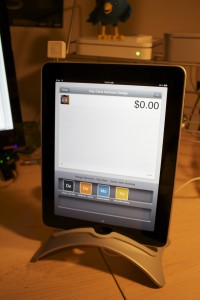
September 10th, 2014 by Elma Jane
If your businesses considering an iPad point-of-sale (POS) system, you may be up for a challenge. Not only can the plethora of providers be overwhelming, but you must also remember that not all iPad POS systems are created equal. iPad POS systems do more than process payments and complete transactions. They also offer advanced capabilities that streamline operations. For instance, they can eliminate manual data entry by integrating accounting software, customer databases and inventory counts in real time, as each transaction occurs. With these systems, you get 24/7 access to sales data without having to be in the store. The challenge, however, is knowing which provider and set of features offer the best iPad POS solution for your business. iPad POS systems vary in functionality far more than the traditional POS solutions and are often targeted at specific verticals rather than the entire market. For that reason, it’s especially important to compare features between systems to ultimately select the right system for your business.
To help you choose a provider, here are things to look for in an iPad POS system.
Backend capabilities
One of the biggest benefits of an iPad POS system is that it offers advanced features that can streamline your entire operations. These include backend processes, such as inventory tracking, data analysis and reporting, and social media integration. As a small business, two of the most important time saving and productivity-boosting features to look for are customer relationship management (CRM) capabilities and connectivity to other sales channels. You’ll want an iPad POS that has robust CRM and a customizable customer loyalty program. It should tell you which products are most and least frequently purchased by specific customers at various store locations. It should also be able to identify the frequent VIP shoppers from the less frequent ones at any one of your store locations, creating the ultimate customer loyalty program for the small business owner. If you own an online store or use a mobile app to sell your products and services, your iPad POS software should also be able to integrate those online platforms with in-store sales. Not only will this provide an automated, centralized sales database, but it can also help increase total sales. You should be able to sell effortlessly through online, mobile and in-store channels. Why should your customers be limited to the people who walk by your store? Your iPad POS should be able to help you sell your products through more channels, online and on mobile. E-commerce and mobile commerce (mCommerce) aren’t just for big box retailers.
Cloud-based
The functions of an iPad POS solution don’t necessarily have to stop in-store. If you want to have anytime, anywhere access to your POS system, you can use one of the many providers with advanced features that give business owners visibility over their stores, its records and backend processes using the cloud. The best tablet-based POS systems operate on a cloud and allow you to operate it from any location you want. An iPad POS provider, with a cloud-based iPad POS system, businesses can keep tabs on stores in real time using any device, as well as automatically back up data. This gives business owners access to the system on their desktops, tablets or smartphones, even when not inside their stores. Using a cloud-based system also protects all the data that’s stored in your point of sale so you don’t have to worry about losing your data or, even worse, getting it stolen. Because the cloud plays such a significant role, businesses should also look into the kind of cloud service an iPad POS provider uses. In other words, is the system a cloud solution capable of expanding, or is it an app on the iPad that is not dependent on the Internet? Who is the cloud vendor? Is it a premium vendor? The type of cloud a provider uses can give you an idea about its reliability and the functions the provider will offer.
Downtime and technical support
As a small business, you need an iPad POS provider that has your back when something goes wrong. There are two types of customer support to look for: Downtime support and technical support.
iPad POS systems are often cheaper and simpler than traditional systems, but that doesn’t mean you can ignore the product support needs. The POS is a key element of your business and any downtime will likely result in significant revenue loss. You could, for instance, experience costly downtime when you lose Internet connectivity. iPad POS systems primarily rely on the Web to perform their core functions, but this doesn’t mean that when the Internet goes down, your business has to go down, too. Many providers offer offline support to keep your business going, such as Always on Mode. The Always on Mode setting enables your business to continue running even in the event of an Internet outage. Otherwise, your business will lose money during a loss of connectivity. Downtime can also happen due to technical problems within the hardware or software. Most iPad POS providers boast of providing excellent tech support, but you never really know what type of customer service you’ll actually receive until a problem occurs.
Test the friendliness of customer service reps by calling or emailing the provider with questions and concerns before signing any contracts. This way, you can see how helpful their responses are before you purchase their solution. Your POS is the most important device in your store. It’s essentially the gateway to all your transactions, customer data and inventory. If anything happens to it, you’ll need to be comfortable knowing that someone is there to answer your questions and guide you through everything.
Grows with your business
All growing businesses need tech solutions that can grow right along with them. Not all iPad POS systems are scalable, so look for a provider that makes it easy to add on more terminals and employees as your business expands. Pay attention to how the software handles growth in sales and in personnel. As a business grows, so does it sales volume and the required software capabilities. Some iPad POS solutions are designed for very small businesses, offering very limited features and transactions. If you have plans for growth, look for a provider that can handle the changes in transactions your business will be going through. Find out about features and customization. Does the system do what you want it to do? Can it handle large volume? How much volume? What modules can you add, and how do you interface to third parties? You should also consider the impacts of physical expansion and adding on new equipment and employees. If there are plans in the future for you to open another store location, you’ll need to make sure that your point of sale has the capabilities of actually handling another store location without adding more work for you. If you plan on hiring more employees for your store, you’ll also want to know that the solution you choose can easily be learned, so onboarding new staff won’t take up too much of your time.
Security
POS cyber attacks have risen dramatically over the past couple of years, making it more critical than ever to protect your business. Otherwise, it’s not just your business information at risk, but also your reputation and entire operations. iPad POS system security is a bit tricky, however. Unlike credit card swipers and mobile credit card readers that have long-established security standards namely, Payment Card Industry (PCI) compliance — the criteria for the iPad hardware itself as a POS terminal aren’t quite so clear-cut. Since iPads cannot be certified as PCI compliant, merchants must utilize a point-to-point encryption system that leaves the iPad out of scope. This means treating the iPad as its own system, which includes making sure it doesn’t save credit-card information or sensitive data on the iPad itself. To stay protected, look for PCI-certified, encrypted card swipers.
Posted in Best Practices for Merchants, Mobile Point of Sale, Point of Sale Tagged with: (POS) systems, accounting, app, business, card, cloud-based, credit, credit card readers, credit-card, crm, customer, customer relationship management, customer support, data, data analysis, database, desktops, e-commerce, inventory, iPad Point-Of-Sale, loyalty program, mcommerce, mobile, mobile app, mobile commerce, online, online platforms, Payment Card Industry, payments, PCI, platforms, POS, POS solution, products, sales, Security, security standards, services, Smartphones, social media, software, tablets, terminal, transactions, web
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services
September 4th, 2014 by Elma Jane
EMV, which stands for Europay, MasterCard and Visa, and is slated to be mandated across the United States starting in October 2015 and automated fuel dispensers have until October 2017 to comply. Unlike magnetic swipe cards, EMV chip cards encrypt data and authenticate communication between the card and card reader. Additionally, chip card user is prompted for a PIN for authentication.
Why are those dates important? Companies lose $5.33 billion to fraud today, with card issuers and merchants incurring 63 and 37 percent of these losses, respectively. Under the EMV mandate, merchants who do not process chip cards will bear the burden of the issuer loss. By accepting chip card transactions, merchants and issuers should see a reduction in fraud.
Overcoming Barriers to EMV Adoption
Given the significant barriers to EMV adoption, it may be tempting for merchants to meet minimum requirements for accepting EMV payments. However, medium to large retailers should also consider the bigger picture of customer security and peace of mind.
Some key critical success factors for a payment initiative of this size include:
Business Continuity Architecture: As with all payment systems, it is imperative to have the EMV system running at all times. The solution should preferably have Active-Active architecture across multiple data centers and have a low Recovery Point Objective (the point in time to which the systems and data must be recovered after an outage).
Cost Benefit Analysis: Take a top down approach and decide accordingly on the scope of the analysis. This will ensure that decisions on scope are made on basis of quantitative data and not just qualitative arguments.
Phased Approach: To overcome time or cost overage in a project of this scope and complexity, retailers should try using an iterative approach for development. The rollout can be divided into multiple releases of six to seven months, which will provide the opportunity to review, capture lessons learnt, and improve subsequent releases.
Proactive Monitoring Alerts: Considering the criticality of business function carried out by EMV, tokenization and payment gateway, a vigorous supervising environment must be defined to perform proactive and reactive monitoring. It should take into consideration the monitoring targets, tools, scope and methods. This will provide advance visibility to the failure points and better ensuring maximum system availability.
Resilience Testing: Typically in a software project, the testing is limited to the unit, integration, performance and user acceptance. However, due to the critical nature of the applications and systems involved, robust resiliency testing is vital. This will ensure that there are no single points of failure and the system remains available when running in error conditions.
Stakeholder Identification: This is a key step to ensure that you have varied perspectives from all departments and their support. It will keep your organization from being blindsided and reduce the risk of disagreements in later stages of the program. Key stakeholders should include Store Operations, Card Accounting, Loss Prevention, Contact Center and IT & Data Security.
Organizations should adopt a five step approach to implement a secure, robust and industry-leading payment solution:
Encryption – Point to point encryption will ensure card data is secure and encrypted from the point of capture to the processor. Usually, merchants use data encryption that is not point to point, rendering their organization vulnerable to data breaches. Software encryption is the most common form of encryption, as it is easily installed and quires little or no hardware upgrades; however, it is less secure, may expose encryption keys, and is prone to memory scanning attacks. Hardware encryption is considered more secure but requires more costly terminal upgrades. Hardware encryption is designed to self-destruct the keys if tampered, but is not well-defined as very limited headway has been made in this space.
Tokenization – Build a Card Data Environment (CDE) that will host a centralized card data storage solution. Only limited applications with firewall access and capability to mutually authenticate via certificates can access CDE and receive card data. The rest of the applications will have tokens which are random numbers. This architecture will ease the merchant’s burden with existing and emerging PCI Data Security Standards.
Payment Gateway – Perform a risk assessment on the current payment gateway and identify gaps in functionality, manageability, compliance, scalability, speed to market and best practices. Determine the alternatives to mitigate the risks. Some of the important aspects of a leading payment gateway solution are support for all forms of credit, debit, gift cards and check transactions. Its ability to work with any acquirer, in-built encryption abilities, support for settlement and reconciliation must also be kept into consideration.
Settlement, Funding and Reconciliation – A workflow-based system to handle chargebacks and the automation of chargeback processing will greatly reduce labor-intensive work and enhance the quality of data used for settlement and reconciliation. Upgrades to the existing receipt retrieval system may be needed.
Card fraud is on the rise in the U.S., and merchants are the primary target for stealing information. With the EMV deadline just over a year away, the responsible retailer must take steps to prepare now. Although EMV implementation might seem overwhelming to merchants, they should start their journey to secure payments rather than wait for a looming deadline. Solutions such as data encryption and tokenization should be used in combination with EMV to implement a robust payment solution to better protect merchants against fraud. By proactively adopting EMV payment solutions, merchants can stay ahead of the regulatory curve and better protect their customers from fraud.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: authentication, automation, card, card data, Card Data Environment, card fraud, card issuers, card transactions, CDE, chargeback, chargeback processing, check, check transactions, chip, chip cards, credit, customer, customer security, data, data breaches, data encryption, data security, debit, EMV, emv chip cards, EuroPay, fraud, gateway, Gift Cards, host, integration, magnetic swipe cards, MasterCard, Merchant's, payment, payment gateway, payment solution, payment systems, PCI, PCI Data Security Standards, PIN, processor, retailers, Security, software, swipe, terminal, tokenization, tools, visa
August 19th, 2014 by Elma Jane
In response to the third-party threat, the PCI Security Standards Council has published a guide to help organizations and their business partners reduce risk by better understanding their respective roles in securing card data.
The Third-Party Security Assurance Information Supplement provides guidance practical recommendations to help businesses and their partners protect data, including:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: card, card data, consumers, data, Merchant's, payment, PCI, Service providers
May 8th, 2014 by Elma Jane
The complexity derives from PCI’s Data Security Standards (DSS), which include up to 13 requirements that specify the framework for a secure payment environment for companies that process, store or transmit credit card transactions.
Make PCI DSS Assessment Easier
Training and educating employees. Technical employees should obtain any certifications or training classes necessary so that they can operate and monitor the security control set in place. Non-technical employees must be trained on general security awareness practices such as password protection, spotting phishing attacks and recognizing social engineering. All the security controls and policies in the world will provide no protection if employees do not know how to operate the tools in a secure manner. Likewise, the strongest 42-character password with special characters, numbers, mixed case, etc. is utterly broken if an employee writes it on a sticky note attached to their monitor.
For an organization to effectively manage its own risk, it must complete a detailed risk analysis on its own environment. Risk analysis goal is to determine the threats and vulnerabilities to services performed and assets for the organization. As part of a risk assessment, organization should define critical assets including hardware, software, and sensitive information and then determine risk levels for those components. This in turn allows the organization to determine priorities for reducing risk. It is important to note that risks should be prioritized for systems that will be in-scope for PCI DSS and then other company systems and networks.
Once the risk assessment has been completed the organization should have a much clearer view of its security threats and risks and can begin determining the security posture of the organization. Policies and procedures form the foundation of any security program and comprise a large percentage of the PCI DSS requirements. Business leaders and department heads should be armed with the PCI DSS requirements and the results of the risk analysis to establish detailed security policies and procedures that address the requirements but are tailored to business processes and security controls within the organization.
Building upon the foundation of security policies, the committee of business leaders and department heads should now review the PCI DSS requirements in detail and discuss any potential compliance gaps and establish a remediation plan for closing those gaps. This is where it is important to have the full support of business leaders who can authorize necessary funds and manpower to implement any remediation activities.
This is also the time to schedule the required annual penetration testing. These are typically performed by third parties, but is not required to be performed by third parties, and can take some time to schedule, perform, and remediate (if necessary). The results of a PCI DSS assessment will be delayed until the penetration test is completed so now is the time to schedule the test.
At this point the organization is ready for a full-scale PCI DSS assessment and can now enter a maintenance mode where periodic internal audits occur and regular committee meetings are held to perform risk assessments and update policies, procedures, and security controls as necessary to respond to an ever changing threat landscape. PCI DSS must become integrated into the everyday operation of the organization so that the organization remains secure and to ease the burden of the annual assessments.
Payment Card Industry (PCI) compliance assessment is a major task for any size organization, but you can make it easier.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: assets, card, card transactions, compliance, compliance assessment, credit card transactions, credit-card, data security standards, DSS, networks, password protection, payment, Payment Card Industry, PCI, Phishing, process, risk, risk analysis, risk assessment, secure payment, Security, security control, security policy, transactions, transmit
May 6th, 2014 by Elma Jane
Boston-based Loop has released its LoopWallet app for storing magnetic-stripe cards on smartphones and using them in contactless payments at regular POS terminals.
Loop is a Level One PCI certified payment provider. Its technology has applications for turning loyalty cards into contactless cards and can also be used to generate dynamic card data every time a payment is made, preventing the creation of cloned cards.
The Loop Fob contains a microprocessor and magnetic induction loop and can be used without a phone, in which case payment would be taken from a designated card.
Mag-stripe cards for payment, gift, loyalty, ID or membership are read by the Loop Fob, a small audio jack magnetic-stripe reader, and then card data is encrypted and stored on the user’s smartphone. The LoopWallet app allows users to view their cards and select the one they wish to use.
To make a payment at the point of sale, the phone sends a signal, using Loop’s Magnetic Secure Transmission technology. MST emulates the signal generated when a mag-stripe card is swiped across a POS terminal’s read head. The signal is received by any mag-stripe card reader without requiring modifications to the POS terminal or processing system.
The free LoopWallet App for iOS 7 is available in the Apple App Store, with an Android version planned for release in April 2014. The app is only available to U.S. consumers.
.
Posted in Best Practices for Merchants, Credit card Processing, Digital Wallet Privacy, Electronic Payments, EMV EuroPay MasterCard Visa Tagged with: contactless, mag-stripe readers, magnetic stripe, mobile wallet, PCI
May 5th, 2014 by Elma Jane
The Payment Card Industry (PCI) Data Security Standard (DSS) has come under criticism as high profile data breaches continue to expose flaws in retailers’ data security systems. But telecommunications firm Verizon Wireless concluded that the PCI DSS is working.
Some Responses to Criticisms
Nilson Report research from August 2013 that said card fraud cost the global payments market over $11 billion in 2012. Verizon added that the frequency of fraud schemes that the PCI DSS was designed to avoid is in fact growing. And yet most businesses are not fully compliant at the time of assessment. Only 51.1 percent of the companies it had audited had passed seven of the 12 requirements of the PCI DSS and only 11.1 percent of said companies had passed all 12.
Verizon addressed some of the criticisms leveled at the PCI DSS. One concern is that the standard promotes compliance as a test to be passed and forgotten, which distracts companies from focusing on improving security. Verizon responded by stating that breached businesses were less likely to be PCI DSS compliant than unaffected companies. It also said businesses improve their chances of not being breached by having the standard in place, and of minimizing the damage of a breach should one occur.
Another common complaint leveled at the standard is that it is too cumbersome and slow moving in relation to the quickly evolving threat landscape and nimble fraudsters ready to try new tactics. Verizon countered that the PCI DSS is meant to be a set of baseline security protocols. Achieving compliance with any standard is simply not enough, organizations must take responsibility for protecting both their reputation and their customers. Most attacks on networks are of the simple variety, with 78 percent of hacking techniques considered low or very low in sophistication. Data Breach Investigations Report (DBIR) research shows that while perpetrators are upping the ante, trying new techniques and leveraging far greater resources, less than 1 percent of the breaches use tactics rated as high on the VERIS (Verizon’s Data breach Analysis Database) difficulty scale for initial compromise.
Recommendations
There’s an initial dip in compliance whenever a major update to the standard is released, so organizations will have to put in additional effort to prepare for achieving compliance with DSS 3.0.
The newest version of the standard, PCI DSS 3.0, went into effect Jan. 1, 2014. Businesses have until Jan. 1, 2015, to implement it. The updated standard has new requirements and clarifications to version 2.0 that will take time for businesses to understand and implement, and this will result in more organizations being out of compliance.
To help businesses deal with their PCI DSS compliance obligations the firm offered five approaches:
Don’t leave compliance to information technology security teams, but enlist application developers, system administrators, executives and other staff in helping further along the process.
Embed compliance in everyday business practices so that it is sustainable.
Integrate compliance programs into enterprise-wide governance, risk and compliance strategies.
Learn how to reduce the scope of organizations’ compliance responsibilities, chiefly by figuring out how to store less data on fewer systems.
Think of compliance as an opportunity to improve overall business processes, rather than as a burden.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, Electronic Payments, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: attacks on networks, Breach, breached, business processes, compliance, compliant, data breach investigators, data breaches, data security systems, database, DSS, fraud schemes, global payments, hacking, information technology, Payment Card Industry, PCI, retailers, Security, security protocols, standard, system administrators, wireless
April 11th, 2014 by Elma Jane
PCI DSS 3.0 standard, which took effect January 1st, introduces changes that extend across all 12 requirements, aimed to improve security of payment card data and reducing fraud. There will be some shakeups for many organizations when it comes to their day-to-day culture and operations. Transitioning to meet the new requirements will help e-business build a stronger, safer, lower-risk environment for their customers.
While the growing number of digital payment avenues offers convenience to customers, it also offers a larger attack surface for criminals.
As cloud technologies and e-commerce environments continue to grow, creating multiple points of access to cardholder data and online retailers will only become more appealing targets for hackers. Cybercriminals are cunning and determined. They understand payment card infrastructures as well as the engineers who designed them.
A scary proposition and it’s exactly why the payment card industry is so determined to help keep e-commerce organizations protected. Meeting the new standard, businesses will be better armed to fight evolving threats. Changes will also drive more consistency among assessors, help business reduce risk of compromise and create more transparent provider-customer relationships.
Transitioning to PCI DSS 3.0 will involve some work, but doing that work on the front end is going to save much work down the line. Adopting the new standard ultimately will drive your e-commerce business into a secure and efficient era.
Cultural Changes – One of the main themes of 3.0 is shifting from an annual compliance approach to embedding security in daily processes. Threats don’t change just once a year. They’re constantly evolving and that means e-commerce organizations must adopt a culture of vigilance. Only through a proactive business-as-usual approach to security can you achieve true DSS compliance. Realistically, this could mean the need to provide more education and build awareness with staff, partners and providers, so that everyone understands why and how new processes are in place.
Operational Changes – The 3.0 standard addresses common vulnerabilities that probably will ring a bell with many of you. These include weak passwords and authentication procedures, as well as insufficient malware detection systems and vulnerability assessments, just to name a few. Depending on your current security controls program, this could mean you’ll need to step up in these areas by strengthening credential requirements, resolving self-detection challenges, testing and documenting your cardholder data environment and making other corrections.
Overview Changes – How much work lands on your plate will depend on your current security program. Examining your current security strategies and program is a good idea. Below are the areas requiring your attention, which this series will explore in more detail in future installments.
Service Provider Changes – Some organizations made unsafe assumptions in the past when it comes to third-party providers. Some have paid the price, from failed audits to breaches. One reason that the new standard is designed to eliminate any confusion over compliance responsibilities. Responsibilities, specifically for management, operations, security and reporting all will need to be spelled out in detailed contracts. In addition to improved communication, an intensified focus on transparency means that you should have a clear view of your provider’s infrastructure, data storage and security controls, along with subcontractors that can impact your environment. So if your organization isn’t exactly clear on which PCI DSS requirements you manage and which ones your providers handle, prepare to get all of that hammered out.
The Compliance Rewards – The path to preparing for the 3.0 deadline in January 2015 sounds like it’s a lot of work. So to get started request your QSA’s opinion on how the changes will impact your organization, by doing the gap assessment and you’ll be able to address any shortcomings.
Meeting the new 3.0 requirements isn’t just about passing audits. In fast paced payment IT landscape, staying smart and protected is part of our commitment to our customers. Beefing up security game not only reduce audit headaches, but also enjoy stronger brand reputation as a safe and reliable e-commerce business.
Posted in Best Practices for Merchants, Credit card Processing, Credit Card Security, e-commerce & m-commerce, Electronic Payments, Financial Services, Payment Card Industry PCI Security, Small Business Improvement, Visa MasterCard American Express Tagged with: 3.0, attack surface, authentication, breaches, businesses, cardholder data, complance, compliant, credential, cybercriminals, digital payment, DSS, e-business, e-commerce, embedding, hackers, lower-risk, online retailers, passing audits, payment card infrastructures, PCI, processes, reducing fraud, requirements, risk of compromise, security controls, security of payment card data, security program, standards
December 5th, 2013 by Elma Jane
Three key benefits mPOS can provide PSPs. mPOS:
1. Maintains A Continuity Of Operations
mPOS solutions also ease the process of accepting and approving payments, according to the white paper. By enabling face-to-face card present transactions, mPOS allows transactions to be conducted in a highly secure manner. Further, once the encrypted transaction data is decrypted securely by the PSP at the payment gateway (with no access granted to the merchant), the onward presentation of the data into the acquiring network is consistent with that used historically for traditional POS terminals.
2. Simplifies Merchant Support
Thales suggests the biggest benefit to PSPs is that mPOS reduces the variety of costs PSPs need to cover to support merchants, cutting expenses related to equipment, security and PCI DSS compliance. This, the white paper says, allows PSPs that utilize mPOS to better allocate resources toward handling higher transaction volumes and acquiring business.
3. Supports Both Magnetic Stripe and EMV Cards
Another benefit to PSPs is that mPOS, despite its recent entrance to the market, is already widely available. The white paper explains that since the mPOS revolution quickly migrated from the U.S. abroad, mPOS solutions now exist to serve the unique needs of both markets. While this means challenges for merchants operating globally, PSPs benefit from being able to address the needs of merchants who want to opt for any and all available market solutions.
Much has been said about the recent explosion of the mobile point-of-sale (mPOS) market and how micromerchants are driving this payments revolution. But, what this story doesn’t communicate effectively is that small merchants aren’t the only stakeholders benefiting from the ongoing mPOS migration.
Payment service providers (PSPs) are another member of the mPOS value chain that can gain flexibility and security through these solutions, new research from data protection solution provider Thales suggests.
“Both merchants and PSPs have operational and logistical issues with traditional POS terminals associated mainly with the highly controlled and certified environment in which they must be used,” Thales writes in its latest white paper on the topic, “mPOS: Secure Mobile Card Acceptance.”
The 27-page white paper provides an extensive overview of the ongoing POS revolution, explaining how mPOS can reduce friction and costs for merchants, illustrating how the technology works step-by-step and highlighting the roles that each stakeholder plays along the value chain.
Posted in Electronic Payments, Mobile Payments, Mobile Point of Sale, Payment Card Industry PCI Security, Point of Sale, Smartphone Tagged with: acceptance, acquiring network, card present, compliance, decrypted, DSS, emv cards, encrypted, face-to-face, magnetic stripe, merchant, micromerchants, migration, mobile card, mobile point of sale, MPOS, payment gateway, payment service providers, payments, PCI, POS, psps, secure, securely, Security, terminals, transactions
New legislation is working its way through congress to require e-commerce retailers and mail order telephone order business to collect local sales taxes on transactions. e-commerce web sites and mail order telephone order businesses that conduct over $1 million gross sales and sell products and services in states where they don’t maintain brick and mortar presences would be required to collect and pay local and state taxes in those states. Targeting remote retailers that engage in interstate commerce the most obvious being mail order and telephone order as well as e-commerce shopping cart sites. Read more of this article »
Posted in Electronic Payments Tagged with: brick and mortar, DSS, e-commerce, electronic payment, mail order, merchant, merchant account, PCI, shopping cart, tax, taxes, telephone order