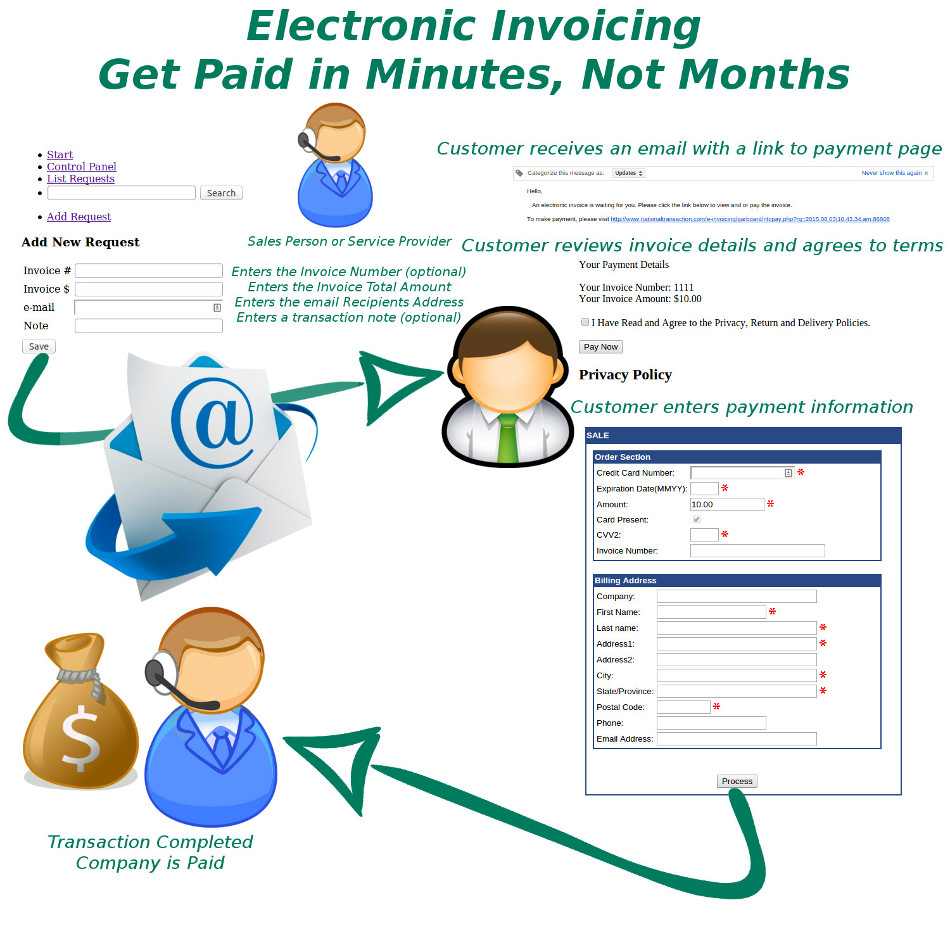
September 3rd, 2015 by Elma Jane
Today, there are numbers of dedicated invoicing software solutions to choose from, but also, specifically built to handle all aspects of invoicing. Whether you send out invoices in the mail, electronically or both. NTC’s Cloud-based invoicing software is a way to simplify your invoicing processes.
National Transaction help merchants consider making the switch to online invoicing methods.
If you’re considering making the transition, check National Transaction’s Electronic Invoice.
Once the transaction is approved a confirmation email is sent to the merchant and consumer.
Benefits of Electronic Invoicing:
Ease of use – Merchants only needs to enter the email address and the amount of sale to complete order.
Better security – Card Holder enters credit card data directly into an acquiring bank system. Bank stores such sensitive information in an encrypted format on remote servers. This reduces your liability and makes it so you won’t lose all your important data if your server gets hacked or destroyed.
Collect useful sales information – Most invoicing software has reporting capabilities which let you track payments, projected income and client history.
Get paid faster – E-Invoice can be paid the same day. The sooner you send your invoices, the sooner you are likely to get paid. With NTC Electronic Invoice, you can schedule invoices to be sent out ASAP, which means faster, more reliable income for your business.
Look more professional – Invoicing software typically includes professional-looking invoice templates, which you can customize with your business name and logo.
Emailing clients invoices instead of mailing them printed bills, is approximately 10 times cheaper than paper invoicing.
Send invoices from anywhere – Cloud-based invoicing software can be accessed from anywhere with an internet connection. This means you can easily invoice customers or access your business’s billing information wherever you are in the world, and even from your phone if you need to.
Interested in Electronic Invoicing? Give us a call 888-996-2273 or go to our website www.nationaltransaction.com
Posted in Best Practices for Merchants Tagged with: bank, card, card data, credit card, Electronic Invoice, invoicing, merchants
May 14th, 2015 by Elma Jane
The way customers Pay In Stores Is Changing.
Chip cards are here to provide advanced security with every transaction. Accepting chip cards could be as simple as changing your payment terminal.
What do you need to know about Chip Card and EMV? Chip cards are payment cards that have an embedded chip, which offers advanced security when you use the card to pay in store. Chip cards are based on a global card payment standard called EMV (Europay, MasterCard and VISA) currently used in more than 80 countries.
Why Is it More Secured? Chip card transactions offer you advanced security for in store payments by making every transaction unique, and, more difficult to counterfeit or copy. If the card data and the one-time code are stolen, the information cannot be used to create counterfeit cards and commit fraud.
How do you know if a customer has a Chip Card? The customer’s card will have chip on the front of it, magnetic stripe remains on the back.
How to use Chip Card at the POS? Swipe the card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. The customer should insert their card with chip toward terminal, facing up. The chip card should not be removed until the customer is prompted.
Customer will provide their signature or PIN as prompted by the terminal.
Some transactions may not require either.
When the terminal says the transaction is complete, the customer can remove their card.
Chip-enabled terminals will still accept magnetic stripe card payments for customers who do not have a chip card.
What does a chip-enabled terminal look like? They have all of the features you are used to with a payment terminal, with the addition of a slot for the customer to insert their card. The slot is typically located at the bottom or the top of the payment terminal.
How will you know if a terminal accepts chip card? During the transition to chip, customers are being told to swipe their card as they normally would and follow the prompts. If the terminal is chip-enabled, it will prompt them to insert it instead. If you have chip-enabled terminals, you can tell your customer to insert their card for a chip transaction, if a customer has a chip card.
How can you get a chip-enabled terminal? Contact your acquirer or merchant service provider.
Show your customers that you care about their information security by making the move to chip. This will ensure that your business and your customers are protected from fraud. Start accepting chip cards!
You may be liable for fraud if you don’t make the change from chip terminal. Starting October 2015, rules are changing. Merchants that accept chip will be protected from fraud losses resulting from in store counterfeit magnetic stripe card transactions just as you are today. However, liability will shift from issuers to merchants if their payment terminals are not chip-enabled for in store transactions. Fraud liability for lost or stolen cards varies by payment network. Contact your acquirer or payment services providers for more information.
Posted in Best Practices for Merchants, Credit Card Reader Terminal, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Point of Sale Tagged with: card data, cards, chip cards, Chip-enabled terminals, data, EMV, EuroPay, magnetic stripe, MasterCard and VISA, merchant service provider, Merchant's, payment, payment cards, payment network, payment terminal, POS, Security, terminal, transaction
September 15th, 2014 by Elma Jane
Visa has taken advantage of the hoopla surrounding Apple’s application of digital account tokens to replace card numbers for online and mobile purchasing by initiating the roll out of its Token Service to US clients.
Visa Tokens will be made available to issuing financial institutions globally, starting with US banks next month, and followed by a phased roll-out overseas beginning in 2015. The technology has been designed to support payments with mobile devices using all major mobile platforms.
More than 750 staff from across the Visa organisation globally were involved in the effort, working closely with initial launch partners – financial institutions, merchants and processors to ensure the ecosystem was ready. Today, Visa is making these services available and believe it will help transform connected devices and wearables into secure payment vehicles.
Visa Token Service replaces sensitive payment account information found on plastic cards with a digital account number or token. Because tokens do not carry a consumer’s payment account details, such as the 16-digit account number, they can be safely stored by online merchants or on mobile devices to for e-commerce and mobile payments.
The release of the service has been given added urgency by a spate of successful hacks on merchant card data stores, such as the recent plundering of card account data at Home Depot and Target.
MasterCard has its own equivalent Digital Enablement Service, which will be released outside of the US in 2015.
Posted in Best Practices for Merchants, Credit Card Security, e-commerce & m-commerce, Mobile Payments, Visa MasterCard American Express Tagged with: account details, card, card account data, card data, data, digital account, digital account number, e-commerce, financial institutions, MasterCard, merchant card data, Merchant's, mobile, Mobile Devices, Mobile Payments, mobile platforms, online merchants, payments, processors, Token Service, tokens, visa, Visa organisation, Visa Token Service, wearables
September 5th, 2014 by Elma Jane
Businesses are rapidly adopting a third-party operations model that can put payment data at risk. Today, the PCI Security Standards Council, an open global forum for the development of payment card security standards, published guidance to help organizations and their business partners reduce this risk by better understanding their respective roles in securing card data. Developed by a PCI Special Interest Group (SIG) including merchants, banks and third-party service providers, the information supplement provides recommendations for meeting PCI Data Security Standard (PCI DSS) requirement 12.8 to ensure payment data and systems entrusted to third parties are maintained in a secure and compliant manner.
Breach reports continue to highlight security vulnerabilities introduced by third parties as a leading cause of data compromise. The leading mistake organizations make when entrusting sensitive and confidential consumer information to third-party vendors is not applying the same level of rigor to information security in vendor networks as they do in their own. Per PCI DSS Requirement 12.8, if a merchant or entity shares cardholder data with a third- party service provider, certain requirements apply to ensure continued protection of this data will be enforced by such providers. The Third-Party Security Assurance Information Supplement focuses on helping organizations and their business partners achieve this by implementing a robust third-party assurance program.
Produced with the expertise and real-world experience of more than 160 organizations involved in the Special Interest Group, the guidance includes practical recommendations on how to:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
The guidance includes high-level suggestions and discussion points for clarifying how responsibilities for PCI DSS requirements may be shared between an entity and its third-party service provider, as well as a sample PCI DSS responsibility matrix that can assist in determining who will be responsible for each specific control area.
PCI Special Interest Groups are PCI community-selected and developed initiatives that provide additional guidance and clarifications or improvements to the PCI Standards and supporting programs. As part of its initial proposal, the group also made specific recommendations that were incorporated into PCI DSS requirements 12.8 and 12.9 in version 3.0 of the standard.One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: banks, Breach, card, card data, cardholder, consumer, data, data security, Merchant's, networks, payment, payment card security, payment data, payment information, PCI, PCI-DSS, provider's, Security, Security Assurance, security standards, security standards council, Service providers, services
September 4th, 2014 by Elma Jane
EMV, which stands for Europay, MasterCard and Visa, and is slated to be mandated across the United States starting in October 2015 and automated fuel dispensers have until October 2017 to comply. Unlike magnetic swipe cards, EMV chip cards encrypt data and authenticate communication between the card and card reader. Additionally, chip card user is prompted for a PIN for authentication.
Why are those dates important? Companies lose $5.33 billion to fraud today, with card issuers and merchants incurring 63 and 37 percent of these losses, respectively. Under the EMV mandate, merchants who do not process chip cards will bear the burden of the issuer loss. By accepting chip card transactions, merchants and issuers should see a reduction in fraud.
Overcoming Barriers to EMV Adoption
Given the significant barriers to EMV adoption, it may be tempting for merchants to meet minimum requirements for accepting EMV payments. However, medium to large retailers should also consider the bigger picture of customer security and peace of mind.
Some key critical success factors for a payment initiative of this size include:
Business Continuity Architecture: As with all payment systems, it is imperative to have the EMV system running at all times. The solution should preferably have Active-Active architecture across multiple data centers and have a low Recovery Point Objective (the point in time to which the systems and data must be recovered after an outage).
Cost Benefit Analysis: Take a top down approach and decide accordingly on the scope of the analysis. This will ensure that decisions on scope are made on basis of quantitative data and not just qualitative arguments.
Phased Approach: To overcome time or cost overage in a project of this scope and complexity, retailers should try using an iterative approach for development. The rollout can be divided into multiple releases of six to seven months, which will provide the opportunity to review, capture lessons learnt, and improve subsequent releases.
Proactive Monitoring Alerts: Considering the criticality of business function carried out by EMV, tokenization and payment gateway, a vigorous supervising environment must be defined to perform proactive and reactive monitoring. It should take into consideration the monitoring targets, tools, scope and methods. This will provide advance visibility to the failure points and better ensuring maximum system availability.
Resilience Testing: Typically in a software project, the testing is limited to the unit, integration, performance and user acceptance. However, due to the critical nature of the applications and systems involved, robust resiliency testing is vital. This will ensure that there are no single points of failure and the system remains available when running in error conditions.
Stakeholder Identification: This is a key step to ensure that you have varied perspectives from all departments and their support. It will keep your organization from being blindsided and reduce the risk of disagreements in later stages of the program. Key stakeholders should include Store Operations, Card Accounting, Loss Prevention, Contact Center and IT & Data Security.
Organizations should adopt a five step approach to implement a secure, robust and industry-leading payment solution:
Encryption – Point to point encryption will ensure card data is secure and encrypted from the point of capture to the processor. Usually, merchants use data encryption that is not point to point, rendering their organization vulnerable to data breaches. Software encryption is the most common form of encryption, as it is easily installed and quires little or no hardware upgrades; however, it is less secure, may expose encryption keys, and is prone to memory scanning attacks. Hardware encryption is considered more secure but requires more costly terminal upgrades. Hardware encryption is designed to self-destruct the keys if tampered, but is not well-defined as very limited headway has been made in this space.
Tokenization – Build a Card Data Environment (CDE) that will host a centralized card data storage solution. Only limited applications with firewall access and capability to mutually authenticate via certificates can access CDE and receive card data. The rest of the applications will have tokens which are random numbers. This architecture will ease the merchant’s burden with existing and emerging PCI Data Security Standards.
Payment Gateway – Perform a risk assessment on the current payment gateway and identify gaps in functionality, manageability, compliance, scalability, speed to market and best practices. Determine the alternatives to mitigate the risks. Some of the important aspects of a leading payment gateway solution are support for all forms of credit, debit, gift cards and check transactions. Its ability to work with any acquirer, in-built encryption abilities, support for settlement and reconciliation must also be kept into consideration.
Settlement, Funding and Reconciliation – A workflow-based system to handle chargebacks and the automation of chargeback processing will greatly reduce labor-intensive work and enhance the quality of data used for settlement and reconciliation. Upgrades to the existing receipt retrieval system may be needed.
Card fraud is on the rise in the U.S., and merchants are the primary target for stealing information. With the EMV deadline just over a year away, the responsible retailer must take steps to prepare now. Although EMV implementation might seem overwhelming to merchants, they should start their journey to secure payments rather than wait for a looming deadline. Solutions such as data encryption and tokenization should be used in combination with EMV to implement a robust payment solution to better protect merchants against fraud. By proactively adopting EMV payment solutions, merchants can stay ahead of the regulatory curve and better protect their customers from fraud.
Posted in Best Practices for Merchants, Credit Card Security, EMV EuroPay MasterCard Visa, Payment Card Industry PCI Security, Visa MasterCard American Express Tagged with: authentication, automation, card, card data, Card Data Environment, card fraud, card issuers, card transactions, CDE, chargeback, chargeback processing, check, check transactions, chip, chip cards, credit, customer, customer security, data, data breaches, data encryption, data security, debit, EMV, emv chip cards, EuroPay, fraud, gateway, Gift Cards, host, integration, magnetic swipe cards, MasterCard, Merchant's, payment, payment gateway, payment solution, payment systems, PCI, PCI Data Security Standards, PIN, processor, retailers, Security, software, swipe, terminal, tokenization, tools, visa
August 19th, 2014 by Elma Jane
In response to the third-party threat, the PCI Security Standards Council has published a guide to help organizations and their business partners reduce risk by better understanding their respective roles in securing card data.
The Third-Party Security Assurance Information Supplement provides guidance practical recommendations to help businesses and their partners protect data, including:
Conduct due diligence and risk assessment when engaging third party service providers to help organizations understand the services provided and how PCI DSS requirements will be met for those services.
Develop appropriate agreements, policies and procedures with third-party service providers that include considerations for the most common issues that arise in this type of relationship.
Implement an ongoing process for maintaining and managing third-party relationships throughout the lifetime of the engagement, including the development of a robust monitoring program.
Implement a consistent process for engaging third-parties that includes setting expectations, establishing a communication plan, and mapping third-party services and responsibilities to applicable PCI DSS requirements.
One of the big focus areas in PCI DSS 3.0 is security as a shared responsibility. This guidance is an excellent companion document to the standard in helping merchants and their business partners work together to protect consumers’ valuable payment information.
Posted in Best Practices for Merchants, Credit Card Security, Payment Card Industry PCI Security Tagged with: card, card data, consumers, data, Merchant's, payment, PCI, Service providers
July 21st, 2014 by Elma Jane
European authorities dismantled a Romanian-dominated cybercrime network that used a host of tactics to steal more than EUR2 million. As a direct result of the excellent cooperation and outstanding work by police officers and prosecutors from Romania, France and other European countries, a key criminal network has been successfully taken down this week.
Hundreds of police in Romania and France, backed by the European Cybercrime Centre, carried out raids on 177 addresses, interrogating 115 people and detaining 65. Those held are suspected of participating in sophisticated electronic payment crimes, using malware to take over and gain access to computers used by money transfer services all over Europe. They are also accused of stealing card data through skimming, money laundering and drug trafficking.Proceeds of the crimes were invested in different types of property, deposited in bank accounts or transferred electronically, says the EC3. Large sums of money, luxury vehicles and IT equipment were seized during the raids.
Posted in Uncategorized Tagged with: accounts, bank, bank accounts, card, card data, cybercrime, data, electronic payment, host, Malware, money transfer, network, payment
May 6th, 2014 by Elma Jane
Which fee structure works best remains unclear despite the recent high-profile data security breaches that are emphasizing the need for security measures. Acquirers charge fees – or not – based on what’s best for their business model and their security objectives
Some charge merchants that comply, others charge merchants that fail to comply and a few charge both. Some Independent Sales Organizations (ISOs) don’t charge merchants a fee for helping them comply with the Payment Card Industry data security standards (PCIS DSS).
If there is any trend, it’s that more banks are finding that some sort of funding is necessary to run a program that gets any results. That funding covers costs for security assessments and compliance assistance as well as internal resources for acquirers. When it comes to covering those costs and creating incentives for compliance, no one fee structure is ideal.
Non-compliance fees encourage merchants to comply so they can save money, but the fees may not accomplish that. Unless you charge exorbitantly, it’s not going to have the effect you want it to have, and by the time you charge that much, the merchant’s just going to move to a different ISO.
ISOs charging non-compliance fees often claim the fee revenue goes into an account designated for use in case of a breach. Non-compliance fees can also reward acquirers for doing nothing to increase compliance. You get this situation where a bank has a revenue stream. Their objective is not to increase the revenue stream but to increase compliance, when they increase compliance, the revenue stream goes down.
It is recommended to some acquirers that they consider charging merchants fees for doing things like storing card data, which could be checked with a scanning tool. Merchants that do store data or fail to run the scan would be charged a fee. That is something that could really decrease risk, because if you’re not storing card data, even if you are breached, there’s nothing to get.
Simplifying the compliance verification process, by making assessment questionnaires available on its merchant portal and by teaching merchants about PCI, will minimize the potential impact of fraud by increasing compliance, which saves the company money in the long run versus a more laissez-faire approach of fees without education and compliance tools.
It’s more important to educate the merchant, it’s the spirit and intent of PCI-DSS supported by the card associations. Visa and MasterCard support it because of the severe impact of a breach or other data compromise, not as a revenue source.
ISOs and other players in the payments chain that do not work to help merchants comply are also putting themselves at risk. Breached merchants may be unable to pay fines that come with a data compromise, potentially leaving ISOs responsible for paying them. Merchants that go out of business because of a data breach also stop providing the ISO with revenue.
Plus, when merchants ask why they’re being charged a non-compliance fee, point them to the questionnaire and explain that they’ll stop being charged as soon as they demonstrate they comply with PCI.
Posted in Best Practices for Merchants, Credit Card Security, Merchant Account Services News Articles, Payment Card Industry PCI Security Tagged with: card associations, card data, compliance, compliance fee, data, data security standards, ISOs, MasterCard, Merchant's, Payment Card Industry, portal, security breaches, visa
March 31st, 2014 by Elma Jane
A payment processor is a company often a third party appointed by a merchant to handle credit card transactions for merchant acquiring banks. They are usually broken down into two types: Back and Front-End.
Back-End Processors accept settlements from Front-End Processors and, via The Federal Reserve Bank, move the money from the issuing bank to the merchant bank.
Front-End Processors have connections to various card associations and supply authorization and settlement services to the merchant banks’ merchants. In an operation that will usually take a few seconds, the payment processor will both check the details received by forwarding them to the respective card’s issuing bank or card association for verification, and also carry out a series of anti-fraud measures against the transaction.
Additional parameters, including the card’s country of issue and its previous payment history, are also used to gauge the probability of the transaction being approved.
Once the payment processor has received confirmation that the credit card details have been verified, the information will be relayed back via the payment gateway to the merchant, who will then complete the payment transaction. If verification is denied by the card association, the payment processor will relay the information to the merchant, who will then decline the transaction.
Modern Payment Processing
Due to the many regulatory requirements levied on businesses, the modern payment processor is usually partnered with merchants through a concept known as software-as-a-service (SaaS). SaaS payment processors offer a single, regulatory-compliant electronic portal that enables a merchant to scan checks “often called remote deposit capture or RDC”, process single and recurring credit card payments (without the merchant storing the card data at the merchant site), process single and recurring ACH and cash transactions, process remittances and Web payments. These cloud-based features occur regardless of origination through the payment processor’s integrated receivables management platform. This results in cost reductions, accelerated time-to-market, and improved transaction processing quality.
Payment Processing Network Architecture
Typical network architecture for modern online payment systems is a chain of service providers, each providing unique value to the payment transaction, and each adding cost to the transaction. Merchant>Point-of-sale SaaS> Aggregator >Credit Card Network> Bank. The merchant can be a brick-and-mortar outlet or an online outlet. The Point-of-sale (POS) SaaS provider is usually a smaller company that provides customer support to the merchant and is the receiver of the merchant’s transactions. The POS provider represents the Aggregator to merchants. The POS provider transaction volumes are small compared to the Aggregator transaction volumes. The POS provider does not handle enough traffic to warrant a direct connection to the major credit card networks. The merchant also does not handle enough traffic to warrant a direct connection to the Aggregator. In this way, scope and responsibilities are divided among the various business partners to easily manage the technical issues that arise.
Transaction Processing Quality
Electronic payments are highly susceptible to fraud and abuse. Liability to merchants for misuse of credit card data creates a huge expense on merchants, if the business were to attempt mitigation on their own. One way to lower this cost and liability exposure is to segment the transaction of the sale from the payment of the amount due. Some merchants have a requirement to collect money from a customer every month. SaaS Payment Processors relieve the responsibility of the management of recurring payments from the merchant and maintain safe and secure the payment information, passing back to the merchant a payment token. Merchants use this token to actually process a charge which makes the merchant system fully PCI-compliant. Some payment processors also specialize in high-risk processing for industries that are subject to frequent chargebacks, such as adult video distribution.
Posted in Best Practices for Merchants, Credit card Processing, Electronic Check Services, Electronic Payments, Internet Payment Gateway, Merchant Services Account, Payment Card Industry PCI Security, Point of Sale, Visa MasterCard American Express Tagged with: aggregator, aggregator transaction volumes, back end, card associations, card data, chargebacks, credit card transactions, electronic portal, front end, front-end processors, issuing bank, merchant, merchant bank, network architecture, online payment systems, payment gateway, payment processing, payment processor, payment transaction, pci-compliant, point of sale, POS, SAAS
March 17th, 2014 by Elma Jane
Lots of talk has gone on since the recent spate of merchant data breaches on ways to potentially prevent hackers from gaining access to stored payment card data. Use of biometric information, such as a fingerprint, to access stored credentials is among the solutions often bandied about.
The prospects of using individuals’ biometric information for credentialing is fairly scary. Security may be what biometrics is trying to achieve, but it’s also its biggest flaw. Imagine having your fingerprint information stored at Target this holiday season, that information would now be in the hands of lots of people not intended to have access to it. Unlike a password, someone can’t change his or her fingerprint. So once someone has the print, they have it forever. So even if something is biometric based, it also has to have a lot of other security measures, and that could include GPS-based location services tied to an individual’s smartphone.
Biometrics alone won’t work. It’s very scary that that information could be stored in a way that someone could figure out how to get it. Even if encrypted, that’s a huge security concern. You can’t change your fingerprint.
Posted in Credit card Processing, Credit Card Security, Electronic Payments, Payment Card Industry PCI Security, Smartphone Tagged with: biometric, card data, credentialing, encrypted, fingerprint, gaining access, gps-based, merchant data breaches, password, prevent hackers, Security, security measures, smartphone, stored credentials










