mobile handset, tablet, personal computer or other smart device.
Key elements of EMVCo’s work include adding new data fields to provide richer industry information about the transaction, which will improve transaction efficiency and enhance the consumer and merchant payment experience by helping to prevent fraudulent card account use. EMVCo will also create a consistent approach to identify and verify the valid use of a token during payment processing including authorization, capture, clearing and settlement.
EMVCo’s announcement follows an earlier joint announcement from MasterCard, Visa and American Express that proposed an initial framework for industry collaboration to standardize payment tokenization. EMVCo says it will now build on this framework with collective input from all of its members and the industry as a whole.
Posted in Credit card Processing, Credit Card Reader Terminal, Credit Card Security, Digital Wallet Privacy, Electronic Payments, Financial Services, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: American Express, authorization, capture, card account numbers, clearing, data fields, device, digital payments, Digital Wallet, Discover, EMV, emvco, fraudulent card account, interoperable, jcb, MasterCard, merchant, mobile handset, payment, payment processing, payment token, secure, security standards, settlement, smart device, specification, standardize, tablet, token, tokenization, transaction, visa
October 21st, 2013 by Elma Jane
UL’s (Underwriter Laboratories) latest contribution to the future of payments has been accomplished through its three years of work with National Security, a French biometrics company that has created a commercially viable biometric technology solution for the point of sale.
The move positions UL and National Security at the forefront of an industry that is expected to expand by 140 percent to reach $12 billion in revenue over the next five years, potentially transforming online, mobile and in-store commerce by increasing the speed of transactions in the process.
Still, arguments can be made that biometric use at the point of sale will remain limited. Why does UL believe the market is right for biometrics, and how did it successfully ensure biometric payments will be ready for all parts of the payment process?
Why The Time Is Now For Biometrics
Consumer concerns regarding identity theft and violence are on the rise, and the solution according to many is a viable biometrics payment solution. Reports show that there is already strong demand in the U.S. and Asian markets for such products, and major research outlets have put their support behind the technology.
UL’s case study elaborates on the benefits illustrating how biometric data has been developed to be harder for hackers to infiltrate and compliant with EMV security standards.
Developing The Technology
UL’s work to ensure biometrics will remove friction at the POS has been extensive. For example, its latest case study profiles how UL developed the underlying technology to overcome challenges and work in harmony with wireless technologies such as bluetooth and Wi-Fi. Further, it explains how UL assessed the human health impact of National Security’s biometric solutions.
Posted in Credit card Processing, Electronic Payments, EMV EuroPay MasterCard Visa, Mobile Point of Sale, Near Field Communication, Point of Sale Tagged with: biometric, bluetooth, commerce, data, developing, EMV, future, hackers, identity theft, impact, in-store, mobile, online, payment process, payments, point of sale, POS, process, security standards, solution, speed, transactions, viable, Wi-Fi, wireless