July 7th, 2015 by Elma Jane
The global brand MasterCard is in the process of launching a pilot program with the help of Google, BlackBerry, Apple, Microsoft, and Samsung to boost security for online payments using facial recognition systems.
About 500 customers are trialing for the new features, participants will provide feedback based on their experience. The company will continue to refine the product until ready to launch. MasterCard confirmed that it is planning to eventually release the new biometric security system publicly.
The payments company is also in the process of securing agreements with two major banking institutions. If all goes as planned, the undisclosed financial establishments will likely participate in the launching of the new security option.
When consumers shop on the Internet, their banks need ways to verify their identities. So this particular product seamlessly integrates biometrics into the overall payments experience, a security expert at MasterCard said.
The system does not actually save a photo of the user during the verification process. Instead, it creates a map of the individual’s face. Afterwards, the map is turned into code, which is sent to MasterCard for confirmation. The facial recognition feature only kicks in when an individual makes an online purchase.
During checkout, users will be prompted to confirm their identity using fingerprint scanning or facial detection.
To prevent criminals from using a photo to dupe the verification process, a user is required to blink once while having his or her face scanned. Technical specifications and mobile requirements for the security feature are still unknown.
With the test of facial recognition, MasterCard seemingly hopes to move away from password-based protocols by providing additional security options for consumers.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Smartphone, Visa MasterCard American Express Tagged with: consumers, financial establishments, MasterCard, online payments, payments, payments company, products, Security
May 19th, 2015 by Elma Jane
We’re now nearly midway through 2015, and payment security still remains a topic that stirs up great concern and confusion. While there is seemingly unanimous agreement on the need for heightened security, there’s uncertainty about those who are tasked with actually implementing it. Let’s dig deeper into EMV, P2PE and tokenization. How each will play a part in the next generation of securing payments, and how without properly working together they might just fall short.
Europay, MasterCard, and Visa (EMV) – A powerful guard against credit card skimming. EMV also uses cryptography to create dynamic data for every transaction and relies on an integrated chip embedded into the card.
Downside: For Independent Software Vendor (ISVs), the biggest downside of EMV is the complexity of creating an EMV solution. ISVs interested in certifying PINpads with a few processors face up to 22 months of costly work, and because there are a large number of pending certifications, processors will be backed up over the next few years.
It’s not impossible for an ISV to build EMV solutions in-house, but it’s difficult and unnecessary when there are plug-and-play EMV solutions available. These solutions include pre-packaged and pre-certified APIs that remove most of the need for research, the complexity and the burden of time and cost.
Point to Point Encryption (P2PE) – Secures devices, apps and processes using encrypted data with cryptographic keys only known to the payment company or gateway from the earliest point of the transaction, from tech-savvy criminals, jumping at their chance to intercept POS systems and scrape the memory from Windows machines.
How does a key get into card reader? Through an algorithm called derived unique key per transaction (DUKPT), or “duck putt.” DUKPT generates a base key that’s shared with device manufacturers securely, where output cardholder data is rendered differently each time a card is swiped, making it impossible to reverse engineer the card data. P2PE not only benefits the cardholders, but also the ISVs and merchants. PA-DSS certification was designed to address the problems created with cardholder data which is not encrypted.
Downside: P2PE isn’t cheap if an organization wants to do it in-house. The secure cryptographic device needed to manage the keys, Hardware Security Module (HSM), can cost $30-40,000 but when it’s built out, that total cost can jump to $100,000.
TOKENIZATION – The best way to protect cardholder data when it’s stored is using tokenization, a process which the PCI Security Standards Council describes as one where the primary account number is replaced with a surrogate value a token. For merchants dealing with recurring billing, future payments, loyalty programs and more, tokenization is critical.
Downside: Tokenization doesn’t prevent malware that’s remotely installed on POS devices. It’s possible, as seen with recent retail card breaches, for data to be stolen before it is tokenized. That’s why it’s essential to group tokenization together with P2PE and EMV to offer optimal security.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: (POS) systems, account number, billing, card, card breaches, card reader, cardholder, cardholder data, chip, credit card, data, DSS, EMV, EuroPay, gateway, Independent Software Vendor, ISVs, MasterCard, merchants, p2pe, payment company, payment security, payments, PCI, PINpads, point-to-point encryption, POS devices, processors, Security, security standards council, token, tokenization, transaction, visa
May 14th, 2015 by Elma Jane
The way customers Pay In Stores Is Changing.
Chip cards are here to provide advanced security with every transaction. Accepting chip cards could be as simple as changing your payment terminal.
What do you need to know about Chip Card and EMV? Chip cards are payment cards that have an embedded chip, which offers advanced security when you use the card to pay in store. Chip cards are based on a global card payment standard called EMV (Europay, MasterCard and VISA) currently used in more than 80 countries.
Why Is it More Secured? Chip card transactions offer you advanced security for in store payments by making every transaction unique, and, more difficult to counterfeit or copy. If the card data and the one-time code are stolen, the information cannot be used to create counterfeit cards and commit fraud.
How do you know if a customer has a Chip Card? The customer’s card will have chip on the front of it, magnetic stripe remains on the back.
How to use Chip Card at the POS? Swipe the card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. The customer should insert their card with chip toward terminal, facing up. The chip card should not be removed until the customer is prompted.
Customer will provide their signature or PIN as prompted by the terminal.
Some transactions may not require either.
When the terminal says the transaction is complete, the customer can remove their card.
Chip-enabled terminals will still accept magnetic stripe card payments for customers who do not have a chip card.
What does a chip-enabled terminal look like? They have all of the features you are used to with a payment terminal, with the addition of a slot for the customer to insert their card. The slot is typically located at the bottom or the top of the payment terminal.
How will you know if a terminal accepts chip card? During the transition to chip, customers are being told to swipe their card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. If you have chip-enabled terminals, you can tell your customer to insert their card for a chip transaction, if a customer has a chip card.
How can you get a chip-enabled terminal? Contact your acquirer or merchant service provider.
Show your customers that you care about their information security by making the move to chip. This will ensure that your business and your customers are protected from fraud. Start accepting chip cards!
You may be liable for fraud if you don’t make the change from chip terminal. Starting October 2015, rules are changing. Merchants that accept chip will be protected from fraud losses resulting from in store counterfeit magnetic stripe card transactions just as you are today. However, liability will shift from issuers to merchants if their payment terminals are not chip-enabled for in store transactions. Fraud liability for lost or stolen cards varies by payment network. Contact your acquirer or payment services providers for more information.
Posted in Best Practices for Merchants, Credit Card Reader Terminal, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Point of Sale Tagged with: card data, cards, chip cards, Chip-enabled terminals, data, EMV, EuroPay, magnetic stripe, MasterCard and VISA, merchant service provider, Merchant's, payment, payment cards, payment network, payment terminal, POS, Security, terminal, transaction
Biometrics Market To Reach $14.9 Billion by 2024
The Biometrics market currently sits at $2 billion, by 2024, it will reach $14.9 billion, with a cumulative total revenue of $67.8 billion. This is being driven by new advancements in Biometrics Hardware and Software that are not only transforming payments, but also serving as frictionless alternatives to security in a myriad of use cases.
For consumer facing security, Biometrics can be deployed at a low price-point for high-volume authentication. Think an iris scan or finger swipe for quickly unlocking a mobile device like an iPhone 6 or Samsung Galaxy S6.
The forecast goes over use cases that spans from Point-of-Sale transactions, to voter identification, making the case for Biometrics embedding itself into a vast number of aspects in everyday life.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Point of Sale, Smartphone Tagged with: biometrics, consumer, device, mobile, mobile device, payments, point of sale, Security, swipe, transactions
January 23rd, 2015 by Elma Jane
Technology and software are among the most important investments a company can make, especially when it comes to security. Growing demand for IT services and security solutions prove that business owners know the threats that are out there and want to do something to guard themselves against cybercriminals.
With a well-rounded security solution a business might purchased, and with all the recommended features a business might need, was the investment really worth it? Security solutions provider Trustwave, found that organizations of all sizes are wasting their security dollars and none more so than small businesses.
Small businesses spent an average of $157 per user on security software, compared with $73 per user in larger companies. Nearly 30 percent of that investment ended up underutilized or never used due to non- or misuse of security controls and features. And yet, companies still increased their spending by 44 percent.
Why did businesses end up letting their security software go partially to waste, despite significant increases in IT spending?
Many organizations cited a lack of resources: Either IT staff was too busy to implement their security solutions properly, or didn’t have the manpower to do so.
With the alarming number of high-profile corporate breaches, businesses of all sizes are aware that they need to invest in top-of-the-line solutions. IT professionals expect a 43 percent increase in their use of cloud-based or managed security services. But the financial constraints many small companies face can prove to be an obstacle to proper security.
A few IT-related tips to help save money, which can then be reallocated toward the technological and staffing resources needed to protect a business.
Monitor software usage and eliminate solutions that aren’t being used. Seek out products that are designed for small business. Some companies offer free or discounted versions of their product to very small companies. Track any IT/software purchases to ensure you’re within your budget.
Posted in Best Practices for Merchants Tagged with: breaches, Security, security software, services, software, solutions provider, technology
October 15th, 2014 by Elma Jane
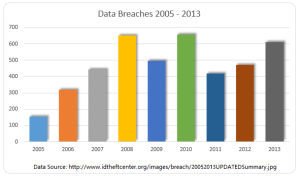
Another day, another corporate data breach. Business owners are now aware that cyber criminals are becoming increasingly smart and sophisticated in their hacking methods, and they can target just about anyone. But smaller companies that think, It can’t happen, or they are too small for hackers to notice, may be setting themselves up for a devastating data breach.
Large corporations typically have a lot more money and resources to invest in IT security, whereas small to medium businesses do not have the IT staffing, resources, money or know-how to put effective security measures into place to combat security vulnerabilities.
If a small business owner is responsible for security practices, it’s going to fall to the lower end of the priority list. The business will have less protections in place and hackers recognize that. Criminals are looking for unlocked doors.
Recent research found that more than half of all small and midsize businesses have been hacked at some point, and nearly three-quarters weren’t able to restore all the lost data. The two most common methods of attack are phishing, gathering sensitive information by masquerading as a trusted website and watering holes. Installing malware on commonly used websites of a target group. These tactics, grant cyber criminals access to the information that leads to identity theft and stolen credit card information.
A credit card breach is fairly easy to recognize once customers of a certain company all begin reporting fraudulent charges. But by that point, a breach has already done a significant amount of damage, not just to the consumers but to the company they trusted to protect their data.
A computer that appears to have been tampered with.If you turned off your computer when you left work and it’s on or has windows and programs running when you return, someone may have been trying to steal important information. This is an especially likely scenario with internal data theft, such as the AT&T breach. Keeping your machines password-protected and encrypting any sensitive data can prevent unauthorized individuals from accessing the information.
Locked-out accounts. If you’ve ever been locked out of your email or social media accounts, you know it’s usually because you typed the wrong login credentials one too many times. If you receive a lock-out message the first time you try to access an account (and you know you’ve typed your password correctly), you might have been hacked. This can mean that someone is attempting to brute force an account, or that an account has already been compromised and the password changed.
Unusually slow Internet or computers. This could be a sign of a compromised machine that is sending out lots of traffic, or that malware or a virus is on the machine. You should also look for pop-up ads (especially if you have an activated blocker) or websites that don’t load properly.
In all of these instances, minor inconveniences that most people might ignore if the problem seems to resolve itself could be signs of a much more serious problem. Both experts advised keeping your antivirus software, firewalls and device operating systems up-to-date, and always remaining alert for any suspicious activity.
Posted in Best Practices for Merchants Tagged with: consumers, credit card breach, credit card information, customers, data, data breach, device, Security, website
September 18th, 2014 by Elma Jane
Electronic invoicing is the exchange of the invoice document between a supplier and a buyer in an integrated electronic format. Traditionally, invoicing, like any heavily paper-based process, is manually intensive and is prone to human error resulting in increased costs and processing lifecycles for companies.
The issue of compliance seems to have separated E-Invoicing from B2B. Surprisingly many Finance leaders are unaware that their company is already sending/receiving EDI electronic invoices.
E-Invoicing is a common B2B practice and National Transaction is ready to launch its E-Invoicing system.
True definition of an electronic invoice is that it should contain data from the supplier in a format that can be entered integrated into the buyer’s Account Payable (AP) system without requiring any data input from the buyer’s AP administrator.
There are number of formats to be employed, it is useful to Apply below guidelines:
An E-Invoice:
1) Structured invoice data issued in Electronic Data Interchange (EDI) or XML formats.
2) Structured invoice data issued using standard Internet-based web forms.
Not a true E-Invoice:
1) Paper invoices sent via fax machines.
2) Scanned paper invoices.
3) Unstructured invoice data issued in PDF or Word formats.
Although significant cost and time savings can be achieved by removing paper and manual processing from your invoicing, the real benefits of E-Invoicing come with the level of security that comes with E-invoicing. Integration between your trading partners and your invoicing software and other business systems are optional. National Transaction can offer a customized Electronic Invoice Structure .
Posted in Best Practices for Merchants Tagged with: (AP), Account Payable, AP administrator, b2b, buyer, compliance, data, E-Invoice, E-Invoicing, E-Invoicing system, EDI, EDI electronic invoices, electronic data interchange, electronic format, electronic invoices, Electronic invoicing, Finance leaders, Internet-based web, invoice document, invoicing, National Transaction, Paper invoices, Security, supplier, web
September 10th, 2014 by Elma Jane
If your businesses considering an iPad point-of-sale (POS) system, you may be up for a challenge. Not only can the plethora of providers be overwhelming, but you must also remember that not all iPad POS systems are created equal. iPad POS systems do more than process payments and complete transactions. They also offer advanced capabilities that streamline operations. For instance, they can eliminate manual data entry by integrating accounting software, customer databases and inventory counts in real time, as each transaction occurs. With these systems, you get 24/7 access to sales data without having to be in the store. The challenge, however, is knowing which provider and set of features offer the best iPad POS solution for your business. iPad POS systems vary in functionality far more than the traditional POS solutions and are often targeted at specific verticals rather than the entire market. For that reason, it’s especially important to compare features between systems to ultimately select the right system for your business.
To help you choose a provider, here are things to look for in an iPad POS system.
Backend capabilities
One of the biggest benefits of an iPad POS system is that it offers advanced features that can streamline your entire operations. These include backend processes, such as inventory tracking, data analysis and reporting, and social media integration. As a small business, two of the most important time saving and productivity-boosting features to look for are customer relationship management (CRM) capabilities and connectivity to other sales channels. You’ll want an iPad POS that has robust CRM and a customizable customer loyalty program. It should tell you which products are most and least frequently purchased by specific customers at various store locations. It should also be able to identify the frequent VIP shoppers from the less frequent ones at any one of your store locations, creating the ultimate customer loyalty program for the small business owner. If you own an online store or use a mobile app to sell your products and services, your iPad POS software should also be able to integrate those online platforms with in-store sales. Not only will this provide an automated, centralized sales database, but it can also help increase total sales. You should be able to sell effortlessly through online, mobile and in-store channels. Why should your customers be limited to the people who walk by your store? Your iPad POS should be able to help you sell your products through more channels, online and on mobile. E-commerce and mobile commerce (mCommerce) aren’t just for big box retailers.
Cloud-based
The functions of an iPad POS solution don’t necessarily have to stop in-store. If you want to have anytime, anywhere access to your POS system, you can use one of the many providers with advanced features that give business owners visibility over their stores, its records and backend processes using the cloud. The best tablet-based POS systems operate on a cloud and allow you to operate it from any location you want. An iPad POS provider, with a cloud-based iPad POS system, businesses can keep tabs on stores in real time using any device, as well as automatically back up data. This gives business owners access to the system on their desktops, tablets or smartphones, even when not inside their stores. Using a cloud-based system also protects all the data that’s stored in your point of sale so you don’t have to worry about losing your data or, even worse, getting it stolen. Because the cloud plays such a significant role, businesses should also look into the kind of cloud service an iPad POS provider uses. In other words, is the system a cloud solution capable of expanding, or is it an app on the iPad that is not dependent on the Internet? Who is the cloud vendor? Is it a premium vendor? The type of cloud a provider uses can give you an idea about its reliability and the functions the provider will offer.
Downtime and technical support
As a small business, you need an iPad POS provider that has your back when something goes wrong. There are two types of customer support to look for: Downtime support and technical support.
iPad POS systems are often cheaper and simpler than traditional systems, but that doesn’t mean you can ignore the product support needs. The POS is a key element of your business and any downtime will likely result in significant revenue loss. You could, for instance, experience costly downtime when you lose Internet connectivity. iPad POS systems primarily rely on the Web to perform their core functions, but this doesn’t mean that when the Internet goes down, your business has to go down, too. Many providers offer offline support to keep your business going, such as Always on Mode. The Always on Mode setting enables your business to continue running even in the event of an Internet outage. Otherwise, your business will lose money during a loss of connectivity. Downtime can also happen due to technical problems within the hardware or software. Most iPad POS providers boast of providing excellent tech support, but you never really know what type of customer service you’ll actually receive until a problem occurs.
Test the friendliness of customer service reps by calling or emailing the provider with questions and concerns before signing any contracts. This way, you can see how helpful their responses are before you purchase their solution. Your POS is the most important device in your store. It’s essentially the gateway to all your transactions, customer data and inventory. If anything happens to it, you’ll need to be comfortable knowing that someone is there to answer your questions and guide you through everything.
Grows with your business
All growing businesses need tech solutions that can grow right along with them. Not all iPad POS systems are scalable, so look for a provider that makes it easy to add on more terminals and employees as your business expands. Pay attention to how the software handles growth in sales and in personnel. As a business grows, so does it sales volume and the required software capabilities. Some iPad POS solutions are designed for very small businesses, offering very limited features and transactions. If you have plans for growth, look for a provider that can handle the changes in transactions your business will be going through. Find out about features and customization. Does the system do what you want it to do? Can it handle large volume? How much volume? What modules can you add, and how do you interface to third parties? You should also consider the impacts of physical expansion and adding on new equipment and employees. If there are plans in the future for you to open another store location, you’ll need to make sure that your point of sale has the capabilities of actually handling another store location without adding more work for you. If you plan on hiring more employees for your store, you’ll also want to know that the solution you choose can easily be learned, so onboarding new staff won’t take up too much of your time.
Security
POS cyber attacks have risen dramatically over the past couple of years, making it more critical than ever to protect your business. Otherwise, it’s not just your business information at risk, but also your reputation and entire operations. iPad POS system security is a bit tricky, however. Unlike credit card swipers and mobile credit card readers that have long-established security standards namely, Payment Card Industry (PCI) compliance — the criteria for the iPad hardware itself as a POS terminal aren’t quite so clear-cut. Since iPads cannot be certified as PCI compliant, merchants must utilize a point-to-point encryption system that leaves the iPad out of scope. This means treating the iPad as its own system, which includes making sure it doesn’t save credit-card information or sensitive data on the iPad itself. To stay protected, look for PCI-certified, encrypted card swipers.
Posted in Best Practices for Merchants, Mobile Point of Sale, Point of Sale Tagged with: (POS) systems, accounting, app, business, card, cloud-based, credit, credit card readers, credit-card, crm, customer, customer relationship management, customer support, data, data analysis, database, desktops, e-commerce, inventory, iPad Point-Of-Sale, loyalty program, mcommerce, mobile, mobile app, mobile commerce, online, online platforms, Payment Card Industry, payments, PCI, platforms, POS, POS solution, products, sales, Security, security standards, services, Smartphones, social media, software, tablets, terminal, transactions, web
September 9th, 2014 by Elma Jane
The use of customer data can help you make smarter decisions that can improve your store, enhance the shopper experience, and increase conversions. When used incorrectly, however, data can waste resources and alienate your visitors.
Ways that ecommerce merchants commonly misuse data.
Collecting Unnecessary Data
Big Data analytics and reporting tools can put a lot of information in your hands, but that doesn’t mean you should collect and track every single metric. Don’t waste space and bandwidth collecting information that is not essential in your business. Unnecessary data can create noise that slows down the analytics process. Gathering and analyzing information you don’t need can distract you from the metrics that matter. Collecting too much data can create security headaches. The best defense against breaches is to not have data to steal. If you don’t need it, don’t collect it.
Determine your store’s key performance indicators before collecting any information. A good way of doing this is to examine each metric and ask yourself whether it’s just nice to know or is something that you can actually act on. While it may be nice to know that a particular customer has a high Klout Score, that metric probably won’t do anything for your bottom line. It’s better to not bother with it. Key metrics vary from one business to the next. For most ecommerce sites, the important metrics usually include conversion rate, traffic sources, and on-site browsing activities.
Creeping-out Shoppers
Most retailers do this inadvertently when they’re trying to customize the shopper experience. A certain amount of personalization can provide value and convenience to users, but you also have to draw the line between cool personalization and creepy. Sending emails with tailored product recommendations is a good way to increase conversions. But you have to be careful with how you execute it, so that you don’t appear too intrusive. The same goes for remarketing banner ads.
Ignoring Qualitative Information
Numbers can produce many insights, but focusing solely on that data can create an incomplete view of your company. Best data strategies make use of both quantitative and qualitative information. Go beyond the numbers to get the pulse of your customers by collecting feedback through social interactions, customer service logs, surveys with open-ended questions and more. Qualitative information can complement and validate the hard numbers.
Using Data to Justify a Decision or Hypothesis
When it comes to data collection, many merchants fall into the confirmation bias trap, wherein they interpret the information to confirm their existing beliefs or to justify their decisions. Using data this way causes you to ignore information or results that aren’t in line with your beliefs and could result in you missing opportunities. Say a company has so much faith in its new marketing strategy that when website traffic improves, the staff deems the campaign a success without looking at the conversion or retention rates. If the staff had ignored initial biases and looked at the big picture instead, they could have identified flaws and found ways to correct them. The key to addressing this is to have an open mind when interpreting information. This can be difficult, especially when you’re too close to your business. Consider a third-party specialist who can remain objective, to help make the right decisions.
Posted in Best Practices for Merchants, e-commerce & m-commerce Tagged with: breaches, business, conversion rate, customer, customer data, customer service, data, ecommerce, ecommerce merchants, Merchant's, rate, retention rates, Security, sources, tools, traffic
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services