Biometrics Market To Reach $14.9 Billion by 2024
The Biometrics market currently sits at $2 billion, by 2024, it will reach $14.9 billion, with a cumulative total revenue of $67.8 billion. This is being driven by new advancements in Biometrics Hardware and Software that are not only transforming payments, but also serving as frictionless alternatives to security in a myriad of use cases.
For consumer facing security, Biometrics can be deployed at a low price-point for high-volume authentication. Think an iris scan or finger swipe for quickly unlocking a mobile device like an iPhone 6 or Samsung Galaxy S6.
The forecast goes over use cases that spans from Point-of-Sale transactions, to voter identification, making the case for Biometrics embedding itself into a vast number of aspects in everyday life.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Point of Sale, Smartphone Tagged with: biometrics, consumer, device, mobile, mobile device, payments, point of sale, Security, swipe, transactions
October 15th, 2014 by Elma Jane
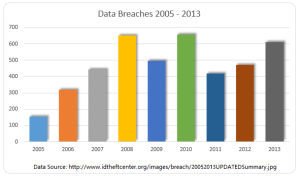
Another day, another corporate data breach. Business owners are now aware that cyber criminals are becoming increasingly smart and sophisticated in their hacking methods, and they can target just about anyone. But smaller companies that think, It can’t happen, or they are too small for hackers to notice, may be setting themselves up for a devastating data breach.
Large corporations typically have a lot more money and resources to invest in IT security, whereas small to medium businesses do not have the IT staffing, resources, money or know-how to put effective security measures into place to combat security vulnerabilities.
If a small business owner is responsible for security practices, it’s going to fall to the lower end of the priority list. The business will have less protections in place and hackers recognize that. Criminals are looking for unlocked doors.
Recent research found that more than half of all small and midsize businesses have been hacked at some point, and nearly three-quarters weren’t able to restore all the lost data. The two most common methods of attack are phishing, gathering sensitive information by masquerading as a trusted website and watering holes. Installing malware on commonly used websites of a target group. These tactics, grant cyber criminals access to the information that leads to identity theft and stolen credit card information.
A credit card breach is fairly easy to recognize once customers of a certain company all begin reporting fraudulent charges. But by that point, a breach has already done a significant amount of damage, not just to the consumers but to the company they trusted to protect their data.
A computer that appears to have been tampered with.If you turned off your computer when you left work and it’s on or has windows and programs running when you return, someone may have been trying to steal important information. This is an especially likely scenario with internal data theft, such as the AT&T breach. Keeping your machines password-protected and encrypting any sensitive data can prevent unauthorized individuals from accessing the information.
Locked-out accounts. If you’ve ever been locked out of your email or social media accounts, you know it’s usually because you typed the wrong login credentials one too many times. If you receive a lock-out message the first time you try to access an account (and you know you’ve typed your password correctly), you might have been hacked. This can mean that someone is attempting to brute force an account, or that an account has already been compromised and the password changed.
Unusually slow Internet or computers. This could be a sign of a compromised machine that is sending out lots of traffic, or that malware or a virus is on the machine. You should also look for pop-up ads (especially if you have an activated blocker) or websites that don’t load properly.
In all of these instances, minor inconveniences that most people might ignore if the problem seems to resolve itself could be signs of a much more serious problem. Both experts advised keeping your antivirus software, firewalls and device operating systems up-to-date, and always remaining alert for any suspicious activity.
Posted in Best Practices for Merchants Tagged with: consumers, credit card breach, credit card information, customers, data, data breach, device, Security, website
September 24th, 2014 by Elma Jane
The CVV Number (Card Verification Value) on your credit card or debit card is a 3 digit number on VISA, MasterCard and Discover branded credit and debit cards. On your American Express branded credit or debit card it is a 4 digit numeric code.
The codes have different names:
American Express – CID or unique card code.
Debit Card – CSC or card security code.
Discover – card identification number (CID)
Master Card – card validation code (CVC2)
Visa – card verification value (CVV2)
CVV numbers are NOT your card’s secret PIN (Personal Identification Number).
You should never enter your PIN number when asked to provide your CVV. (PIN numbers allow you to use your credit or debit card at an ATM or when making an in-person purchase with your debit card or a cash advance with any credit card.)
Types of security codes:
CVC1 or CVV1, is encoded on track-2 of the magnetic stripe of the card and used for card present transactions. The purpose of the code is to verify that a payment card is actually in the hand of the merchant. This code is automatically retrieved when the magnetic stripe of a card is swiped on a point-of-sale (card present) device and is verified by the issuer. A limitation is that if the entire card has been duplicated and the magnetic stripe copied, then the code is still valid.
The most cited, is CVV2 or CVC2. This code is often sought by merchants for card not present transactions occurring by mail or fax or over the telephone or Internet. In some countries in Western Europe, card issuers require a merchant to obtain the code when the cardholder is not present in person.
Contactless card and chip cards may supply their own codes generated electronically, such as iCVV or Dynamic CVV.
Code Location:
The card security code is typically the last three or four digits printed, not embossed like the card number, on the signature strip on the back of the card. On American Express cards, the card security code is the four digits printed (not embossed) on the front towards the right. The card security code is not encoded on the magnetic stripe but is printed flat.
American Express cards have a four-digit code printed on the front side of the card above the number.
MasterCard, Visa, Diners Club, Discover, and JCB credit and debit cards have a three-digit card security code. The code is the final group of numbers printed on the back signature panel of the card.
New North American MasterCard and Visa cards feature the code in a separate panel to the right of the signature strip. This has been done to prevent overwriting of the numbers by signing the card.
Benefits when it comes to security:
As a security measure, merchants who require the CVV2 for card not present payment card transactions are required by the card issuer not to store the CVV2 once the individual transaction is authorized and completed. This way, if a database of transactions is compromised, the CVV2 is not included, and the stolen card numbers are less useful. Virtual Terminals and payment gateways do not store the CVV2 code, therefore employees and customer service representatives with access to these web-based payment interfaces who otherwise have access to complete card numbers, expiration dates, and other information still lack the CVV2 code.
The Payment Card Industry Data Security Standard (PCI DSS) also prohibits the storage of CSC (and other sensitive authorization data) post transaction authorization. This applies globally to anyone who stores, processes or transmits card holder data. Since the CSC is not contained on the magnetic stripe of the card, it is not typically included in the transaction when the card is used face to face at a merchant. However, some merchants in North America require the code. For American Express cards, this has been an invariable practice (for card not present transactions) in European Union (EU) states like Ireland and the United Kingdom since the start of 2005. This provides a level of protection to the bank/cardholder, in that a fraudulent merchant or employee cannot simply capture the magnetic stripe details of a card and use them later for card not present purchases over the phone, mail order or Internet. To do this, a merchant or its employee would also have to note the CVV2 visually and record it, which is more likely to arouse the cardholder’s suspicion.
Supplying the CSC code in a transaction is intended to verify that the customer has the card in their possession. Knowledge of the code proves that the customer has seen the card, or has seen a record made by somebody who saw the card.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale, Visa MasterCard American Express Tagged with: (Card Verification Value), (CVC2), American Express, atm, authorization data, bank/cardholder, card holder data, card identification number, card issuers, Card Not Present transactions, card number, card numbers, card security code, card validation code, card-not-present, card-present transactions, cardholder, cards, cash advance, chip cards, CID, code, Contactless card, credit, credit-card, CSC, customer, customer service, CVC1, CVV Number, CVV1, CVV2, Data Security Standard, debit, debit card, debit cards, device, Diners Club, Discover, fax, gateways, iCVV or Dynamic CVV, individual transaction, internet, issuer, JCB credit, magnetic stripe, mail, MasterCard, merchant, payment card, Payment Card Industry, payment card transactions, payment gateways, PCI-DSS, Personal Identification Number, PIN, point of sale, post transaction authorization, security codes, telephone, terminals, unique card code, virtual terminals, visa, web-based payment
June 3rd, 2014 by Elma Jane
Apple announced new Touch ID API better known among the masses as fingerprint ID, which will allow app developers to use fingerprint authentication for mobile payments and other applications.
This means that in addition to protecting the mobile device itself, the technology can now be used also to secure individual applications on the device against unauthorized use. Customers could potentially use prints from different fingers to control different apps. For instance, right thumbprint for access to the device, left index finger for access to the mobile bank app within the device.
The new feature for third party software developers provides a logical progression for the removal of password protection across a range of applications, including payments.
Financial services providers who offer the convenience of a mobile application for their customers can now also offer said customers an additional layer of security for the information that application holds.
Posted in Credit Card Security, Mobile Payments, Smartphone Tagged with: app, Apple, bank, device, financial services, Financial services providers, fingerprint authentication, fingerprint ID, mobile, mobile application, mobile bank app, Mobile Payments, payments, Security, software, software developers, Touch ID API
May 21st, 2014 by Elma Jane
Mobile credit card processing is way cheaper than traditional point-of-sale (POS) systems. Accepting credit cards using mobile devices is stressful, not to mention a hassle to set up and customers would never dare compromise security by saving or swiping their credit cards on a mobile device. Some of the many myths surrounding mobile payments, which allow merchants to process credit card payments using smartphones and tablets. Merchants process payments using a physical credit card reader attached to a mobile device or by scanning previously stored credit card information from a mobile app, as is the case with mobile wallets. Benefits include convenience, a streamlined POS system and access to a breadth of business opportunities based on collected consumer data. Nevertheless, mobile payments as a whole remains a hotly debated topic among retailers, customers and industry experts alike.
Although mobile payment adoption has been slow, consumers are steadily shifting their preferences as an increasing number of merchants implement mobile payment technologies (made easier and more accessible by major mobile payment players such as Square and PayPal). To stay competitive, it’s more important than ever for small businesses to stay current and understand where mobile payment technology is heading.
If you’re considering adopting mobile payments or are simply curious about the technology, here are mobile payment myths that you may have heard, but are completely untrue.
All rates are conveniently the same. Thanks to the marketing of big players like Square and PayPal – which are not actually credit card processors, but aggregators rates can vary widely and significantly. For instance, consider that the average debit rate is 1.35 percent. Square’s is 2.75 percent and PayPal Here’s is 2.7 percent, so customers will have to pay an additional 1.41 percent and 1.35 percent, respectively, using these two services. Some cards also get charged well over 4 percent, such as foreign rewards cards. These companies profit & mobile customers lose. Always read the fine print.
Credit card information is stored on my mobile device after a transaction. Good mobile developers do not store any critical information on the device. That information should only be transferred through an encrypted, secure handshake between the application and the processor. No information should be stored or left hanging around following the transaction.
I already have a POS system – the hassle isn’t worth it. Mobile payments offer more flexibility to reach the customer than ever before. No longer are sales people tied to a cash register and counters to finish the sale. That flexibility can mean the difference between revenue and a lost sale. Mobile payments also have the latest technology to track sales, log revenue, fight chargebacks, and analyze performance quickly and easily.
If we build it, they will come. Many wallet providers believe that if you simply build a new mobile payment method into the phones, consumers will adopt it as their new wallet. This includes proponents of NFC technology, QR codes, Bluetooth and other technologies, but given very few merchants have the POS systems to accept these new types of technologies, consumers have not adopted. Currently, only 6.6 percent of merchants can accept NFC, and even less for QR codes or BLE technology, hence the extremely slow adoption rate. Simply put, the new solutions are NOT convenient, and do not replace consumers’ existing wallets, not even close.
It raises the risk of fraud. Fraud’s always a concern. However, since data isn’t stored on the device for Square and others, the data is stored on their servers, the risk is lessened. For example, there’s no need for you to fear one of your employees walking out with your tablet and downloading all of your customers’ info from the tablet. There’s also no heightened fraud risk for data loss if a tablet or mobile device is ever sold.
Mobile processing apps are error-free. Data corruption glitches do happen on wireless mobile devices. A merchant using mobile credit card processing apps needs to be more diligent to review their mobile processing transactions. Mobile technology is fantastic when it works.
Mobile wallets are about to happen. They aren’t about to happen, especially in developed markets like the U.S. It took 60 years to put in the banking infrastructure we have today and it will take years for mobile wallets to achieve critical mass here.
Setup is difficult and complicated. Setting up usually just involves downloading the vendor’s app and following the necessary steps to get the hardware and software up and running. The beauty of modern payment solutions is that like most mobile apps, they are built to be user-friendly and intuitive so merchants would have little trouble setting them up. Most mobile payment providers offer customer support as well, so you can always give them a call in the unlikely event that you have trouble setting up the system.
The biggest business opportunity in the mobile payments space is in developed markets. While most investments and activity in the Mobile Point of Sale space take place today in developed markets (North America and Western Europe), the largest opportunity is actually in emerging markets where most merchants are informal and by definition can’t get a merchant account to accept card payments. Credit and debit card penetration is higher in developed markets, but informal merchants account for the majority of payments volume in emerging markets and all those transactions are conducted in cash today.
Wireless devices are unreliable. Reliability is very often brought up as I think many businesses are wary of fully wireless setups. I think this is partly justified, but very easily mitigated, for example with a separate Wi-Fi network solely for point of sale and payments. With the right device, network equipment, software and card processor, reliability shouldn’t be an issue.
Posted in Best Practices for Merchants, Mobile Payments, Mobile Point of Sale, Smartphone Tagged with: (POS) systems, aggregators rates, apps, BLE technology, bluetooth, card, card processor, card reader, cash, cash register, chargebacks, consumer data, credit, credit card payments, credit card processing, credit card processors, credit card reader, credit-card, customer support, data, data loss, debit card, debit rate, device, fraud, fraud risk, hardware, industry experts, merchant account, Merchant's, mobile, mobile app, mobile credit card processing, Mobile Devices, Mobile Payments, mobile point of sale, Mobile processing apps, mobile processing transactions, mobile technology, mobile wallets, network, network equipment, nfc, nfc technology, payment solutions, payment technology, PayPal, phones, point of sale, qr codes, retailers, rewards cards, Security, Smartphones, software, Square, tablet, tablets, vendor's app, wallet providers, Wi-Fi network, wireless mobile, wireless mobile devices
May 15th, 2014 by Elma Jane
Looking to buy a new business phone? Wait!!! A slew of hot new smartphones are set to launch in the coming months, 2014 has already seen its share of major releases. This spring, HTC unveiled the new HTC One M8, which packs a slick all-metal body and Samsung debuted the featured-packed Galaxy S5. Nokia also released the Lumia Icon, its new flagship Windows Phone. But some of the year’s biggest releases are still to come, including a new version of Apple’s iPhone and a follow-up to Samsung’s stylus-equipped Galaxy Note 3. Meanwhile, a new Android phone from startup OnePlus could make a splash.
Galaxy Note 4
Samsung is expected to launch a follow-up to the Galaxy Note 3 this fall, one of the best business phones ever made, thanks in part to the included S Pen stylus, which slides out from a slot on the phone’s chassis and turns the device into a note-taking machine. The phablet also boasts a stunning 5.7-inch display that’s big enough for real productivity tasks. Samsung hasn’t officially confirmed any details about the Note 3’s successor, but there are a few safe bets. For starters, fans can expect the line’s trademark stylus to return for the Galaxy Note 4. Its display meanwhile, should rival the Samsung’s newer Galaxy S5 in terms of brightness and picture quality. Finally, considering Samsung packed a fingerprint reader into the S5’s home button, it’s likely the company will do the same for the Note 4. A fingerprint reader can make your business phone more secure, since only you can unlock the device with a quick swipe of your finger.
iPhone 6
Apple’s iPhone 5s is a great phone, but its compact 4-inch display could be too small for some people. Reports indicate that Apple might deliver a much bigger device in the iPhone 6, which is expected to debut this fall in 4.7-inch and 5.5-inch variants. That’s a big deal for business users who depend on their smartphone to stay productive but prefer a larger display. Both models are also rumored to include a blazing-fast A8 processor, an upgrade over the speedy 64-bit A7 chip found in the iPhone 5s. The iPhone 6 is also expected to include the same fingerprint reader that debuted with the iPhone 5s. The reader is embedded in the phone’s home button, and lets you unlock the device simply by placing your finger on the button. And of course, the iPhone is the only smartphone that gives you access to Apple’s App Store, which features the biggest and arguably the best, library of business and productivity apps on any platform.
LG G3
LG is preparing to unveil a successor to its flagship phone, the LG G2 this spring. The so-called LG G3 could be one of the year’s most noteworthy business phones if it retains the G2’s superlong battery life. The phone ran for up to 11 hours in tests that involved continuous Web browsing, making it one of the longest-lasting smartphones ever made. In addition to longevity, the G2 boasts a snappy quad-core processor, a roomy 5.2-inch display and a handy multitasking feature called QSlide, which lets you run a second app in a floating window over your main app. That’s a plus for business users who need to juggle tasks such as responding to email while conducting research in a Web browser. LG hasn’t yet announced which features will get an upgrade for the LG G3, but fans won’t have to wait long to find out. The company is expected to show the device off at a special press event on May 27, though it’s not yet known when the phone will hit store shelves.
Lumia 635
Windows Phone fans saw the release of a new flagship device in the Nokia Lumia Icon this spring. Now, Nokia is following that up with the Lumia 635. A new midrange Windows Phone with a lower price point, that could make it worth a look for budget-minded business users, especially since the device runs on Windows Phone 8.1, a new version of Microsoft’s mobile operating system. One of the phone’s standout features is Cortana, a voice-activated personal digital assistant that can notify you of upcoming appointments, flight information, weather alerts and more. Also, new in Windows Phone 8.1 is the Action Center, which is similar to the notification hub found on both the Android and iOS operating systems. Just swipe down from the top of your phone’s display to view all of your alerts at a glance, and like every Windows Phone device. The Lumia 635 is fully integrated with the desktop version of Microsoft Office.
OnePlus One
The OnePlusOne set to launch this June, is a powerful new business phone with a unique set of features. The 5.5-inch Android device packs a huge display, a top-tier processor and a high-capacity battery. The phone also adds features you won’t find in many flagship phones, such as always-on voice commands. So instead of fiddling with menus and touch-screen controls, you can set an alarm, place an appointment in your calendar or access turn-by-turn directions by uttering a few words – even when the display is off. The OnePlus One also offers a few notable security features you won’t find in most other smartphones. For instance, the phone’s Privacy Guard setting lets you block individual apps from accessing personal information stored on your device. The OnePlus One also ships with built-in encryption for SMS text messages to ensure your private business communications remain private.
Posted in Smartphone Tagged with: Android, Android and iOS operating systems, Android device, Android phone, App Store, Apple's iPhone, Apple's iPhone 5s, chip, Cortana, desktop, device, digital, email, encryption, fingerprint reader, flagship phones, Galaxy Note 3, Galaxy Note 4, Galaxy S5, high-capacity, HTC, HTC One M8, hub, integrated, iOS, iPhone 6, LG G2, LG G3, Lumia 635, Microsoft, Microsoft Office, Microsoft's mobile operating system, mobile, Nokia, Nokia Lumia Icon, OnePlusOne, operating systems, phablet, phones, platform, Privacy Guard, processor, QSlide, S Pen stylus, Samsung, Security, slot, Smartphones, sms, stylus, swipe, top-tier processor, touch-screen controls, voice commands, web, Web browsing, windows, windows phone, Windows Phone 8.1
May 9th, 2014 by Elma Jane
Facebook is apparently ready to become a person-to-person (P2P) money transfer network. The clear decision to launch a money transfer service in the region can be seen as a test bed for Facebook’s larger ambitions of becoming a payments hub for its 1 billion user base. Facebook was only weeks away from gaining regulatory approval in Ireland for its remittance platform FT quoted unnamed sources. Facebook’s P2P platform will be geared to facilitating migrant remittances, with the goal of expanding its payment presence in emerging markets such as India. Facebook makes the bulk of its revenue from advertising, but 10 percent of its profits reportedly come from in-game payments for online and mobile games, such as Zynga’s popular FarmVille.
From WhatsApp to what’s next
Facebook’s February 2014 acquisition of mobile messaging service WhatsApp for $19 billion clarified the social network’s strategy. The WhatsApp acquisition and the expected P2P network launch as part of the first phase of Facebook’s deeper immersion into payments.
Tech giants face up to payments
When comparing the payment strategies of tech giants Google Inc., Apple Inc. and Facebook, the latter two competitors as having bigger potential upsides than Google. Facebook and Apple (via iTunes) already have established financial relationships with millions of users who have attached funding mechanisms – debit and credit cards – to their social media accounts. As primarily a search engine, Google is playing catch up to persuade its users to set up Google Wallet accounts.
In May 2013, Google launched its own P2P network by integrating Google Wallet with Gmail accounts, so that wallet users can facilitate money transfers via email. More recently, reports have surfaced indicating Google plans to extend Google Wallet to its wearable technology solution Google Glass. But the success of such ventures rests on users’ confidence with Google as a financial service provider.
Facebook as having a brighter financial services future than Apple. Apple’s reach is limited to consumers who have iPhones and iPads, whereas Facebook is not tied to any branded mobile devices, it is a very ubiquitous offering. It could apply to anybody with any type of phone or tablet.
Eventually, tech companies like Facebook will need to partner with payment businesses in order to expand into the merchant-centric brick-and-mortar world. The mobile POS solution provider, a business unit of global POS terminal manufacturer Ingenico SA, would be an ideal partner for Facebook. If they extend what they do from P2P payments to more of a wallet purchasing capability for their users, then the next step could very easily be an extension of that into servicing the merchant side.
Posted in Financial Services, Mobile Payments, Smartphone Tagged with: Apple Inc.Facebook, consumers, credit cards, debit, device, financial service, financial service provider, Gmail accounts, Google Glass, Google Inc., Google Wallet accounts, ingenico, iPads, iPhones, iTunes, merchant-centric brick-and-mortar, migrant remittances, mobile, Mobile Devices, mobile games, mobile messaging service, mobile pos, mobile POS solution, mobile POS solution provider, money transfer, money transfer network, money transfer service, network, online, p2p, P2P network, P2P payments, P2P platform, payment businesses, payments, payments hub, phone, POS terminal, remittance, remittance platform, search engine, service provider, social media, social media accounts, social networks, tablet, wearable technology
April 22nd, 2014 by Elma Jane
Mobile Business App.
Customers should be able to easily find you wherever they are, from any device. Mobile presence is more or less essential for business success in today’s world, whether you just have a mobile-optimized website, or a full-scale dedicated mobile application for your business.
With smartphones and tablets, people have a computer in their pockets when they’re out and about are where people are engaging with content, so business want a mobile strategy.
The problem many businesses have with mobile strategy development is determining what is most effective, both in terms of reach and cost. Creating a mobile app isn’t the right path for every company, but if it’s something you’re considering, check the following questions before you invest.
Android, HTML5 or iOS?
No matter what platform you choose, it’s important not to take on too much too soon, regardless of your technical skill level. There are a lot of different solutions for app development. Keep it simple and work on it. Once you’ve made the decision to develop an app and figured out your end-goal for it, determine what platform you want to use. When businesses choose to create an app for only Android or iOS, they end up missing half the market, but building an app on both major platforms requires two different sets of technical skills. While an app creator can make it much easier to develop an app on multiple platforms, including Windows Phone and Blackberry, maintaining a multiplatform presence will end up costing you more. HTML5 Web-based apps may not be as visible as those in major platform app stores, but they are compatible on mobile browsers of any operating system, as well as desktop browsers.
Make an own app, or become part of an existing?
If you want to create your own native app, make sure you have a plan to continually update and work on it. Don’t underestimate the ongoing maintenance. Constantly engage with the app, and as you’re planning it in the first place, think about what you want to add over time.
Many businesses begin the app development process without considering the amount of time and money they will need to invest in the process. Becoming part of an existing app for example, a directory-type app that lists businesses in your industry can be an easier, less expensive way to claim your segment of the mobile market. The app creator can do the heavy technical work while also providing you with the opportunity to connect with its larger network of users.
What do you want to gain from your business app?
Is it to bring people into your store or to get them to visit your website? Many businesses waste a lot of resources because they think people will just come to their app. It’s trendy to say that you have a mobile app, but if your goal is just to have that mobile presence, you’ll create something that no one will ever see. Small businesses should set a clear goal to focus on before beginning app development. Having a mobile presence is more or less essential for business success in today’s world. Whether you just have a mobile-optimized website, or a full-scale dedicated mobile application for your business, your customers should be able to easily find you wherever they are, from any device.
Posted in Best Practices for Merchants, e-commerce & m-commerce, Financial Services, Mobile Payments, Mobile Point of Sale, Smartphone Tagged with: Android, android or ios, app, app development, blackberry, business, device, html5, iOS, mobile, mobile application, mobile browsers, mobile presence, mobile strategy, mobile-optimized website, multiplatform, pockets, Smartphones, tablets, web-based apps, windows phone
February 18th, 2014 by Elma Jane
Payment Tokenization Standards
Tokenization is the process of replacing a traditional card account number with a unique payment token that is restricted in how it can be used with a specific device, merchant, transaction type or channel. When using tokenization, merchants and digital wallet operators do not need to store card account numbers; instead they are able to store payment tokens that can only be used for their designated purpose. The tokenization process happens in the background in a manner that is expected to be invisible to the consumer.
EMVCo – which is collectively owned by American Express, Discover, JCB, MasterCard, UnionPay and Visa – has announced that it is expanding its scope to lead the payments industry’s work to standardize payment tokenization. EMVCo says that the new specification will help provide the payments community with a consistent, secure and interoperable environment to make digital payments when using a mobile handset, tablet, personal computer or other smart device.
Key elements of EMVCo’s work include adding new data fields to provide richer industry information about the transaction, which will improve transaction efficiency and enhance the consumer and merchant payment experience by helping to prevent fraudulent card account use. EMVCo will also create a consistent approach to identify and verify the valid use of a token during payment processing including authorization, capture, clearing and settlement.
EMVCo’s announcement follows an earlier joint announcement from MasterCard, Visa and American Express that proposed an initial framework for industry collaboration to standardize payment tokenization. EMVCo says it will now build on this framework with collective input from all of its members and the industry as a whole.
Posted in Credit card Processing, Credit Card Reader Terminal, Credit Card Security, Digital Wallet Privacy, Electronic Payments, Financial Services, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: American Express, authorization, capture, card account numbers, clearing, data fields, device, digital payments, Digital Wallet, Discover, EMV, emvco, fraudulent card account, interoperable, jcb, MasterCard, merchant, mobile handset, payment, payment processing, payment token, secure, security standards, settlement, smart device, specification, standardize, tablet, token, tokenization, transaction, visa
October 31st, 2013 by Elma Jane

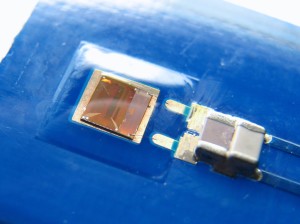
Ingenico Biometric Credit Card Terminal with EMV Chip and PIN Processing NFC.
Ingenico’s new biometric payment device (the iWB 220) is to be used in a pioneering project, to bring financial support to low-income families.
Payment solutions provider, Ingenico are to deploy Ingenico´s biometric solution in Colombia and the Dominican Republic, together with Carvajal Tecnología y Servicios, a player in the electronic payment industry in Latin America,
This biometric point of sale solution complies with the Image Quality Specifications for single finger capture device defined by the FBI, the United States Federal Bureau of Investigation.
In addition to high security standards, the solution is a mobile device with an embedded Magstripe, as well as Chip & PIN readers.
Upon government approval for each of the applications, funds will be sent to the banks and through the use of these unique devices, beneficiaries can withdraw their funds, with the use of a fingertip. Approved family members are the only ones able to withdraw the funds, and the government is assured that the benefit is being paid to the right person.
Posted in Credit Card Reader Terminal, Credit Card Security, Electronic Payments, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security Tagged with: banks, biometric, capture, Chip & PIN, deploys, device, electronic, finger, fingertip, funds, ingenico, iwb220, magstripe, mobile, paid, payments, readers, solution, withdraw