September 16th, 2016 by Elma Jane
National Transaction offer valuable features and benefits, if you want to improve your business’s productivity, you should look for the following features below, that you need from your Electronic Payments provider.
Advanced Security Options – 6 out of 10 small businesses close within six months of a card data breach, it is important that Point-of-Sale devices should have appropriate security measures, particularly EMV, encryption and tokenization. NTC offer Safe-T for Small and Medium Businesses and Safe-T for Large Businesses. The Top-tier security is important on your business’s data especially customer information, consider adding additional authentication procedures.
Fast Payment Processing – first step is having up-to-date technology, because some customers might leave, the sooner you have the money processed by your provider, the bigger and stronger your business can become. NTC is adept at administering payments quickly and efficiently. We can provide regular funding or next day funding.
Feature Flexibility – obtaining the features you need from your payment services provider is very important. Look for a provider that appropriately addresses your payment concerns.
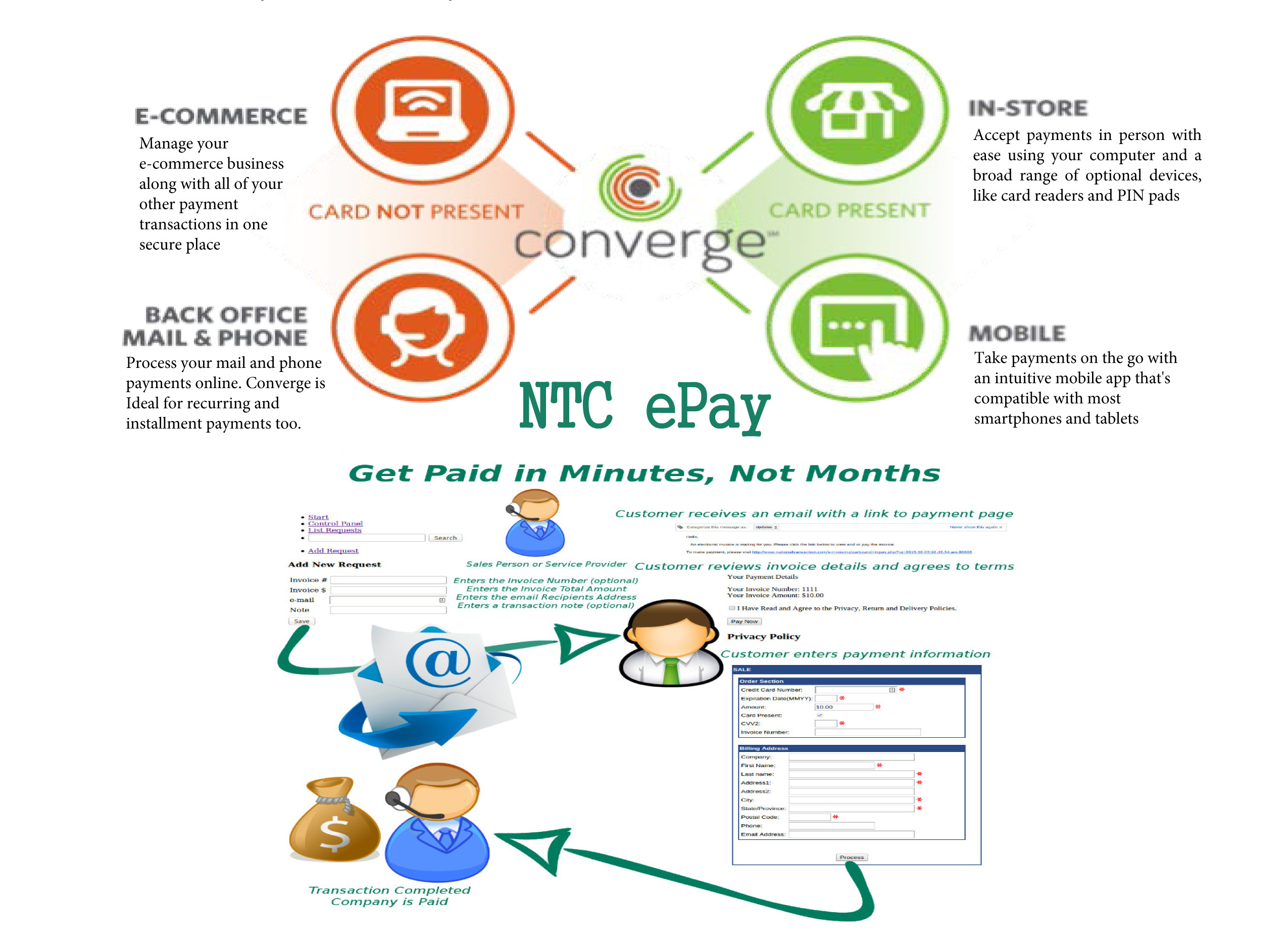
Mobile Payment Processing – NTC offer Virtual Merchant/Converge Mobile that gives you the ability to accept payments using your smartphone or tablet anywhere you go. Furthermore, the app works with most Apple and Android mobile devices. Accept a key-entered transactions or swipe cards using an encryption reader. You can now take chip card payments using Ingenico iCMP PIN Pad or the new RP457c card reader.
Reliable Customer Support – NTC is available 24/7, the phones are answered by humans and not automated systems. You got support with your hardware, answer questions and guide you to better understand the process. Customer support is the most important feature of any business partnership you make. At NTC we are very passionate about that.
Up-to-Date Tech – futuristic features, like mobile payment abilities, EMV/NFC, contactless payments are worth investing. Modern consumers are generally more familiar with up-to-date payment systems. Seeing a payment service provider offer a swipe-only terminal should be a red flag, because the recent regulations require merchants to have EMV to provide better data security.
Posted in Best Practices for Merchants, Credit Card Security, Electronic Payments, EMV EuroPay MasterCard Visa, Mobile Payments, Mobile Point of Sale, Near Field Communication, Point of Sale, Smartphone Tagged with: Breach, card data, card reader, chip card, contactless payments, data, EMV, encryption, merchants, mobile, mobile payment, nfc, payments, Payments provider, point of sale, provider, Security, service provider, smartphone, swipe, tablet, terminal, tokenization, transactions

August 3rd, 2016 by Elma Jane
National Transaction offer valuable features and benefits. If you want to improve your business’s productivity, you should look for this features that you need from your merchant account provider.
Advanced Security Options – did you know that 6 out of 10 small businesses close within six months of a card data breach? Point-of-Sale devices should have appropriate security measures, particularly EMV, encryption and tokenization. With National Transaction we have Safe-T for Small and Medium Businesses and Safe-T for Large Businesses. Top-tier security is important on all your business’s data especially customer information, consider adding additional authentication procedures. Merchant account providers bundle various security features to make the process of becoming secure.
Fast Payment Processing – having up-to-date technology is the first step because some customers might become annoyed by slow service and leave. The sooner you have the money processed by your merchant account provider, the bigger and stronger your business can become. NTC is adept at administering payments quickly and efficiently. We can provide regular funding or next day funding.
Feature Flexibility – Look for a merchant provider that appropriately addresses your payment concerns. Obtaining the features you need from your merchant services provider is very important.
Mobile Payment Processing – NTC offer Virtual Merchant/Converge Mobile that gives you the ability to accept payments using your smartphone or tablet anywhere you go. The app works with most Apple and Android mobile devices. You can accept key-entered transactions or swipe cards using an encryption reader. You can now take chip card payments using Ingenico iCMP PIN Pad. Merchants who aren’t mobile payment capable do demonstrate unwillingness to progress with payment technology and might lose customers eventually.
Reliable Customer Support – NTC is available 24/7 answering the phone by humans and not automated systems. You got support with your hardware, answer questions and guide you to better understand the process. Customer support is perhaps the most important feature of any business partnership you make. You don’t want to choose the wrong provider.
Up-to-Date Tech – futuristic features, like mobile payment abilities, EMV/NFC, contactless payments are worth investing. Modern consumers are generally more familiar with up-to-date payment systems. Seeing a merchant service provider offer a swipe-only terminal should be a red flag, because the recent regulations require merchants to have EMV to provide better data security.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Financial Services, Merchant Account Services News Articles, Merchant Services Account, Mobile Payments, Mobile Point of Sale, Small Business Improvement, Travel Agency Agents Tagged with: account, Breach, card data, chip card, customer, EMV, encryption, merchant, mobile, payment, point of sale, provider, Security, tokenization, transactions

December 14th, 2015 by Elma Jane
Reality of data theft means that a breach can sometimes have two or three aftershock effects years down the line.
Eighty five percent of American consumers admitted that if significant personal consequences present themselves after their information is compromised as part of a breach, they would have no problem seeking a new place to spend their money.
In particular, 67 percent said that they would cut ties with the victimized brand if money was actually removed from their checking accounts, 62 percent said so if their credit cards were charged for fraudulent purchases, 57 percent said the same if their personal information was released and 54 percent would look elsewhere if their credit scores were affected.
It’s been two years since major retail attacks made data breach a household word, vice president of enterprise data security firm said.
As it becomes easier for customers to switch their preferred brands, data breaches events can be too devastating for some merchants.
http://www.pymnts.com/news/2015/been-breached-say-bye-bye-to-customer-loyalty/
Posted in Best Practices for Merchants Tagged with: Breach, credit, data breach, data security, merchants
September 23rd, 2014 by Elma Jane
Home Depot, US retail chain says that 56 million payment cards are at risk following a malware-laden cyber-attack on eftpos tills across its stores in the US and Canada.
The investigation into a possible breach began on September 2nd,Tuesday morning, immediately after Home Depot received reports from its banking partners and law enforcement that criminals may have breached its systems.
According to Home Depot’s security partners, the malware had not been seen previously in other attacks.
Criminals used unique, custom-built malware to evade detection. The cyber-attack is estimated to have put payment card information at risk for approximately 56 million unique payment cards, after lurking in the company’s eftpos tills for four months between April and September.
While the breach has been seen as a further proof-point in the US push to adopt Chip and PIN at the point-of-sale, the fact that the outbreak also hit the home improvement chain’s Canadian stores, where the EMV standard has been implemented, leaves pause for thought. Nonetheless, the retailer has committed to installing 85,000 PIN pads at its US outlets, well ahead of the national 2015 deadline.
Home Depot has set aside $65 million to cover the cost to investigate the data breach, provide credit monitoring services to its customers, increase call center staffing, and pay legal and professional services. Approximately $27 million of the projected outlay will be covered by the company’s insurance.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Point of Sale Tagged with: banking partners, Breach, call center, card information, cards, Chip and PIN, credit monitoring, credit monitoring services, customers, cyber-attack, data breach, EMV, EMV standard, Malware, payment, payment card information, payment cards, PIN pads, point of sale, risk
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services
May 5th, 2014 by Elma Jane
The Payment Card Industry (PCI) Data Security Standard (DSS) has come under criticism as high profile data breaches continue to expose flaws in retailers’ data security systems. But telecommunications firm Verizon Wireless concluded that the PCI DSS is working.
Some Responses to Criticisms
Nilson Report research from August 2013 that said card fraud cost the global payments market over $11 billion in 2012. Verizon added that the frequency of fraud schemes that the PCI DSS was designed to avoid is in fact growing. And yet most businesses are not fully compliant at the time of assessment. Only 51.1 percent of the companies it had audited had passed seven of the 12 requirements of the PCI DSS and only 11.1 percent of said companies had passed all 12.
Verizon addressed some of the criticisms leveled at the PCI DSS. One concern is that the standard promotes compliance as a test to be passed and forgotten, which distracts companies from focusing on improving security. Verizon responded by stating that breached businesses were less likely to be PCI DSS compliant than unaffected companies. It also said businesses improve their chances of not being breached by having the standard in place, and of minimizing the damage of a breach should one occur.
Another common complaint leveled at the standard is that it is too cumbersome and slow moving in relation to the quickly evolving threat landscape and nimble fraudsters ready to try new tactics. Verizon countered that the PCI DSS is meant to be a set of baseline security protocols. Achieving compliance with any standard is simply not enough, organizations must take responsibility for protecting both their reputation and their customers. Most attacks on networks are of the simple variety, with 78 percent of hacking techniques considered low or very low in sophistication. Data Breach Investigations Report (DBIR) research shows that while perpetrators are upping the ante, trying new techniques and leveraging far greater resources, less than 1 percent of the breaches use tactics rated as high on the VERIS (Verizon’s Data breach Analysis Database) difficulty scale for initial compromise.
Recommendations
There’s an initial dip in compliance whenever a major update to the standard is released, so organizations will have to put in additional effort to prepare for achieving compliance with DSS 3.0.
The newest version of the standard, PCI DSS 3.0, went into effect Jan. 1, 2014. Businesses have until Jan. 1, 2015, to implement it. The updated standard has new requirements and clarifications to version 2.0 that will take time for businesses to understand and implement, and this will result in more organizations being out of compliance.
To help businesses deal with their PCI DSS compliance obligations the firm offered five approaches:
Don’t leave compliance to information technology security teams, but enlist application developers, system administrators, executives and other staff in helping further along the process.
Embed compliance in everyday business practices so that it is sustainable.
Integrate compliance programs into enterprise-wide governance, risk and compliance strategies.
Learn how to reduce the scope of organizations’ compliance responsibilities, chiefly by figuring out how to store less data on fewer systems.
Think of compliance as an opportunity to improve overall business processes, rather than as a burden.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Electronic Payments, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: attacks on networks, Breach, breached, business processes, compliance, compliant, data breach investigators, data breaches, data security systems, database, DSS, fraud schemes, global payments, hacking, information technology, Payment Card Industry, PCI, retailers, Security, security protocols, standard, system administrators, wireless
March 14th, 2014 by Elma Jane
Merchant and Consumer Groups Seek Senate Support To Forego EMV Chip and Signature As Breach Concerns Rise
There’s no shortage of answers in trying to put a stop to hackers set on throwing chaos into the way consumers transact at the point of sale, or online for that matter. Yesterday, the Banking, Housing and Urban Affairs subcommittee on national security and international trade and finance got its chance to hear some of them.
During the hearing, William Noonan, deputy special agent in charge, U.S. Secret Service, noted the advances in computer technology and greater access to personally identifiable information online, which have created a virtual marketplace for transnational cyber criminals to share stolen information and criminal methodologies. As a result, the Secret Service has observed a marked increase in the quality, quantity, and complexity of cyber crimes targeting private industry and critical infrastructure. These crimes include network intrusions, hacking attacks, malicious software, and account takeovers leading to significant data breaches affecting every sector of the world economy.
The recently reported data breaches of Target and Neiman Marcus represent only the most recent, well-publicized examples of this decade-long trend of major data breaches perpetrated by cyber criminals intent on targeting the nation’s retailers and financial payment systems. The increasing level of collaboration among cyber-criminals allows them to compartmentalize their operations, greatly increasing the sophistication of their criminal endeavors and allowing for development of expert specialization. These specialties raise both the complexity of investigating these cases, as well as the level of potential harm to companies and individuals.
So how should the industry react to prevent further breaches? Those opinions provided during testimony at the hearing varied widely, though both consumer and merchant groups would like the card networks to give up requiring only signatures for smart card purchases at the point of sale.
Consumer program director at the U.S. Public Interest Research Group, called for myriad of changes, citing that the greater risk from the recent breaches is less related to identity theft than it is to fraud on existing accounts, and he said it’s time for players on both sides of the transaction to focus more on protecting consumers than on managing their own risk.
Until now, both banks and merchants have looked at fraud and identity theft as a modest cost of doing business and have not protected the payment system well enough. They have failed to look seriously at harms to their customers from fraud and identity theft -including not just monetary losses and the hassles of restoring their good names, but also the emotional harm that they must face as they wonder whether future credit applications will be rejected due to the fraudulent accounts.
As a first step, Congress should institute the same fraud cap, $50, on debit/ATM cards that exists on credit cards, or eliminate the $50 cap entirely, since it is never imposed because of the zero-liability policies issuers have voluntarily have imposed. Congress also should provide debit and prepaid card customers with the stronger billing-dispute rights and rights to dispute payment for products that do not arrive or do not work as promised, just as many credit card users enjoy.
Congress should endorse a specific technology, such as EMV smart cards and if it does, require the use of PINs when initiating smart card transactions. The current pending U.S. rollout of chip cards will allow use of the less-secure chip-and-signature cards rather than the more-secure chip-and-PIN cards. Why not go to the higher-and-PIN authentication standard immediately and skip past chip and signature? There is still time to make this improvement.”
Retailers have spent billions of dollars on card-security measures and upgrades to comply with PCI card security requirements, but it hasn’t made them immune to data breaches and fraud. The card networks have made those decisions for merchants, and the increases in fraud demonstrate that their decisions have not been as effective as they should have been.
The card networks should forego chip and signature and go straight to chip and PIN. To do otherwise would mean that merchants would spend billions to install new card readers without they or their customers obtaining PINs’ fraud-reducing benefits. We would essentially be spending billions to combine a 1990’s technology chips with a 1960’s relic signature in the face of 21st century threats.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Reader Terminal, Credit Card Security, Digital Wallet Privacy, Electronic Payments, EMV EuroPay MasterCard Visa, Financial Services, Merchant Services Account, Payment Card Industry PCI Security, Point of Sale, Small Business Improvement, Visa MasterCard American Express Tagged with: banking, Breach, card networks, card-security, chip and signature, chip cards, chip-and-PIN cards, computer technology, credit applications, credit cards, critical infrastructure, cyber crimes, cyber-criminals, data breaches, debit atm cards, EMV, hackers, hacking attacks, international trade and finance, malicious software, managing risk, merchant, national security, netwrok intrusions, new card readers, online, payment system, pci card security requirements, PIN, point of sale, prepaid card customers, smart card transactions, technology chips, the secret service, transnational cyber criminals, virtual marketplace, world economy
September 10th, 2013 by Admin
Verizon annually releases it’s Data Breach Investigation Reports which probes data breaches in various industries and studies the nature of fraud reported by merchants and other agencies. In the past Verizon has worked with the U.S. Secret Service, now the information gathered on the electronic payment breaches have expanded to Police Central e-Crime Unit, Australian Federal Police, the Dutch National High Tech Crime Unit, and the Irish Reporting & Information Security Service in addition to the United States Secret Service.
One area that Verizon broke out and performed independent studies on was the healthcare industry. In 2010 the Health Information Technology for Economic and Clinical Health (HI TECH) Act included a provision to report healthcare and medical data breaches to a variety of outlets including the Secretary of Health and Human Services. Medical record protections keep the casual cyber criminal at bay but the majority of security data breaches are in large part targeted at information attackers can profit from. The data cybercriminals target most often includes health insurance data, personal and electronic payment transaction data. Hardware is another assett that is targeted both because of the data on the hardware and the cost of the hardware itself.
Remote data breaches on health care providers were typically carried out through some form of hacking or malware. That is consistent with other industries in the report and is considered the favorites among cybercriminal organizations. Exploiting of default or guessable credentials rang in at the top of the chart. Of those, point of sale payment systems and desktop computers were the highest targeted areas of the health care industry. Although electronic medical records and transcriptions stored on file and database servers were a target, those criminals were more likely interested in indentity theft and fraudulent loans than what was actually in any individuals medical records.
Point of sale payment terminals are the most targeted assett with POS servers and gateways as the second most targeted. Like all other sectors, professional criminals tend to follow the money trail and that ends up being at POS payment systems. So much so that even desktop computers and emails try to get malware onto medical systems to render security policies inneffective. To find out how to better protect medical and healthcare records from cybercriminals and data breaches read the reports here and here.
Posted in Best Practices for Merchants, Credit Card Security, Point of Sale Tagged with: Breach, breaches, electronic payment, gateways, healthcare, medical, point of sale, POS, Security, transactions, transcription
Data Breaches Cost Consumers Billions
Exposure of personal information is a new challenge in todays environment, the initial exposure being a nightmare to unravel. A Javelin Strategy and Research study shows that a single data security breach can cost Billions of dollars in consumer fraud losses. Data security breaches rose 48% from 2011 in 2012 to 1,611 data breaches. Identity theft is on the rise too.
Walmart CEO Mike Duke Expecting $10 Billion in e-commerce payments 2013.
Commenting at a shareholder meeting WalMart CEO Mike Duke expected WalMarts online e-commerce site to bring in $10 Billion in transactions this year.
India Sees Spike in e-commerce and Mobile Payment Investments.
India is seeing deeper saturation of broadband rollouts connecting personal computers and laptops online at a faster pace. Big names such as Intel are keen on India’s development for market opportunities. Amazon and ebay just staked claims to India’s e-commerce playing field with deals to deliver their e-commerce services. Read more of this article »
Posted in Electronic Payments Tagged with: Breach, Digital Wallet, e-commerce, electronic payments, Mobile Payments, nfc, tablet, Virtual Currency







