Category: Payment Card Industry PCI Security

February 29th, 2016 by Elma Jane
True Stories of our Customers in Action
Travel Agency ~ An Independent Travel Firm had been using their bank as credit card processor. When they learned that Virtuoso and NTC were going to team up they jumped on the opportunity. Not only NTC has lowered their fees but NTC has streamlined their credit card processing. The manual type-in process before has been all automated batch process now which saves time. This is a great new partnership for Virtuoso and its members.
Wholesale Hardware Industry ~ Have been turned down his business loan by a traditional bank last year due to his bankruptcy few years ago. He has no option but to borrow using a Cash Advance, making daily payment with a very high-interest rate. NTC was able to get an approval for a Real Business Loan, with monthly payment with an annual rate.
Term loan amount: $85K – Line of credit: $75K
Another Travel Agency ~ NTC has great customer service, the support team will patiently guide you through the PCI compliance. The payments specialist will check whether they could reduce your rates (which they did successfully!). They will even follow up regularly with status updates. NTC is exemplary!
NTC has a lot to offer, from our e-Pay Service and other New Programs for ISO’s, and Options for your merchants. NTC, The Payments and Technology Expert! Visit us at www.nationaltransaction.com or call us at 888-996-2273.
Posted in Best Practices for Merchants, Credit card Processing, Payment Card Industry PCI Security, Travel Agency Agents Tagged with: bank, Business Loan, card, cash advance, credit card, customers, loan, merchants, payment, PCI Compliance, processor, travel, travel agency

January 12th, 2016 by Elma Jane
Can we securely store card data for recurring billing?
PCI DSS discourages businesses from storing credit card data, Merchants feel the practice is necessary in order to facilitate recurring payments.
The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, MasterCard, American Express, Discover, and JCB.
In order for the electronic storage of cardholder data to be PCI Compliant, appropriate encryption must be applied to the primary account number (PAN). In this situation, the numbers in the electronic file should be encrypted.
All PCI controls would apply to the environment in which the cardholder data is transmitted and stored. Tokenization can be implemented for recurring and/or delayed transactions. Travel Merchants and or Storage Facility could use this feature to help reduce the need for electronically stored cardholder data while still maintaining current business processes.
The best thing you can do for your business is to not store any cardholder data or personally identifiable information.
Tomorrow let’s tackle Encryption and Tokenization a strong combination to protect card data while reducing the cost of compliance!
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Payment Card Industry PCI Security, Travel Agency Agents, Visa MasterCard American Express Tagged with: cardholder data, credit card, data, merchants, payments, Security, tokenization, transactions, travel
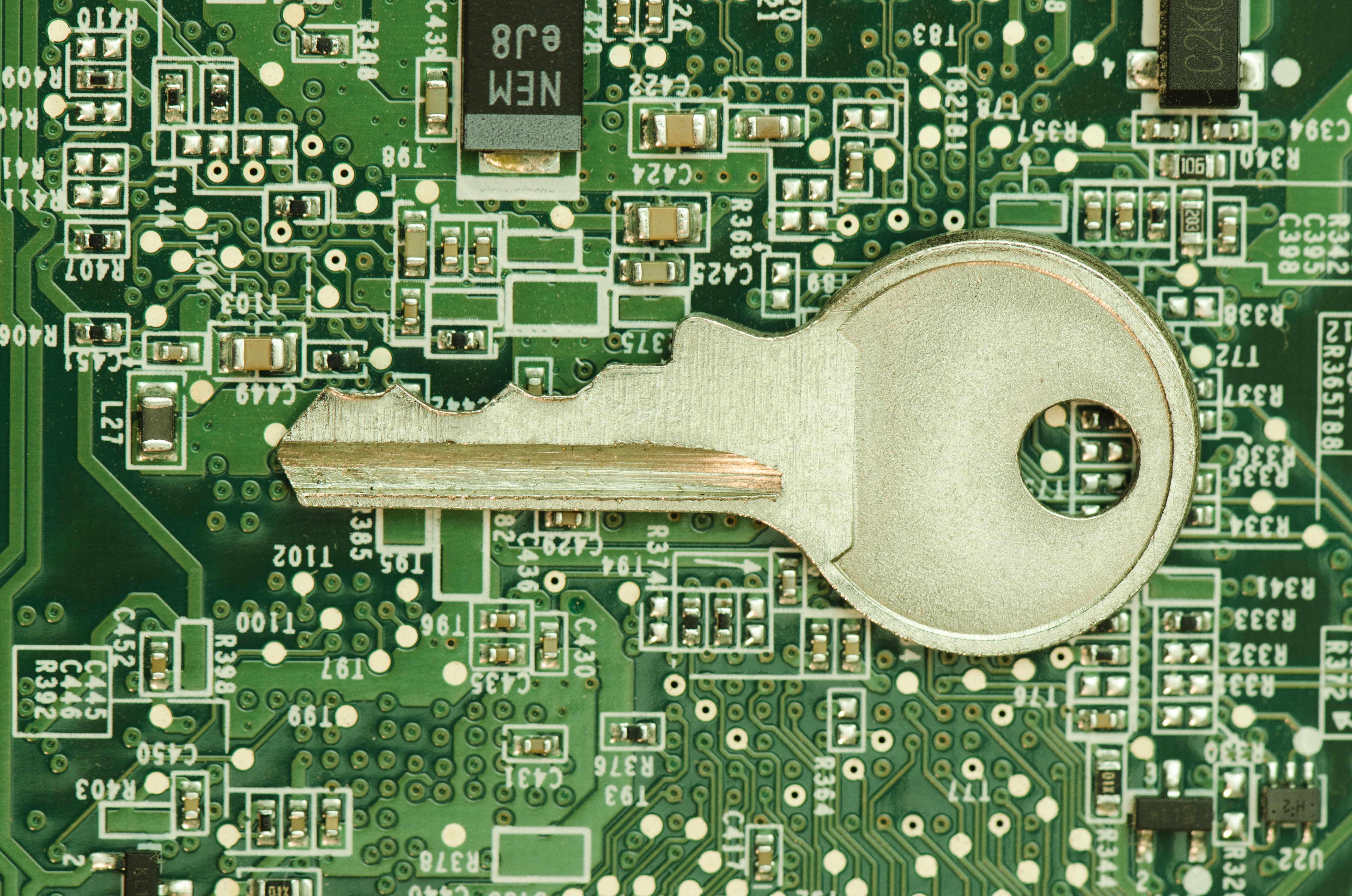
November 16th, 2015 by Elma Jane
Combat Fraud With Layered Approach!
Encryption and Tokenization a strong combination to protect cardholder data at all points in the transaction cycle.
Encryption – the strongest protection for card data when it’s in transit. From the moment a payment card is swiped or dipped at a terminal featuring a hardware-based, tamper resistant security module. Encryption protects the card data from fraudsters as it travels across various systems and networks until it is decrypted at secure data center. Encryption is ideally suited for any businesses that processes card transactions in a face to face or card present environment.
Tokenization – protects card data when it’s in use and at rest. It converts or replaces cardholder data with a unique token ID to be used for subsequent transactions. This eliminates the possibility of having card data stolen because it no longer exists within your environment. Tokens can be used in card not present environments such as e-commerce or mail order/telephone order (MOTO), or in conjunction with encryption in card present environments. Tokens can reside on your POS/PMS or within your e-commerce infrastructure at rest and can be used to make adjustments, add new charges, make reservations, perform recurring transactions, or perform other transactions in use.
A layered approach can be the most effective way to combat fraud. Security solutions that provide layers of protection, when used in combination with EMV and PCI-DSS compliance; to ensure you’re doing all you can to protect cardholder data from increasingly complex and evolving security threats.
Posted in Best Practices for Merchants, Credit Card Security, e-commerce & m-commerce, EMV EuroPay MasterCard Visa, Mail Order Telephone Order, Mobile Point of Sale, Payment Card Industry PCI Security, Point of Sale Tagged with: card data, card present, card transactions, card-not-present, cardholder, e-commerce, EMV, encryption, mail order, moto, payment card, PCI-DSS, PMS, POS, telephone order, terminal, tokenization, tokens

November 3rd, 2015 by Elma Jane
While EMV represents a significant improvement in the way credit/debit card fraud is detected and prevented, some have confused EMV’s capabilities with the concepts of data security and PCI compliance.
Does EMV override PCI?
The answer is NO, EMV technology does not satisfy any PCI requirements, nor does it reduce PCI scope.
- EMV is counterfeit card fraud protection – it makes it more difficult to make use of stolen card data.
- EMV is not encryption – EMV does not encrypt the Primary Account Number (PAN) and therefore the card data must still be protected according to PCI guidelines.
- EMV only works for card present transactions.
If your business accepts credit or debit cards in a physical store or other face-to-face setting, you will need to implement the EMV technology and PCI standards. If you upgrade your terminals for EMV, consider adding point-to-point encryption (P2PE) capabilities to reduce PCI scope and protect data end to end. In addition, using tokens after authorization can prevent the card data from being used, should it be stolen.
Posted in Best Practices for Merchants, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security Tagged with: card data, card fraud, card present, counterfeit card, credit, data security, debit card, EMV, emv technology, fraud, p2pe, PAN, PCI, PCI Compliance, point-to-point encryption, Primary Account Number, terminals, tokens

October 15th, 2015 by Elma Jane
There are numbers of guidelines issued for accepting card payments, and merchants are expected to understand them all. To avoid issues down the road know a few basic rules in order to keep your business going without being penalized.
There’s a lot of ways to process a credit card: In-store, online, and by phone. There’s also different ways to pay and different brands of cards.
In-store and Card-not-present policies.
In-Store Policies:
- Always verify that the person presenting the card is the cardholder
- Ask for a 2nd ID for comparison
- Cards are non-transferable, cardholder MUST be present for purchase
- Compare the signature on the back of the card with that of the person who presents the card
- Inspect the card to confirm that it’s not visibly altered or mutilated
- Validate the card’s expiration date
Online/Phone Payment Policies: Card-not-present transactions
- Card account number
- Card billing address
- CID (3 digits on back of card OR 4 on the front)
- Card expiration date
- Card member’s home or billing telephone number
- Card member name (as it appears on the Card)
Rules for Visa, MasterCard and Amex that merchants need to know:
- Never store cardholder data on any systems to help minimize the risk of fraud and protect your business from potential chargebacks.
Complying with Federal Laws, State Laws and PCI
- A merchant should be familiar with and abide by Federal Laws regarding accepting credit cards. The Fair Credit Reporting Act is the federal law that establishes the foundation of consumer credit rights. This law regulates the collection and use of consumer credit information by merchants.
- Check state laws on the use of consumer credit information and accepting credit cards. Not all states have additional laws that regulate credit card practices, but some (such as California) prohibit merchants from requesting/requiring a customer to provide any personal information (like their address or telephone number) on any form involved with their credit card transaction. So, it is advised that merchants inquire about further information in their particular state.
- The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that all companies processing, storing, or transmitting credit card information uphold a secure environment. These rules essentially apply to any merchant that has a Merchant ID (MID). If you are a merchant that accepts credit card payments, you are required to comply with the PCI Data Security Standard, large or small businesses.
EMV Liability Shift Set By Visa and MasterCard as of October 1st
U.S. banks and credit card companies are now using the EMV (Europay, MasterCard, and Visa) technology. The EMV liability shift for fraud carried out in physical stores with counterfeit cards belongs to the merchant if it has not yet upgraded its POS system to accept EMV-enabled chip cards. While issuers absorb losses under card-network rules, that burden will shift to acquirers in cases where the fraud occurs at merchants unprepared for EMV.
It’s good to know every aspect of your business. The above guidelines are part of a business that every merchants should be familiar with. The main reason for these rules is to protect your business and keep your customer’s payment card data safe and secure.
To start accepting more credit cards give us a call now at 888-996-2273. We have the latest terminals that’s EMV/NFC capable.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security Tagged with: amex, card network, card payments, card-not-present, chargebacks, chip cards, credit card, credit card companies, Data Security Standard, EMV, EuroPay, MasterCard, merchants, MID, Payment Card Industry, PCI-DSS, POS system, U.S. banks, visa

October 9th, 2015 by Elma Jane
Credit card fraud is much more difficult to prevent in a card-not-present transaction. In a face-to-face setting the merchant can inspect the card to ensure that it is valid and can verify that the cardholder is an authorized user on the account. None of these actions can be performed when the payment is submitted online or accepted by phone. As we moved in adopting EMV Technology, majority of fraud is going to migrate away from counterfeit and stolen cards towards the card-not-present transaction as happened in other countries.
A combination of best practices and fraud prevention tools can provide card-not-present merchants with strong fraud prevention capabilities.
Steps to avoid fraud and protect your business for a card-not-present transaction:
- Email Verification: Send a message to the email address provided by the customer requesting that the customer verify the email address is correct, you can ensure that the email is associated with the other information provided.
- Maintain PCI compliance:All merchants accepting card payments are now required to be compliant with the requirements of the PCI DSS (Payment Card Industry Data Standard) which sets the rules for data security management, policies, procedures, network architecture, software design and other protective measures.
- Security Code Verification. Requesting the three digit security code on the back of a credit card. Visa (CVV2), MasterCard (CVC 2) and Discover (CID) cards, and the 4-digit numbers located on the front of American Express (CID) cards. Card Security Codes help verify that the customer is in a physical possession of a valid card during a card-not-present transaction.
- Use an Address Verification Service (AVS): Enables you to compare the billing address provided by your customer with the billing address on the card issuer’s file before processing a transaction. AVS is good protection against card information obtained through means like phishing and malware because fraudster might not know the billing address.
- Use 3D Secure Service: MasterCard and Verified by Visa enable cardholders to authenticate themselves to their card issuers through the use of personal passwords they create when they register their cards with the programs. The liability of any fraudulent charges through the 3D service is picked up by the issuer, not the merchant.
- Verify the phone number and transaction information.Prior to shipping your products, call the phone number provided by the customer and verify the transaction information. Criminals may be unable to verify such information, because in their haste to max out the credit line before the fraud is discovered, they often order at random and do not keep records.
Posted in Best Practices for Merchants, e-commerce & m-commerce, Mail Order Telephone Order, Payment Card Industry PCI Security, Travel Agency Agents Tagged with: American Express, card-not-present, card-security, cardholder, cnp, credit card, Discover, EMV, MasterCard, merchant, Payment Card Industry, payments, PCI, visa

October 9th, 2015 by Elma Jane
In order to maintain some sort of order within PCI Compliance, VISA and MasterCard have created 4 risk levels that will apply to any particular business, for determining the risk level of a merchant.
| Merchant Level |
Description |
Validation Requirements |
| Level 1 |
Merchants processing over 6 million Visa transactions annually (all channels) or Global merchants identified as Level 1 by any Visa region. |
Annual Report on Compliance (ROC) by Qualified Security Assessor (QSA) or internal auditor if signed by officer of the company.
Quarterly network scan by Approved Scan Vendor (ASV).
Attestation of Compliance Form. |
| Level 2 |
Merchants processing 1 million to 6 million Visa transactions annually (all channels). |
Annual Self-Assessment Questionnaire (SAQ).
Quarterly network scan by ASV.Attestation of Compliance Form. |
| Level 3 |
Merchants processing 20,000 to 1 million Visa e-commerce transactions annually. |
Annual Self-Assessment Questionnaire (SAQ).
Quarterly network scan by ASV.
Attestation of Compliance Form. |
| Level 4 |
Merchants processing less than 20,000 Visa e-commerce transactions annually and all other merchants processing up to 1 million Visa transactions annually. |
Annual SAQ recommended.
Quarterly network scan by ASV if applicable.
Compliance validation requirements set by acquirer. |
Posted in Best Practices for Merchants, Credit Card Security, e-commerce & m-commerce, Payment Card Industry PCI Security Tagged with: MasterCard, merchant, PCI Compliance, visa
May 19th, 2015 by Elma Jane
We’re now nearly midway through 2015, and payment security still remains a topic that stirs up great concern and confusion. While there is seemingly unanimous agreement on the need for heightened security, there’s uncertainty about those who are tasked with actually implementing it. Let’s dig deeper into EMV, P2PE and tokenization. How each will play a part in the next generation of securing payments, and how without properly working together they might just fall short.
Europay, MasterCard, and Visa (EMV) – A powerful guard against credit card skimming. EMV also uses cryptography to create dynamic data for every transaction and relies on an integrated chip embedded into the card.
Downside: For Independent Software Vendor (ISVs), the biggest downside of EMV is the complexity of creating an EMV solution. ISVs interested in certifying PINpads with a few processors face up to 22 months of costly work, and because there are a large number of pending certifications, processors will be backed up over the next few years.
It’s not impossible for an ISV to build EMV solutions in-house, but it’s difficult and unnecessary when there are plug-and-play EMV solutions available. These solutions include pre-packaged and pre-certified APIs that remove most of the need for research, the complexity and the burden of time and cost.
Point to Point Encryption (P2PE) – Secures devices, apps and processes using encrypted data with cryptographic keys only known to the payment company or gateway from the earliest point of the transaction, from tech-savvy criminals, jumping at their chance to intercept POS systems and scrape the memory from Windows machines.
How does a key get into card reader? Through an algorithm called derived unique key per transaction (DUKPT), or “duck putt.” DUKPT generates a base key that’s shared with device manufacturers securely, where output cardholder data is rendered differently each time a card is swiped, making it impossible to reverse engineer the card data. P2PE not only benefits the cardholders, but also the ISVs and merchants. PA-DSS certification was designed to address the problems created with cardholder data which is not encrypted.
Downside: P2PE isn’t cheap if an organization wants to do it in-house. The secure cryptographic device needed to manage the keys, Hardware Security Module (HSM), can cost $30-40,000 but when it’s built out, that total cost can jump to $100,000.
TOKENIZATION – The best way to protect cardholder data when it’s stored is using tokenization, a process which the PCI Security Standards Council describes as one where the primary account number is replaced with a surrogate value a token. For merchants dealing with recurring billing, future payments, loyalty programs and more, tokenization is critical.
Downside: Tokenization doesn’t prevent malware that’s remotely installed on POS devices. It’s possible, as seen with recent retail card breaches, for data to be stolen before it is tokenized. That’s why it’s essential to group tokenization together with P2PE and EMV to offer optimal security.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: (POS) systems, account number, billing, card, card breaches, card reader, cardholder, cardholder data, chip, credit card, data, DSS, EMV, EuroPay, gateway, Independent Software Vendor, ISVs, MasterCard, merchants, p2pe, payment company, payment security, payments, PCI, PINpads, point-to-point encryption, POS devices, processors, Security, security standards council, token, tokenization, transaction, visa
May 14th, 2015 by Elma Jane
The way customers Pay In Stores Is Changing.
Chip cards are here to provide advanced security with every transaction. Accepting chip cards could be as simple as changing your payment terminal.
What do you need to know about Chip Card and EMV? Chip cards are payment cards that have an embedded chip, which offers advanced security when you use the card to pay in store. Chip cards are based on a global card payment standard called EMV (Europay, MasterCard and VISA) currently used in more than 80 countries.
Why Is it More Secured? Chip card transactions offer you advanced security for in store payments by making every transaction unique, and, more difficult to counterfeit or copy. If the card data and the one-time code are stolen, the information cannot be used to create counterfeit cards and commit fraud.
How do you know if a customer has a Chip Card? The customer’s card will have chip on the front of it, magnetic stripe remains on the back.
How to use Chip Card at the POS? Swipe the card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. The customer should insert their card with chip toward terminal, facing up. The chip card should not be removed until the customer is prompted.
Customer will provide their signature or PIN as prompted by the terminal.
Some transactions may not require either.
When the terminal says the transaction is complete, the customer can remove their card.
Chip-enabled terminals will still accept magnetic stripe card payments for customers who do not have a chip card.
What does a chip-enabled terminal look like? They have all of the features you are used to with a payment terminal, with the addition of a slot for the customer to insert their card. The slot is typically located at the bottom or the top of the payment terminal.
How will you know if a terminal accepts chip card? During the transition to chip, customers are being told to swipe their card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. If you have chip-enabled terminals, you can tell your customer to insert their card for a chip transaction, if a customer has a chip card.
How can you get a chip-enabled terminal? Contact your acquirer or merchant service provider.
Show your customers that you care about their information security by making the move to chip. This will ensure that your business and your customers are protected from fraud. Start accepting chip cards!
You may be liable for fraud if you don’t make the change from chip terminal. Starting October 2015, rules are changing. Merchants that accept chip will be protected from fraud losses resulting from in store counterfeit magnetic stripe card transactions just as you are today. However, liability will shift from issuers to merchants if their payment terminals are not chip-enabled for in store transactions. Fraud liability for lost or stolen cards varies by payment network. Contact your acquirer or payment services providers for more information.
Posted in Best Practices for Merchants, Credit Card Reader Terminal, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Point of Sale Tagged with: card data, cards, chip cards, Chip-enabled terminals, data, EMV, EuroPay, magnetic stripe, MasterCard and VISA, merchant service provider, Merchant's, payment, payment cards, payment network, payment terminal, POS, Security, terminal, transaction
All merchants that accepts, transmit or stores cardholder data are required to be PCI (Payment Card Industry) Compliant. Most believe that because they do not charge the credit cards themselves, they are exempt. Why all agencies are required to be complaint even when they don’t charge credit cards themselves, and some steps to ensure your agency is PCI compliant.
What is PCI compliance?
The Payment Card Industry Data Security Standard (PCI DSS) is a set of requirements designed to ensure that all companies that process, store or transmit credit card information maintain a secure environment. PCI applies to all organizations or merchants, regardless of size or number of transactions, that accepts, transmits or stores any cardholder data. Travel agents accepting, storing and transmitting credit card information to suppliers, are required to be compliant too. Suppliers reinforce this through their travel agent guidelines/contracts. Travel Agency must adhere to the applicable credit card company’s procedures for credit card transactions.
Consequences of Not Being PCI Compliant
If an agency is not PCI compliant, the agency can lose the ability to process credit card payments with that supplier. Not being able to pay with client credit cards can be a serious roadblock for agencies, and an inconvenience for clients.
If you have a merchant account and are found to be out of compliance, you can be fined.
How to be PCI Compliant
Don’t store the CCV security code from the client’s credit card. The client does not have the authority to grant you permission to store their CCV code. The credit card company explicitly forbid storage of the CCV code.
Make sure you securely store any client information, including their credit card number and expiration date. If you use a CRM, ensure that you have a strong password. If your CRM database is stored on your computer hard drive, encrypt it (there is a great encryption software that is free of charge). If you have an IT resource, talk to them about installing a firewall on your network, installing anti-virus and anti-malware protection, and any other steps that you can take to secure your client data even further.
If you keep paper copies of client information, keep it in a locked filing cabinet or desk drawer. When you no longer need their credit card information, cross shred it.
Home based businesses are arguably the most vulnerable simply because they are usually not well protected, according to the PCI Compliance Guide. Having strong passwords, encryption, a firewall, anti-virus and anti-malware protection are all inexpensive steps that you can take to protect your business and your clients’ sensitive data.
If you receive a courtesy call reminding you about PCI Compliance, don’t ignore it.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Payment Card Industry PCI Security Tagged with: cardholder, cardholder data, cards, CCV, CCV code, credit, credit card company, credit card number, credit card payments, credit card transactions, credit cards, crm, CRM database, data, database, encryption software, merchant account, Merchant's, network, Payment Card Industry, PCI, security code, transactions, travel agents









